SaaS applications are the spine of modern organizations, constituting a staggering 70% of total computer software utilization. Applications like Box, Google Office, and Microsoft 365 are integral to day-to-day operations. This popular adoption has transformed them into probable breeding grounds for cyber threats. Every SaaS application provides exceptional security troubles, and the landscape frequently evolves as suppliers greatly enhance their security options. Additionally, the dynamic nature of consumer governance, which includes onboarding, deprovisioning, and part adjustments, even more complicates the security equation.
With wonderful convenience arrives terrific accountability, as securing these SaaS applications has come to be a leading priority for Main Information and facts Security Officers (CISOs) and IT groups all over the world.
Effectively securing SaaS purposes necessitates a delicate equilibrium amongst strong security measures and enabling buyers to carry out their duties successfully. To navigate this intricate terrain, this report excerpts a stage-by-phase tutorial to create a strong SaaS security system – from setting up to execution and overall performance measurement.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Map Your Applications and Security Necessities
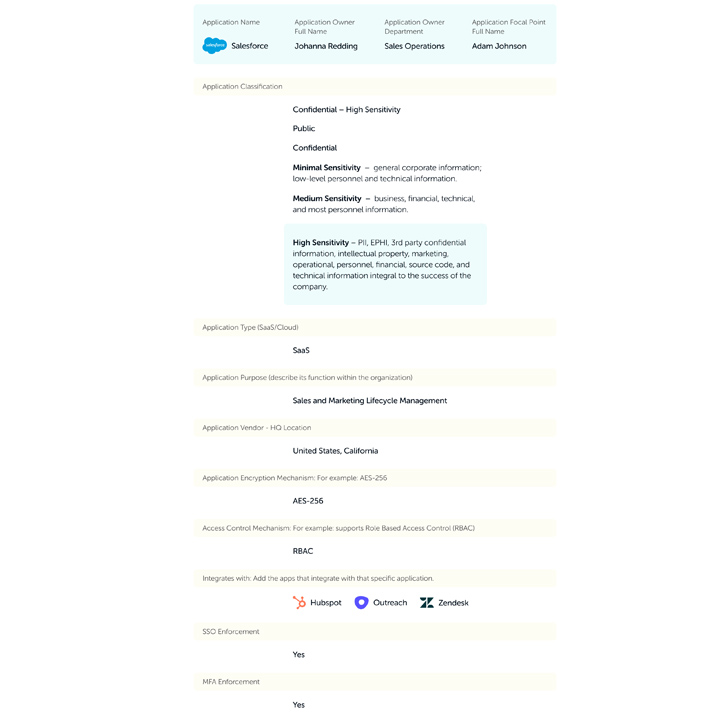
In advance of embarking on a SaaS security journey, it can be very important to realize your organization’s particular landscape and security requires. Even though purposes like Salesforce and Microsoft 365 may well include extra critical data, even scaled-down, niche apps utilized by numerous teams can retailer delicate info that must be shielded.
Take into account the regulatory and compliance specifications applicable to your company. Industries this kind of as finance adhere to SOX, though healthcare corporations need to comply with HIPAA. Comprehension your regulatory natural environment is critical for shaping your security strategy.
Also, prioritize person accessibility and facts privacy. Employing the basic principle of minimum privilege (POLP) makes certain buyers have entry only to the information essential for their roles, lessening the risk of facts breaches and unauthorized obtain. If your applications cope with personally identifiable information (PII), assure your security application aligns with privacy laws.
In this article is some standard information you must acquire for every application:
To read through the complete Kickstarting Your SaaS Security System tutorial, simply click listed here.
Map Your Present Security Ecosystem and How You Plan to Integrate SaaS Security Resources and Procedures
To be most effective, your SaaS security program must integrate tightly into the current infrastructure. It ought to join with the organization’s Identification Service provider (IdP) for effective user governance and your one indicator-on (SSO) provider to make it a lot more difficult for unauthorized users to accessibility the SaaS stack. These integrations boost the security of your apps and make it a lot easier for security professionals to do their occupation.
It is really also essential to integrate your SaaS security tools with existing SOC, SIEM, and SOAR instruments. The SOC group can examine alerts and immediately make a willpower as to the mitigation essential. Meanwhile, SIEM can take care of events though SOAR can orchestrate remediations, deprovision people, and automate a lot of of the mitigations needed to secure the SaaS stack.
Detect Stakeholders and Define Obligations
SaaS security is a collaborative work involving numerous stakeholders. Company models deal with SaaS programs with a concentration on productivity, while the security team’s priority is info protection. Bridging the hole involving these groups and deciphering the one of a kind language of each SaaS application’s settings is tough.
Successful SaaS security needs collaboration and compromise among these get-togethers to mitigate pitfalls without the need of hindering productiveness.
Determine Short-Phrase and Lengthy-Phrase Ambitions
Producing a effective SaaS security application requires crystal clear goals and key general performance indicators (KPIs) to measure development. Get started with a pilot software concentrated on critical purposes managed by different departments. Establish a timeline for the pilot, normally around three months, and established reasonable enhancement plans.
A posture rating, measured on a scale of -100%, can aid gauge security performance. Intention to manage a rating above 80% at the conclusion of a three-thirty day period pilot software and goal a very long-term rating of 90-100%.
Boost Your First Security Posture
Start by securing large-risk, very low-contact things in collaboration with app homeowners. Shut communication is crucial to comprehending the impression of security modifications on workflows and processes. Deal with superior-risk security checks impacting a tiny number of staff members very first. Utilize Security Posture Administration solutions to manual remediation efforts dependent on software, security domain, or severity.
Some companies pick to enhance posture a single software at a time. Other people boost posture by domain throughout many applications, though still other folks pick out to remediate issues by severity no matter of the software. Whichever design you choose, it is critical to establish a process to support you transfer systematically through your purposes.
Plan Ongoing Verify-In Conferences to Keep and Maintain Boosting Your Posture
Recurrent conferences with stakeholders involved in remediation are important, specifically throughout the pilot phase. As the posture stabilizes, modify the frequency of these meetings to be certain sustained security.
Carry on onboarding and checking supplemental applications to greatly enhance the security posture of your total SaaS stack.
Adopt a Rigorous Identification & Obtain Governance Policy
Embrace the principle of minimum privilege (POLP) to limit consumer entry to necessary resources and information. Deprovision end users who no longer require accessibility to limit dangers associated with active accounts. Often monitor external end users, specially all those with admin legal rights, to safeguard application details.
By adhering to these principles and pursuing a structured approach, businesses can create a sturdy SaaS security software. Remember, SaaS security is an ongoing system, and constant adaptation and advancement are critical to keeping in advance of evolving threats in the electronic landscape.
Study how to streamline and automate securing your SaaS stack.
Observed this posting intriguing? Adhere to us on Twitter and LinkedIn to examine more exceptional content material we write-up.
Some areas of this report are sourced from:
thehackernews.com


 Chinese Redfly Group Compromised a Nation’s Critical Grid in 6-Month ShadowPad Campaign
Chinese Redfly Group Compromised a Nation’s Critical Grid in 6-Month ShadowPad Campaign