When the headlines emphasis on breaches of large enterprises like the Optus breach, it really is easy for scaled-down firms to assume they are not a goal for hackers. Absolutely, they are not value the time or exertion?
Sadly, when it comes to cyber security, sizing doesn’t make any difference.
Assuming you might be not a focus on potential customers to lax security methods in lots of SMBs who deficiency the understanding or experience to put simple security measures in position. Handful of modest organizations prioritise cybersecurity, and hackers know it. According to Verizon, the number of smaller corporations becoming hit has climbed steadily in the last handful of a long time – 46% of cyber breaches in 2021 impacted firms with fewer than 1,000 workers.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Cyber security isn’t going to require to be hard
Securing any business won’t require to be intricate or come with a hefty value tag. Below are 7 straightforward tips to aid the lesser business enterprise secure their programs, persons and knowledge.
1 — Put in anti-virus computer software all over the place
Each individual organisation has anti-virus on their devices and devices, ideal? Sad to say, organization units these as web servers get disregarded all much too often. It is significant for SMBs to contemplate all entry factors into their network and have anti-virus deployed on each server, as nicely as on employees’ personalized devices.
Hackers will locate weak entry points to install malware, and anti-virus program can provide as a fantastic last-vacation resort backstop, but it is not a silver bullet. Via continual checking and penetration screening you can establish weaknesses and vulnerabilities ahead of hackers do, for the reason that it can be much easier to cease a burglar at the entrance doorway than when they’re in your property.
2 — Continually keep track of your perimeter
Your perimeter is uncovered to remote attacks simply because it is accessible 24/7. Hackers constantly scan the internet hunting for weaknesses, so you ought to scan your very own perimeter way too. The for a longer period a vulnerability goes unfixed, the more probably an attack is to manifest. With applications like Autosploit and Shodan commonly readily available, it truly is easier than at any time for attackers to find internet dealing with weaknesses and exploit them.
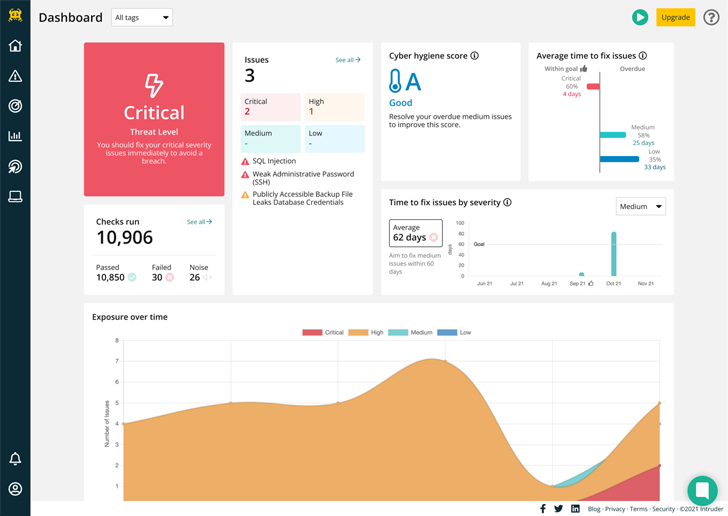
Even organisations that simply cannot pay for a comprehensive-time, in-house security specialist can use on the web products and services like Intruder to operate vulnerability scans to uncover weaknesses.
Intruder is a strong vulnerability scanner that supplies a continual security assessment of your devices. With above 11,000 security checks, Intruder helps make enterprise-grade scanning uncomplicated and available to SMBs.
Intruder will immediately identify large-impact flaws, modifications in the attack surface area, and fast scan your infrastructure for emerging threats.
3 — Minimise your attack floor
Your attack surface is produced up of all the programs and providers exposed to the internet. The greater the attack area, the even larger the risk. This signifies exposed companies like Microsoft Exchange for email, or content administration systems like WordPress can be susceptible to brute-forcing or credential-stuffing, and new vulnerabilities are uncovered nearly each day in these application units. By removing community entry to delicate devices and interfaces which you should not need to be accessible to the public, and making certain 2FA is enabled exactly where they do, you can limit your exposure and considerably cut down risk.
A very simple first phase in lessening your attack floor is by applying a protected virtual private network (VPN). By making use of a VPN, you can stay away from exposing delicate methods immediately to the internet whilst preserving their availability to workers performing remotely. When it arrives to risk, avoidance is superior than treatment – will not expose nearly anything to the internet except it truly is certainly necessary!
4 — Keep application up to day
New vulnerabilities are uncovered each day in all varieties of program, from web browsers to enterprise programs. Just one particular unpatched weak spot could direct to entire compromise of a system and a breach of buyer details as TalkTalk identified when 150,000 of its private facts records were stolen.
According to a Cyber Security Breaches Survey, enterprises that maintain digital own info of their buyers are additional probable than common to have had breaches. Patch administration is an critical component of excellent cyber hygiene, and there are equipment and companies to enable you check your computer software for any lacking security patches.
5 — Back again up your details
Ransomware is on the improve. In 2021, 37% of businesses and organisations were being strike by ransomware in accordance to study by Sophos. Ransomware encrypts any details it can entry, rendering it unusable, and won’t be able to be reversed devoid of a important to decrypt the details.
Info reduction is a key risk to any small business either via destructive intent or a technical mishap these as hard disk failure, so backing up info is generally recommended. If you back up your facts, you can counter attackers by recovering your data without the need of needing to shell out the ransom, as units impacted by ransomware can be wiped and restored from an unaffected backup without the need of the attacker’s critical.
6 — Preserve your team security knowledgeable
Cyber attackers frequently depend on human mistake, so it is crucial that staff members are trained in cyber cleanliness so they recognise threats and react correctly. The Cyber Security Breaches Survey 2022 discovered that the most common kinds of breaches ended up team receiving fraudulent emails or phishing attacks (73%), adopted by men and women impersonating the organisation in email messages or on line (27%), viruses, spyware and malware (12%), and ransomware (4%).
Increasing consciousness of the benefits of utilizing elaborate passwords and training workers to spot popular attacks these kinds of as phishing e-mails and malicious one-way links, will ensure your people today are a energy relatively than a vulnerability.
7 — Safeguard by yourself relative to your risk
Cyber security actions ought to always be suitable to the organisation. For illustration, a compact small business which handles banking transactions or has entry to sensitive data this kind of as health care knowledge really should use far a lot more stringent security procedures and procedures than a pet shop.
Which is not to say a pet store isn’t going to have a responsibility to shield consumer details, but it’s much less very likely to be a focus on. Hackers are inspired by revenue, so the even larger the prize the far more time and effort will be invested to realize their gains. By pinpointing your threats and vulnerabilities with a device like Intruder, you can consider ideal actions to mitigate and prioritize which dangers want to be tackled and in which get.
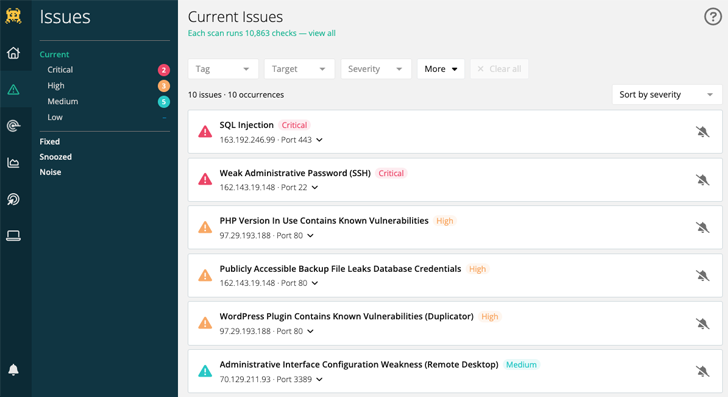
It is really time to raise your cyber security match
Attacks on significant businesses dominate the information, which feeds the perception that SMBs are harmless, when the opposite is real. Attacks are significantly automated, so SMBs are just as susceptible targets as larger sized enterprises, much more so if they will not have adequate security processes in put. And hackers will constantly adhere to the route of least resistance. Fortunately, that is the component Intruder manufactured easy…
About Intruder
Intruder is a cyber security enterprise that can help organisations cut down their attack surface by delivering ongoing vulnerability scanning and penetration screening products and services. Intruder’s effective scanner is intended to immediately identify significant-affect flaws, modifications in the attack area, and fast scan the infrastructure for rising threats. Running 1000’s of checks, which contain figuring out misconfigurations, lacking patches, and web layer issues, Intruder will make enterprise-grade vulnerability scanning easy and available to anyone. Intruder’s higher-top quality studies are perfect to move on to possible buyers or comply with security rules, this sort of as ISO 27001 and SOC 2.
Intruder gives a 14-working day totally free trial of its vulnerability evaluation system. Stop by their web-site these days to acquire it for a spin!
Identified this report appealing? Abide by THN on Facebook, Twitter and LinkedIn to read through much more distinctive content we put up.
Some components of this article are sourced from:
thehackernews.com


 Ireland’s DPC Fines Meta €265m Following Large-Scale Data Leak
Ireland’s DPC Fines Meta €265m Following Large-Scale Data Leak