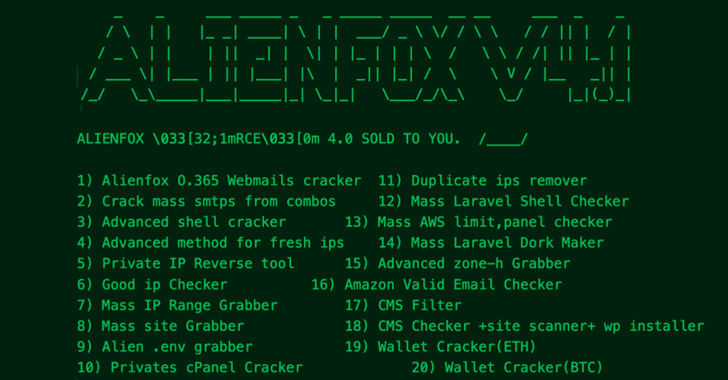
A new “detailed toolset” identified as AlienFox is becoming distributed on Telegram as a way for menace actors to harvest qualifications from API keys and tricks from well-known cloud assistance vendors.
“The distribute of AlienFox signifies an unreported trend toward attacking additional negligible cloud companies, unsuitable for crypto mining, in get to enable and expand subsequent strategies,” SentinelOne security researcher Alex Delamotte claimed in a report shared with The Hacker Information.
The cybersecurity enterprise characterized the malware as very modular and frequently evolving to accommodate new characteristics and performance enhancements.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The principal use of AlienFox is to enumerate misconfigured hosts by using scanning platforms like LeakIX and SecurityTrails, and subsequently leverage different scripts in the toolkit to extract qualifications from configuration documents exposed on the servers.
Exclusively, it entails exploring for inclined servers related with common web frameworks, including Laravel, Drupal, Joomla, Magento, Opencart, Prestashop, and WordPress.
Recent variations of the resource incorporate the means to set up persistence on an Amazon Web Companies (AWS) account and escalate privileges as nicely as automate spam campaigns by way of the compromised accounts.
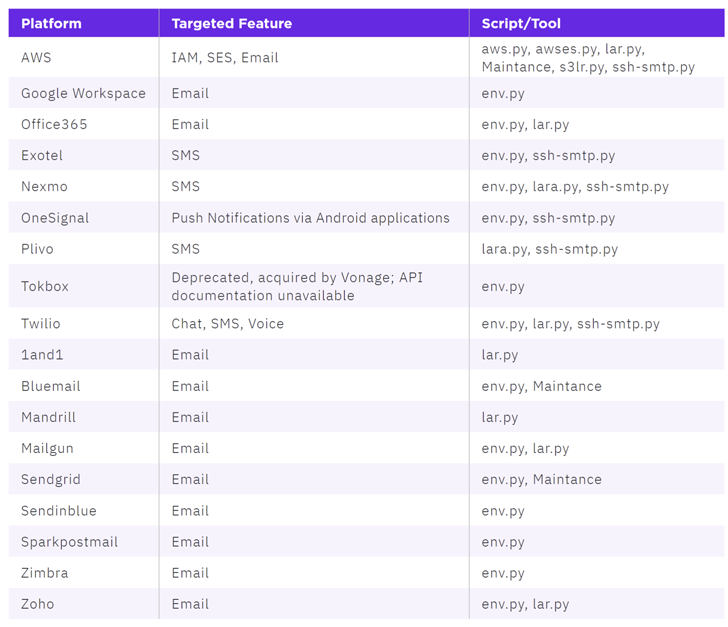
Attacks involving AlienFox are claimed to be opportunistic, with the scripts capable of collecting sensitive info pertaining to AWS, Bluemail, Exotel, Google Workspace, Mailgun, Mandrill, Microsoft 365, Sendgrid, Twilio, Zimbra, and Zoho.
Two these scripts are AndroxGh0st and GreenBot, which ended up earlier documented by Lacework and Permiso p0 Labs. SentinelOne claimed it discovered a few various variants of the malware (from v2 to v4) courting again to February 2022.
WEBINARDiscover the Concealed Hazards of Third-Party SaaS Apps
Are you conscious of the hazards involved with third-party application obtain to your company’s SaaS apps? Join our webinar to find out about the types of permissions remaining granted and how to limit risk.
RESERVE YOUR SEAT
A notable functionality of the v4 is its potential to check out if an email address is now connected to an Amazon.com retail account, and if not, create a new account employing that handle.
To mitigate threats posed by AlienFox, companies are encouraged to adhere to configuration administration best tactics and abide by the basic principle of the very least privilege (PoLP).
“The AlienFox toolset demonstrates an additional stage in the evolution of cybercrime in the cloud,” Delamotte mentioned. “For victims, compromise can lead to additional assistance fees, loss in purchaser trust, and remediation expenses.”
Observed this short article intriguing? Stick to us on Twitter and LinkedIn to read through extra exceptional written content we submit.
Some elements of this write-up are sourced from:
thehackernews.com

 Okta launches new partner programme to capture $80b identity market
Okta launches new partner programme to capture $80b identity market