The U.S. Cybersecurity and Infrastructure Security Company (CISA) has added a critical security vulnerability impacting Microsoft SharePoint Server to its Identified Exploited Vulnerabilities (KEV) catalog, citing proof of active exploitation.
The issue, tracked as CVE-2023-29357 (CVSS rating: 9.8), is a privilege escalation flaw that could be exploited by an attacker to acquire administrator privileges. Microsoft introduced patches for the bug as aspect of its June 2023 Patch Tuesday updates.
“An attacker who has obtained access to spoofed JWT authentication tokens can use them to execute a network attack which bypasses authentication and enables them to get obtain to the privileges of an authenticated consumer,” Redmond claimed. “The attacker desires no privileges nor does the person need to carry out any motion.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
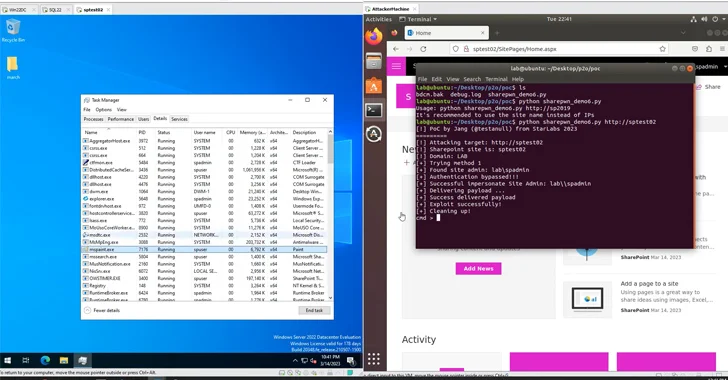
Security researcher Nguyễn Tiến Giang (Jang) of StarLabs SG shown an exploit for the flaw at the Pwn2Own Vancouver hacking contest, earning a $100,000 prize.

The pre-authenticated remote code execution chain combines authentication bypass (CVE-2023–29357) with a code injection bug (CVE-2023-24955, CVSS rating: 7.2), the latter of which was patched by Microsoft in May perhaps 2023.
“The approach of finding and crafting the exploit chain eaten virtually a yr of meticulous effort and hard work and analysis to finish the whole exploit chain,” Tiến Giang famous in a specialized report printed in September 2023.
More particulars of the genuine-environment exploitation of CVE-2023–29357 and the id of the danger actors that may be abusing them are presently not known. That mentioned, federal organizations are advised to utilize the patches by January 31, 2024, to secure from the lively threat.
Located this write-up intriguing? Comply with us on Twitter and LinkedIn to read additional special articles we post.
Some parts of this post are sourced from:
thehackernews.com

 Threat Actors Increasingly Abusing GitHub for Malicious Purposes
Threat Actors Increasingly Abusing GitHub for Malicious Purposes