Ambitious Employees Tout New AI Resources, Disregard Severe SaaS Security Hazards
Like the SaaS shadow IT of the past, AI is inserting CISOs and cybersecurity teams in a challenging but common place.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Employees are covertly making use of AI with little regard for proven IT and cybersecurity evaluation procedures. Looking at ChatGPT’s meteoric increase to 100 million end users in 60 times of launch, particularly with small revenue and marketing and advertising fanfare, personnel-pushed desire for AI instruments will only escalate.
As new scientific studies clearly show some staff raise productivity by 40% utilizing generative AI, the force for CISOs and their teams to fastrack AI adoption — and flip a blind eye to unsanctioned AI resource use — is intensifying.
But succumbing to these pressures can introduce really serious SaaS info leakage and breach challenges, specifically as personnel flock to AI instruments formulated by modest businesses, solopreneurs, and indie builders.
AI Security GuideDownload AppOmni’s CISO Tutorial to AI Security – Aspect 1
AI evokes inspiration, confusion, and skepticism — specifically amid CISOs. AppOmni’s latest CISO Manual examines widespread misconceptions about AI security, giving you a well balanced standpoint on present day most polarizing IT subject.
Get It Now
Indie AI Startups Normally Absence the Security Rigor of Company AI
Indie AI applications now range in the tens of 1000’s, and they’re productively luring staff with their freemium designs and solution-led progress promoting system. According to leading offensive security engineer and AI researcher Joseph Thacker, indie AI application builders utilize significantly less security staff members and security target, a lot less authorized oversight, and fewer compliance.
Thacker breaks down indie AI software risks into the adhering to types:
- Data leakage: AI instruments, specifically generative AI employing huge language products (LLMs), have wide entry to the prompts employees enter. Even ChatGPT chat histories have been leaked, and most indie AI tools aren’t operating with the security standards that OpenAI (the parent organization of ChatGPT) implement. Practically every indie AI instrument retains prompts for “teaching facts or debugging uses,” leaving that details vulnerable to exposure.
- Material high quality issues: LLMs are suspect to hallucinations, which IBM defines as the phenomena when LLMS “perceives patterns or objects that are nonexistent or imperceptible to human observers, generating outputs that are nonsensical or entirely inaccurate.” If your business hopes to depend on an LLM for content material technology or optimization without having human reviews and actuality-checking protocols in area, the odds of inaccurate information getting published are substantial. Further than articles creation precision pitfalls, a developing range of teams these types of as academics and science journal editors have voiced ethical issues about disclosing AI authorship.
- Product vulnerabilities: In common, the more compact the business constructing the AI resource, the extra most likely the developers will fail to tackle popular merchandise vulnerabilities. For instance, indie AI instruments can be a lot more vulnerable to prompt injection, and standard vulnerabilities these kinds of as SSRF, IDOR, and XSS.
- Compliance risk: Indie AI’s absence of mature privacy procedures and inside restrictions can lead to stiff fines and penalties for non-compliance issues. Employers in industries or geographies with tighter SaaS facts rules this kind of as SOX, ISO 27001, NIST CSF, NIST 800-53, and APRA CPS 234 could uncover them selves in violation when employees use equipment that do not abide by these benchmarks. Also, lots of indie AI distributors have not achieved SOC 2 compliance.
In shorter, indie AI suppliers are typically not adhering to the frameworks and protocols that hold critical SaaS data and methods safe. These threats turn into amplified when AI equipment are related to company SaaS programs.
Connecting Indie AI to Organization SaaS Apps Boosts Efficiency — and the Probability of Backdoor Attacks
Employees obtain (or understand) considerable approach improvement and outputs with AI tools. But quickly, they are going to want to turbocharge their efficiency gains by connecting AI to the SaaS techniques they use every day, these as Google Workspace, Salesforce, or M365.
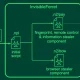
Due to the fact indie AI instruments depend on development through word of mouth more than traditional marketing and profits strategies, indie AI vendors encourage these connections within just the products and solutions and make the approach rather seamless. A Hacker News short article on generative AI security hazards illustrates this issue with an case in point of an personnel who finds an AI scheduling assistant to assist handle time superior by checking and examining the employee’s undertaking management and meetings. But the AI scheduling assistant should link to applications like Slack, company Gmail, and Google Generate to obtain the knowledge it truly is made to analyze.
Because AI applications mostly rely on OAuth entry tokens to forge an AI-to-SaaS connection, the AI scheduling assistant is granted ongoing API-based communication with Slack, Gmail, and Google Generate.
Staff members make AI-to-SaaS connections like this each and every working day with very little issue. They see the attainable rewards, not the inherent hazards. But properly-intentioned staff never comprehend they may have linked a 2nd-amount AI software to your organization’s extremely delicate knowledge.
 Determine 1: How an indie AI software achieves an OAuth token relationship with a major SaaS platform. Credit history: AppOmni
Determine 1: How an indie AI software achieves an OAuth token relationship with a major SaaS platform. Credit history: AppOmni
AI-to-SaaS connections, like all SaaS-to-SaaS connections, will inherit the user’s authorization settings. This translates to a really serious security risk as most indie AI instruments abide by lax security requirements. Threat actors target indie AI instruments as the implies to obtain the related SaaS devices that incorporate the firm’s crown jewels.
After the risk actor has capitalized on this backdoor to your organization’s SaaS estate, they can accessibility and exfiltrate facts till their activity is found. However, suspicious action like this frequently flies under the radar for months or even several years. For instance, about two months handed among the facts exfiltration and community recognize of the January 2023 CircleCI info breach.
With no the proper SaaS security posture management (SSPM) tooling to monitor for unauthorized AI-to-SaaS connections and detect threats like big figures of file downloads, your firm sits at a heightened risk for SaaS details breaches. SSPM mitigates this risk significantly and constitutes a critical component of your SaaS security method. But it’s not intended to exchange review procedures and protocols.
How to Almost Decrease Indie AI Software Security Threats
Acquiring explored the hazards of indie AI, Thacker recommends CISOs and cybersecurity groups concentrate on the fundamentals to prepare their business for AI resources:
1. Never Neglect Standard Because of Diligence
We start off with the basics for a purpose. Assure anyone on your group, or a member of Lawful, reads the phrases of products and services for any AI applications that staff request. Of training course, this is just not necessarily a safeguard against details breaches or leaks, and indie vendors could extend the real truth in hopes of placating business consumers. But totally being familiar with the conditions will tell your legal system if AI suppliers break provider phrases.
2. Take into consideration Utilizing (Or Revising) Application And Info Policies
An application plan presents crystal clear pointers and transparency to your business. A basic “allow-checklist” can go over AI instruments developed by business SaaS providers, and just about anything not provided falls into the “disallowed” camp. Alternatively, you can set up a facts policy that dictates what varieties of info staff can feed into AI tools. For instance, you can forbid inputting any type of intellectual property into AI systems, or sharing details between your SaaS devices and AI apps.
3. Dedicate To Standard Employee Teaching And Education
Couple staff seek out indie AI equipment with destructive intent. The vast the vast majority are basically unaware of the risk they are exposing your firm to when they use unsanctioned AI.
Provide frequent coaching so they comprehend the reality of AI applications details leaks, breaches, and what AI-to-SaaS connections entail. Trainings also provide as opportune moments to demonstrate and boost your guidelines and program critique process.
4. Request The Critical Questions In Your Seller Assessments
As your crew conducts seller assessments of indie AI tools, insist on the identical rigor you use to organization providers beneath evaluate. This procedure have to consist of their security posture and compliance with facts privacy legal guidelines. Concerning the workforce requesting the resource and the seller by itself, deal with issues these kinds of as:
- Who will access the AI resource? Is it restricted to certain persons or groups? Will contractors, associates, and/or consumers have entry?
- What people today and businesses have accessibility to prompts submitted to the software? Does the AI aspect count on a third party, a product company, or a neighborhood design?
- Does the AI device consume or in any way use exterior enter? What would occur if prompt injection payloads have been inserted into them? What influence could that have?
- Can the software take consequential actions, this sort of as improvements to documents, users, or other objects?
- Does the AI resource have any attributes with the likely for common vulnerabilities to come about (this kind of as SSRF, IDOR, and XSS mentioned over)? For example, is the prompt or output rendered exactly where XSS may be probable? Does web fetching performance allow hitting interior hosts or cloud metadata IP?
AppOmni, a SaaS security seller, has published a sequence of CISO Guides to AI Security that supply a lot more in depth vendor evaluation queries together with insights into the possibilities and threats AI equipment existing.
5. Establish Relationships and Make Your Workforce (and Your Procedures) Obtainable
CISOs, security teams, and other guardians of AI and SaaS security must existing themselves as associates in navigating AI to enterprise leaders and their groups. The principles of how CISOs make security a organization precedence crack down to powerful associations, interaction, and accessible pointers.
Demonstrating the effect of AI-relevant info leaks and breaches in phrases of pounds and prospects shed makes cyber pitfalls resonate with organization teams. This enhanced communication is critical, but it is only one step. You could also have to have to modify how your group works with the business.
Irrespective of whether you choose for application or data enable lists — or a mixture of both equally — make sure these recommendations are plainly prepared and commonly offered (and promoted). When employees know what info is allowed into an LLM, or which permitted distributors they can pick for AI applications, your crew is considerably additional probable to be viewed as empowering, not halting, progress. If leaders or workers request AI resources that tumble out of bounds, get started the discussion with what they’re striving to complete and their targets. When they see you’re intrigued in their perspective and wants, they are much more eager to spouse with you on the proper AI resource than go rogue with an indie AI seller.
The finest odds for holding your SaaS stack secure from AI resources over the prolonged expression is making an natural environment in which the enterprise sees your group as a useful resource, not a roadblock.
Observed this write-up interesting? Adhere to us on Twitter and LinkedIn to examine extra exclusive content we write-up.
Some components of this article are sourced from:
thehackernews.com


 ClearFake Campaign Expands to Deliver Atomic Stealer on Macs Systems
ClearFake Campaign Expands to Deliver Atomic Stealer on Macs Systems