Amazon, in December 2021, patched a substantial severity vulnerability influencing its Pictures application for Android that could have been exploited to steal a user’s obtain tokens.
“The Amazon entry token is applied to authenticate the user across numerous Amazon APIs, some of which contain private knowledge such as total title, email, and deal with,” Checkmarx researchers João Morais and Pedro Umbelino stated. “Many others, like the Amazon Drive API, allow an attacker entire access to the user’s data files.”
The Israeli software security screening organization claimed the issue to Amazon on November 7, 2021, following which the tech big rolled out a resolve on December 18, 2021.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The leak is the result of a misconfiguration in one particular of the app’s components named “com.amazon.gallery.thor.application.exercise.ThorViewActivity” that’s described in the AndroidManifest.xml file and which, when released, initiates an HTTP ask for with a header containing the accessibility token.
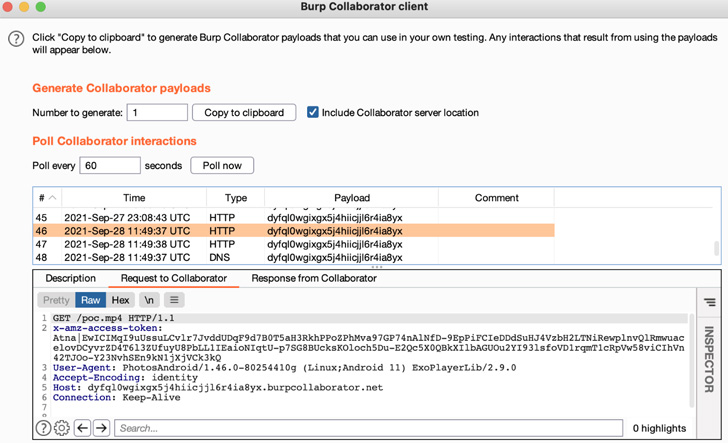
In a nutshell, it indicates that an exterior application could send an intent — a message to aid communication concerning applications — to launch the vulnerable action in dilemma and redirect the HTTP ask for to an attacker-controlled server and extract the entry token.

Calling the bug a case of broken authentication, the cybersecurity organization reported the issue could have enabled malicious applications installed on the gadget to grab the accessibility tokens, granting the attacker permissions to make use of the APIs for abide by-on functions.
This could differ from deleting information and folders in Amazon Push to even exploiting the access to stage a ransomware attack by studying, encrypting, and re-creating a victim’s information when erasing their record.
Checkmarx further observed that the vulnerability may possibly have experienced a broader impact provided that the APIs exploited as element of its evidence-of-notion (PoC) constitute only a compact subset of the overall Amazon ecosystem.
Observed this write-up attention-grabbing? Adhere to THN on Facebook, Twitter and LinkedIn to study a lot more unique written content we submit.
Some sections of this post are sourced from:
thehackernews.com


 Northern Ireland is the future of British cyber security
Northern Ireland is the future of British cyber security