Menace actors can get edge of Amazon Web Services Security Token Company (AWS STS) as a way to infiltrate cloud accounts and conduct comply with-on attacks.
The service permits risk actors to impersonate user identities and roles in cloud environments, Purple Canary researchers Thomas Gardner and Cody Betsworth reported in a Tuesday assessment.
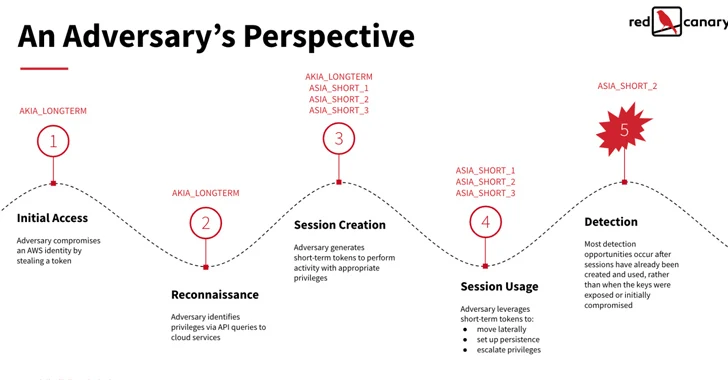
AWS STS is a web service that permits buyers to request short term, restricted-privilege credentials for users to obtain AWS resources devoid of needing to produce an AWS identity. These STS tokens can be legitimate any where from 15 minutes to 36 hours.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Threat actors can steal long-term IAM tokens through a wide range of strategies like malware bacterial infections, publicly exposed qualifications, and phishing emails, subsequently making use of them to decide roles and privileges linked with these tokens by using API phone calls.

“Based on the token’s permission amount, adversaries may also be in a position to use it to make extra IAM customers with extended-phrase AKIA tokens to be certain persistence in the function that their first AKIA token and all of the ASIA limited phrase tokens it produced are learned and revoked,” the researcher claimed.
In the future stage, an MFA-authenticated STS token is applied to make multiple new shorter-expression tokens, followed by conducting put up-exploitation actions such as details exfiltration.
To mitigate this sort of AWS token abuse, it is encouraged to log CloudTrail function data, detect part-chaining situations and MFA abuse, and rotate lengthy-time period IAM person access keys.
“AWS STS is a critical security manage for restricting the use of static qualifications and the period of entry for consumers throughout their cloud infrastructure,” the scientists explained.
“Nonetheless, underneath sure IAM configurations that are widespread throughout many organizations, adversaries can also build and abuse these STS tokens to obtain cloud means and complete destructive actions.”
Identified this report fascinating? Comply with us on Twitter and LinkedIn to go through more unique content we article.
Some elements of this write-up are sourced from:
thehackernews.com

 New Report: Unveiling the Threat of Malicious Browser Extensions
New Report: Unveiling the Threat of Malicious Browser Extensions