Many security flaws have been disclosed in Apache OpenMeetings, a web conferencing resolution, that could be perhaps exploited by destructive actors to seize command of admin accounts and run destructive code on inclined servers.
“Attackers can carry the application into an sudden condition, which allows them to get above any user account, including the admin account,” Sonar vulnerability researcher Stefan Schiller reported in a report shared with The Hacker Information.
“The acquired admin privileges can even further be leveraged to exploit an additional vulnerability allowing for attackers to execute arbitrary code on the Apache OpenMeetings server.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Adhering to dependable disclosure on March 20, 2023, the vulnerabilities were addressed with the release of Openmeetings variation 7.1. that was launched on Might 9, 2023. The list of 3 flaws is as follows –
- CVE-2023-28936 (CVSS score: 5.3) – Insufficient check out of invitation hash
- CVE-2023-29032 (CVSS score: 8.1) – An authentication bypass that sales opportunities to unrestricted access through invitation hash
- CVE-2023-29246 (CVSS rating: 7.2) – A NULL byte (%00) injection that makes it possible for an attacker with admin privileges to get code execution
Conference invites produced making use of OpenMeetings appear are not only sure to a certain home and a person but also come with a special hash which is utilized by the application to retrieve information affiliated with the invitation.
Forthcoming WEBINARShield In opposition to Insider Threats: Grasp SaaS Security Posture Administration
Nervous about insider threats? We’ve received you coated! Join this webinar to take a look at sensible strategies and the strategies of proactive security with SaaS Security Posture Management.
Be a part of Nowadays
The initially two flaws, in a nutshell, have to do with a weak hash comparison between the person-supplied hash and what is actually present in the databases and a quirk that permits for the development of a room invitation without having a place assigned to it, major to a situation exactly where an invitation exists with no place hooked up to it.
A threat actor could exploit these shortcomings to produce an event and be a part of the corresponding home, and observe it up by deleting the function, at which issue an invitation is produced for the admin user to the non-present space. In the following stage, the weak hash comparison bug could be leveraged to enumerate the despatched invitation and redeem it by providing a wildcard hash input.
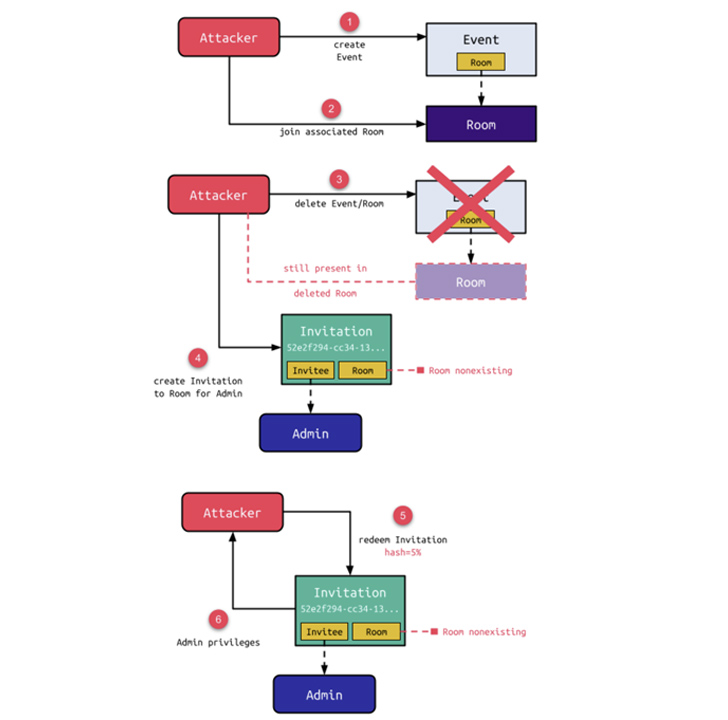
“Whilst the area is also deleted when its connected party is deleted, the presence of the attacker in the home will make this a zombie home,” Schiller discussed. “Whilst an error is elevated when redeeming the hash for these kinds of an invitation, a valid web session for the invitee with comprehensive permissions of this person is produced.”
In other words, the zombie room could let the attacker to obtain admin privileges and make modifications to the OpenMeetings occasion, including incorporating and getting rid of people and groups, switching room configurations, and terminating classes of related people.
Sonar said it also discovered a 3rd vulnerability that is rooted in a feature that enables an administrator to configure the path for executables linked to ImageMagick, an open up-resource computer software utilized to edit and course of action illustrations or photos. This permits an attacker with admin privileges to gain code execution by modifying the ImageMagic route to “/bin/sh%00x” and triggering arbitrary shell commands.
“When now uploading a faux picture made up of a valid image header adopted by arbitrary shell commands, the conversion spawns /bin/sh with the initial argument staying the bogus picture, effectively executing just about every command in it,” Schiller reported.
“In mixture with the account takeover, this vulnerability enables a self-registered attacker to achieve remote code execution on the fundamental server.”
Discovered this short article fascinating? Comply with us on Twitter and LinkedIn to go through much more exceptional content we put up.
Some elements of this article are sourced from:
thehackernews.com


 North Korean State-Sponsored Hackers Suspected in JumpCloud Supply Chain Attack
North Korean State-Sponsored Hackers Suspected in JumpCloud Supply Chain Attack