The Iranian state-backed hacking outfit referred to as APT42 is making use of improved social engineering strategies to infiltrate target networks and cloud environments.
Targets of the attack contain Western and Center Japanese NGOs, media businesses, academia, legal companies and activists, Google Cloud subsidiary Mandiant mentioned in a report released previous 7 days.
“APT42 was observed posing as journalists and celebration organizers to construct believe in with their victims by ongoing correspondence, and to supply invitations to conferences or legitimate paperwork,” the business claimed.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“These social engineering schemes enabled APT42 to harvest credentials and use them to obtain preliminary access to cloud environments. Subsequently, the threat actor covertly exfiltrated facts of strategic interest to Iran, although relying on designed-in characteristics and open up-source equipment to prevent detection.”
APT42 (aka Damselfly and UNC788), first documented by the organization in September 2022, is an Iranian condition-sponsored cyber espionage team tasked with conducting information and facts assortment and surveillance functions against folks and companies of strategic desire to the Iranian authorities.
It is really assessed to be a subset of another notorious danger team tracked as APT35, which is also identified by a variety of names CALANQUE, CharmingCypress, Charming Kitten, ITG18, Mint Sandstorm (previously Phosphorus), Newscaster, TA453, and Yellow Garuda.

Equally the groups are affiliated with Iran’s Islamic Innovative Guard Corps (IRGC), but operate with a unique set of objectives.
Although Charming Kitten focuses extra on lengthy-phrase, malware-intense operations concentrating on corporations and firms in the U.S. and Center East to steal information. APT42, in contrast, targets unique people today and organizations that the regime has its eye on for the intent of domestic politics, international plan, and regime steadiness.
Previously this January, Microsoft attributed the Charming Kitten actor to phishing strategies focusing on higher-profile men and women functioning on Center Japanese affairs at universities and exploration businesses in Belgium, France, Gaza, Israel, the U.K., and the U.S. given that November 2023.
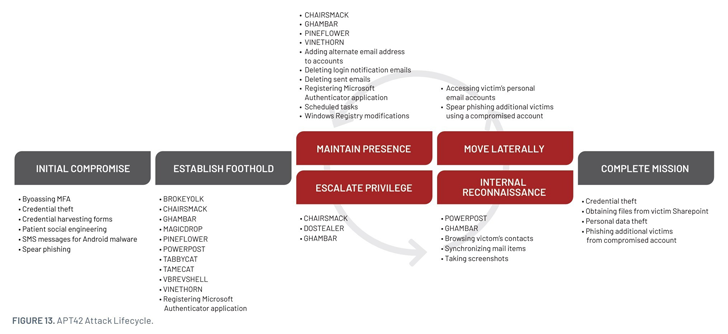
Attacks mounted by the team are recognised to require intensive credential harvesting functions to gather Microsoft, Yahoo, and Google Credentials through spear-phishing e-mails made up of destructive back links to lure files that redirect the recipients to a pretend login webpage.
In these strategies, the adversary has been noticed sending e-mails from domains typosquatting the unique entities and masquerading as news retailers respectable services like Dropbox, Google Fulfill, LinkedIn, and YouTube and mailer daemons and URL shortening instruments.
The credential-grabbing attacks are complemented by data exfiltration things to do concentrating on the victims’ public cloud infrastructure to get hold of paperwork that are of curiosity to Iran, but only just after gaining their believe in – something Charming Kitten is effectively-versed at.
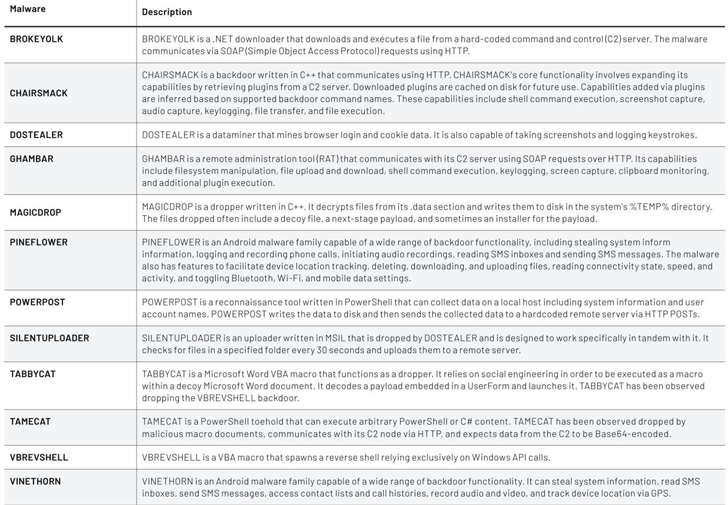 Known malware family members linked with APT42
Known malware family members linked with APT42
“These functions started with improved social engineering schemes to acquire the first entry to victim networks, usually involving ongoing belief-developing correspondence with the target,” Mandiant mentioned.
“Only then the sought after credentials are obtained and multi-factor authentication (MFA) is bypassed, by serving a cloned internet site to seize the MFA token (which unsuccessful) and later by sending MFA thrust notifications to the sufferer (which succeeded).”
In an hard work to protect up its tracks and blend in, the adversary has been uncovered relying on publicly accessible resources, exfiltrating data files to a OneDrive account masquerading as the victim’s group, and employing VPN and anonymized infrastructure to interact with the compromised surroundings.

Also used by APT42 are two personalized backdoors that act as a jumping place to deploy supplemental malware or to manually execute commands on the machine –
- NICECURL (aka BASICSTAR) – A backdoor published in VBScript that can obtain additional modules to be executed, like facts mining and arbitrary command execution
- TAMECAT – A PowerShell toehold that can execute arbitrary PowerShell or C# articles
It’s value noting that NICECURL was earlier dissected by cybersecurity business Volexity in February 2024 in link with a sequence of cyber attacks aimed at Center East coverage specialists.
“APT42 has remained somewhat concentrated on intelligence assortment and focusing on comparable victimology, inspite of the Israel-Hamas war that has led other Iran-nexus actors to adapt by conducting disruptive, destructive, and hack-and-leak routines,” Mandiant concluded.
“The approaches deployed by APT42 leave a small footprint and could possibly make the detection and mitigation of their functions more complicated for network defenders.”
Discovered this write-up attention-grabbing? Stick to us on Twitter and LinkedIn to read through extra special content we publish.
Some components of this post are sourced from:
thehackernews.com

 China-Linked Hackers Used ROOTROT Webshell in MITRE Network Intrusion
China-Linked Hackers Used ROOTROT Webshell in MITRE Network Intrusion