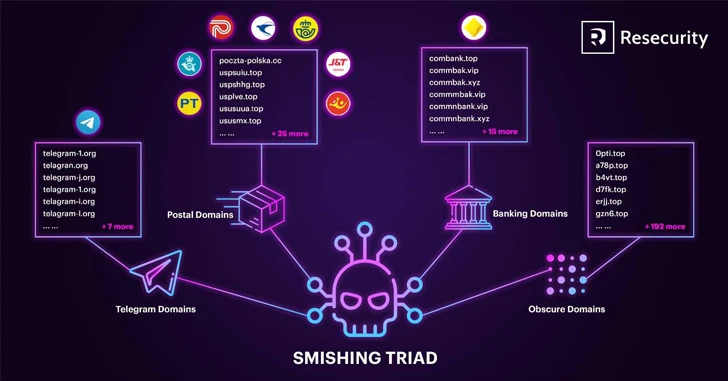
The Chinese-speaking menace actors driving Smishing Triad have been observed masquerading as the United Arab Emirates Federal Authority for Id and Citizenship to mail malicious SMS messages with the ultimate intention of gathering delicate information from residents and foreigners in the nation.
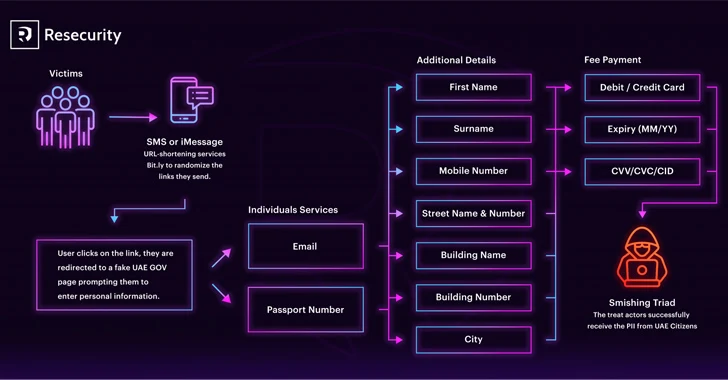
“These criminals deliver malicious back links to their victims’ cell products through SMS or iMessage and use URL-shortening products and services like Little bit.ly to randomize the links they deliver,” Resecurity explained in a report revealed this 7 days. “This will help them shield the fake website’s area and hosting locale.”
Smishing Triad was very first documented by the cybersecurity enterprise in September 2023, highlighting the group’s use of compromised Apple iCloud accounts to send smishing messages for carrying out identity theft and economic fraud.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Approaching WEBINAR Beat AI-Driven Threats with Zero Believe in – Webinar for Security Specialists
Classic security steps would not slice it in present-day environment. It truly is time for Zero Have confidence in Security. Secure your facts like in no way before.
Sign up for Now
The threat actor is also identified to give prepared-to-use smishing kits for sale to other cybercriminals for $200 a month, alongside engaging in Magecart-type attacks on e-commerce platforms to inject destructive code and pilfer buyer details.
“This fraud-as-a-service (FaaS) model permits ‘Smishing Triad’ to scale their functions by empowering other cybercriminals to leverage their tooling and start independent attacks,” Resecurity famous.
The most current attack wave is developed to focus on individuals who have not long ago current their residence visas with damaging messages. The smishing marketing campaign applies to both of those Android and iOS gadgets, with the operators very likely using SMS spoofing or spam services to perpetrate the scheme.
Recipients who click on on the embedded connection the concept are taken to a bogus, lookalike website (“rpjpapc[.]best”) impersonating the UAE Federal Authority for Identity, Citizenship, Customs and Port Security (ICP), which prompts them to enter their individual information these types of as names, passport quantities, cell figures, addresses, and card information.
What would make the marketing campaign noteworthy is the use of a geofencing system to load the phishing type only when visited from UAE-dependent IP addresses and cell products.
“The perpetrators of this act could have accessibility to a personal channel in which they received facts about UAE citizens and foreigners dwelling in or checking out the state,” Resecurity explained.
“This could be obtained by way of 3rd-party data breaches, organization email compromises, databases bought on the dark web, or other resources.”
Smishing Triad’s most recent campaign coincides with the start of a new underground market place known as OLVX Market (“olvx[.]cc”) that operates on the clear web and claims to provide tools to have out online fraud, these as phish kits, web shells, and compromised credentials.

“Although the OLVX marketplace provides hundreds of individual merchandise across quite a few classes, its site administrators preserve relationships with different cybercriminals who make custom toolkits and can receive specialised data files, therefore furthering OLVX’s potential to manage and catch the attention of shoppers to the system,” ZeroFox stated.
Cyber Criminals Misuse Predator Bot Detection Instrument for Phishing Attacks
The disclosure comes as Trellix revealed how menace actors are leveraging Predator, an open up-tool designed to beat fraud and identify requests originating from automatic programs, bots, or web crawlers, as element of various phishing strategies.
The setting up stage of the attack is a phishing email despatched from a formerly compromised account and made up of a malicious website link, which, when clicked, checks if the incoming request is coming from a bot or a crawler, right before redirecting to the phishing webpage.
The cybersecurity company said it determined a variety of artifacts in which the menace actors repurposed the first tool by giving a listing of really hard-coded inbound links as opposed to creating random one-way links dynamically on detecting a visitor is a bot.
“Cyber criminals are generally hunting for new strategies to evade detection from organizations’ security products,” security researcher Vihar Shah and Rohan Shah mentioned. “Open-resource tools these kinds of as these make their task less complicated, as they can easily use these resources to prevent detection and more effortlessly accomplish their malicious plans.”
Found this article interesting? Adhere to us on Twitter and LinkedIn to read through extra distinctive content material we write-up.
Some areas of this report are sourced from:
thehackernews.com

 3,500 Arrested in Global Operation HAECHI-IV Targeting Financial Criminals
3,500 Arrested in Global Operation HAECHI-IV Targeting Financial Criminals