Apple earlier this 12 months set a security vulnerability in iOS and macOS that could have probably permitted an attacker to get unauthorized entry to a user’s iCloud account.
Uncovered in February by Thijs Alkemade, a security expert at IT security business Computest, the flaw resided in Apple’s implementation of TouchID (or FaceID) biometric characteristic that authenticated end users to log in to internet websites on Safari, exclusively those that use Apple ID logins.
Immediately after the issue was described to Apple by way of their dependable disclosure program, the iPhone maker addressed the vulnerability in a server-facet update.
An Authentication Flaw
The central premise of the flaw is as follows. When buyers attempt to sign in to a website that needs an Apple ID, a prompt is shown to authenticate the login applying Touch ID. Doing so skips the two-element authentication stage given that it presently leverages a blend of things for identification, such as the product (anything you have) and the biometric details (a thing you are).
Distinction this during logins to Apple domains (e.g. “icloud.com”) the standard way with an ID and password, wherein the web page embeds an iframe pointing to Apple’s login validation server (“https://idmsa.apple.com”), which handles the authentication method.
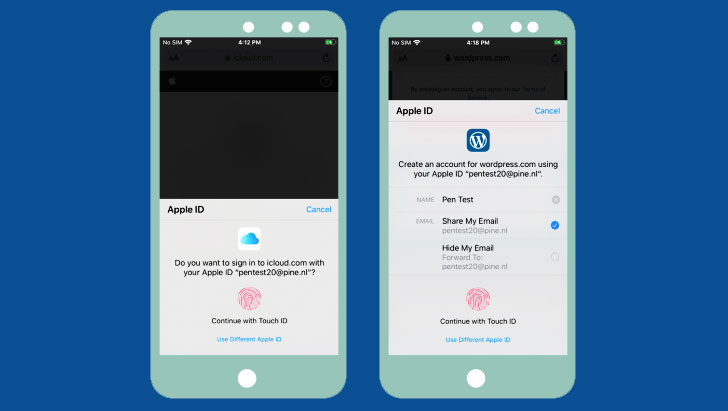
A proven in the movie demonstration, the iframe URL also is made up of two other parameters — a “consumer_id” identifying the assistance (e.g., iCloud) and a “redirect_uri” that has the URL to be redirected to immediately after effective verification.
But in the circumstance where a person is validated making use of TouchID, the iframe is taken care of otherwise in that it communicates with the AuthKit daemon (akd) to handle the biometric authentication and subsequently retrieve a token (“grant_code”) that’s applied by the icloud.com site to continue the login method.
To do this, the daemon communicates with an API on “gsa.apple.com,” to which it sends the information of the request and from which it receives the token.
The security flaw learned by Computest resides in the aforementioned gsa.apple.com API, which produced it theoretically attainable to abuse people domains to validate a customer ID without having authentication.
“Even nevertheless the customer_id and redirect_uri have been included in the info submitted to it by akd, it did not look at that the redirect URI matches the customer ID,” Alkemade famous. “As a substitute, there was only a whitelist used by AKAppSSOExtension on the domains. All domains ending with apple.com, icloud.com and icloud.com.cn have been permitted.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This indicates that an attacker could exploit a cross-website scripting vulnerability on any a person of Apple’s subdomains to run a destructive snippet of JavaScript code that can cause a login prompt utilizing the iCloud shopper ID, and use the grant token to get a session on icloud.com.
Placing Up Phony Hotspots to Take Around iCloud Accounts
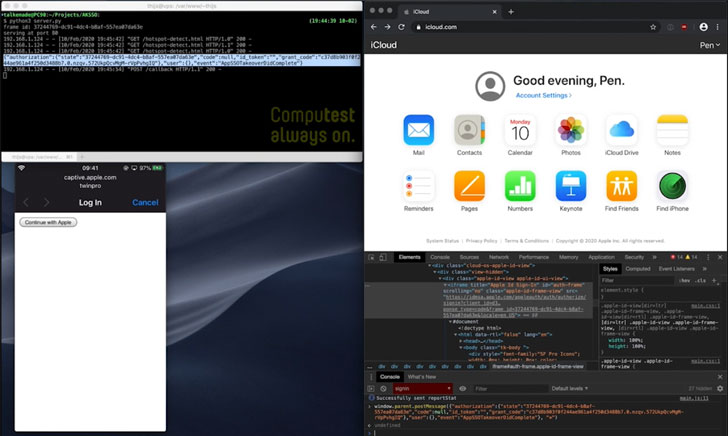
In a separate state of affairs, the attack could be executed by embedding JavaScript on the web web page that is exhibited when connecting to a Wi-Fi network for the initially time (through “captive.apple.com”), therefore enabling an attacker access to a user’s account by just accepting a TouchID prompt from that web site.
“A malicious Wi-Fi network could respond with a page with JavaScript which initiates OAuth as iCloud,” Alkemade explained. “The person gets a TouchID prompt, but it is pretty unclear what it implies. If the consumer authenticates on that prompt, their session token will be despatched to the malicious web page, providing the attacker a session for their account on iCloud.”
“By location up a faux hotspot in a site where buyers expect to get a captive portal (for example at an airport, hotel or teach station), it would have been feasible to attain accessibility to a significant number of iCloud accounts, which would have authorized accessibility to backups of pics, locale of the phone, files and a lot more,” he included.
This is not the very first time security issues have been found in Apple’s authentication infrastructure. In Might, Apple patched a flaw impacting its “Signal in with Apple” procedure that could have built it attainable for distant attackers to bypass authentication and take in excess of focused users’ accounts on third-occasion services and applications that have been registered using Apple’s signal-in selection.
Discovered this write-up attention-grabbing? Adhere to THN on Fb, Twitter and LinkedIn to read extra exceptional information we put up.


 Punishing Cybersecurity Errors Discovered to be Counterproductive
Punishing Cybersecurity Errors Discovered to be Counterproductive