Picture a cybersecurity landscape wherever defenses are impenetrable, and threats are absolutely nothing far more than mere disturbances deflected by a strong defend. Sadly, this image of fortitude remains a pipe dream even with its comforting nature. In the security earth, preparedness is not just a luxury but a necessity. In this context, Mike Tyson’s well-known adage, “Everyone has a plan till they get punched in the encounter,” lends itself to our arena – cyber defenses must be struggle-analyzed to stand a probability.
Tyson’s words and phrases capture the paradox of readiness in cybersecurity: way too usually, untested cyber defenses can develop a fake sense of security, major to dire penalties when genuine threats land a blow. This is where Breach and Attack Simulation (BAS), a proactive device in any organization’s cybersecurity arsenal, will come into participate in.
When Cybersecurity Meets the Punch – The Assumption Issue
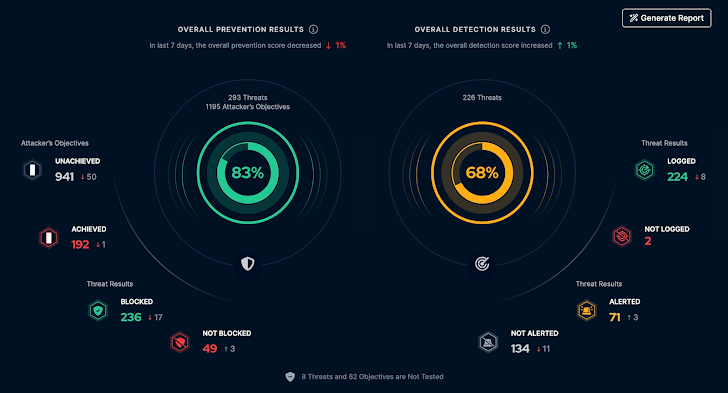
Assumptions are the hidden icebergs in cybersecurity’s wide ocean. Although we may possibly believe our security controls are foolproof, the studies paint a different photograph. In accordance to the Blue Report 2023 by Picus, only 59% of attacks are prevented, just 37% detected, and a scant 16% activated alerts. This facts reveals an alarming reality: cybersecurity steps often fall short in authentic-earth eventualities. Frequently, this shortcoming is thanks to complexities in configuration and a lack of proficient experts, which can lead to underperforming and misconfigured defenses. At the very same time, regular tests strategies like penetration tests and pink group exercises can’t absolutely gauge the success of an organization’s security. This can lead to the normally perilous assumption that security controls are effective with out consistently tension-tests them in actual-world situations.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
This chasm concerning perceived and actual security confirms the expanding want for security validation as a result of Breach and Attack Simulation (BAS) – a system of confronting these fallacies by rigorously validating defenses prior to attacks catch companies off guard. Ultimately, BAS tightens the veil of cybersecurity across every single potential breach.
Shifting the Attitude from Plan to Practice
Cultivating a proactive cybersecurity culture is akin to shadowboxing, placing principle into motion. Cyber threats morph as swiftly as clouds in a stormy sky, and simulations ought to be as dynamic as the threats they mimic. This cultural shift begins at the top rated, with leadership championing the embrace of continuous security validation by means of BAS. Only then can cybersecurity teams embed this exercise-centric philosophy, sparring with simulations usually and with intent.
The Mechanics of BAS
BAS is a fact check out for your cybersecurity posture. At its main, BAS is the systematic, controlled simulation of cyberattacks throughout your manufacturing network. Each individual simulation is made to mimic the conduct of genuine attackers, cultivating preparedness for adversary methods, techniques, and processes (TTPs). According to the Purple Report 2023, danger actors use an regular of 11 different TTPs in the course of an attack.
For case in point, an APT attack scenario begins with first breach procedures, these types of as exploiting software program vulnerabilities or phishing e-mails with destructive attachments. Then, it moves deeper, trying lateral movements within the network, escalating privileges the place attainable, and striving to exfiltrate simulated sensitive info. In this state of affairs, the objective is to replicate an total attack lifecycle with fidelity, all when analyzing how your security controls respond at each phase.
What’s far more, BAS is not just a one-off exercise. It is an ongoing system that adapts as the threat landscape evolves. As new malware variants, TTPs, exploit techniques, APT campaigns, and other emerging threats occur to mild, they are included into the BAS tool’s danger intelligence library. This ensures that your firm can protect alone in opposition to the likely threats of right now and tomorrow.
Following each individual simulation, BAS applications present extensive analytics and insightful stories. These include important facts on how the intrusion was (or was not) detected or prevented, the time it took for the security controls to reply, and the efficiency of the reaction.
Armed with this information, cybersecurity professionals can better prioritize their reaction tactics, concentrating on the most pressing gaps in their organizational defense very first. They can also wonderful-tune present security controls with easy-to-implement avoidance signatures and detection procedures that can improve their capability to detect, avert, or respond to cyber threats.
Integrating the BAS Punch into Your Cyber Strategy
Envision that BAS is a reliable pulse reinforcing your security steps. Correctly incorporating BAS into your organization’s defenses starts with critical evaluation to ascertain how it enhances your cybersecurity architecture.
Step 1: Tailor BAS to Your Demands
Customizing BAS for your corporation starts off with knowledge the threats you might be most possible to deal with – since a bank’s major cybersecurity worries vary from a hospital’s. Pick out simulations that mirror the most suitable threats to your sector and technical infrastructure. Modern day BAS resources can deliver custom-made simulation playbooks with cyber threats most likely to have an effect on your firm.
Step 2: Build a Simulation Plan
Consistency is critical. Operate BAS simulations regularly, not just as a 1-time event but as an integral element of your cybersecurity strategy. Build a cadence – no matter if day-to-day, weekly, every month, or in real-time adhering to sizeable IT or danger landscape alterations – to continue being a move ahead of adversaries who constantly refine their practices.
Phase 3: Apply the Insights
The correct benefit of BAS lies in the actionable insights derived from simulation effects. Highly developed BAS platforms offer sensible suggestions, such as prevention signatures and detection rules that can be immediately incorporated into security controls – together with IPS, NGFW, WAF, EDR, SIEM, SOAR, and other security solutions – to improve your security posture straight away.
Action 4: Measure and Refine
Define quantitative achievements metrics to evaluate the impression of BAS on your organization’s cybersecurity. This can include the ratio of blocked/logged/alerted attacks to all attacks, the range of dealt with defensive gaps, or enhancements in detection and response instances. Repeatedly refine your BAS process primarily based on these effectiveness indicators to ensure your defenses get sharper with each individual iteration.
All set to Fortify Your Cyber Defenses with the Pioneer of BAS Technology?
As we unpack the parallels involving a boxer’s defense and an organization’s security posture, one particular mantra echoes correct: surviving the first punch is about resilience by relentless follow. Right here, we have demonstrated the critical job BAS performs in cultivating a proactive solution to the unpredictability of cyber threats.
Picus Security pioneered Breach and Attack Simulation (BAS) technology in 2013 and has assisted corporations strengthen their cyber resilience ever because. With Picus Security Validation Platform, your firm can assume unparalleled visibility into its security posture, so you can hone your defenses versus even the most refined cyberattacks.
With Picus, you are not just reacting you happen to be proactively countering cyber threats just before they impression your functions. Organizations have to throw the 1st punch, demanding and strengthening their defenses for when the actual combat commences. So, equipment up it can be time to put your cyber defenses to the test. Go to us at picussecurity.com to reserve a demo or check out our sources.
Note: This posting was prepared by Dr. Suleyman Ozarslan, co-founder and VP of Picus Labs at Picus Security, where by simulating cyber threats and empowering defenses are our passions.
Located this write-up intriguing? Abide by us on Twitter and LinkedIn to browse additional special content we publish.
Some elements of this posting are sourced from:
thehackernews.com

 Cryptominers Targeting Misconfigured Apache Hadoop and Flink with Rootkit in New Attacks
Cryptominers Targeting Misconfigured Apache Hadoop and Flink with Rootkit in New Attacks