Entities in Armenia have appear less than a cyber attack making use of an up-to-date variation of a backdoor termed OxtaRAT that will allow remote accessibility and desktop surveillance.
“The resource abilities incorporate searching for and exfiltrating files from the contaminated device, recording the movie from the web digicam and desktop, remotely managing the compromised equipment with TightVNC, setting up a web shell, carrying out port scanning, and more,” Examine Level Study mentioned in a report.
The newest marketing campaign is explained to have commenced in November 2022 and marks the 1st time the risk actors behind the exercise have expanded their aim over and above Azerbaijan.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“The risk actors guiding these attacks have been focusing on human rights corporations, dissidents, and unbiased media in Azerbaijan for several several years,” the cybersecurity firm famous, calling the marketing campaign Operation Silent Watch.
The late 2022 intrusions are substantial, not the very least because of the changes in the infection chain, the methods taken to strengthen operational security, and equip the backdoor with far more ammunition.
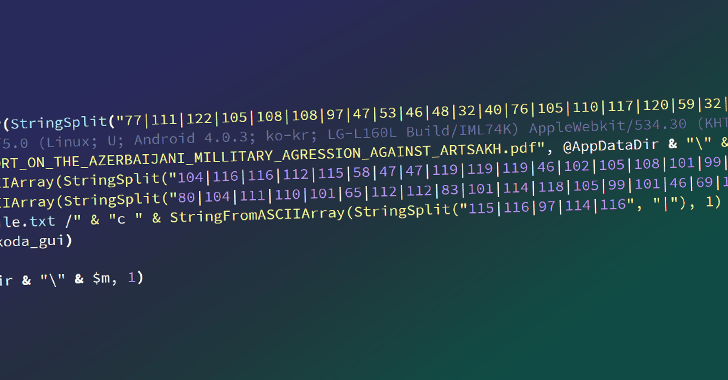
The setting up place of the attack sequence is a self-extracting archive that mimics a PDF file and bears a PDF icon. Launching the purported “document” opens a decoy file though also stealthily executing malicious code hidden inside an impression.
A polyglot file that brings together compiled AutoIT script and an graphic, OxtaRAT options commands that allow the menace actor to operate extra instructions and data files, harvest delicate data, accomplish reconnaissance and surveillance by means of a web digital camera, and even pivot to other.
OxtaRAT has been set to use by the adversary as much again as June 2021, albeit with drastically lessened functionality, indicating an endeavor to consistently update its toolset and manner it into a Swiss Military knife malware.
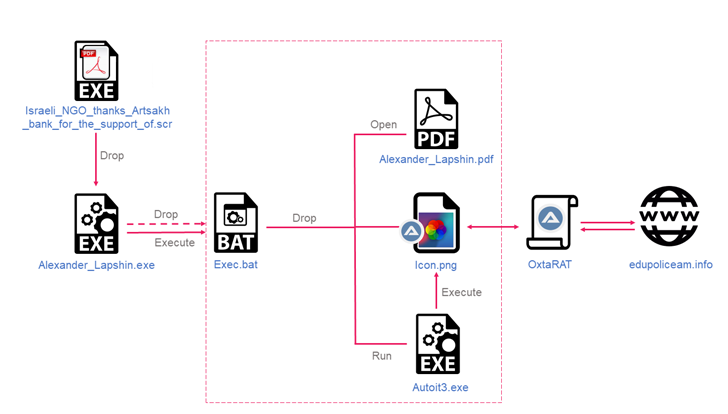
The November 2022 attack also stands out for a amount of reasons. The initial is that the .SCR information that activate the get rid of chain currently incorporate the OxtaRAT implant as opposed to acting as a downloader to fetch the malware.
“This will save the actors from needing to make extra requests for binaries to the C&C server and attracting unwanted focus, as effectively as hides the primary malware from being effortlessly discovered on the infected equipment, as it appears to be like a normal graphic and bypasses style-precise protections,” Check out Issue explained.
The second hanging facet is the geofencing of command-and-management (C2) domains that host the auxiliary equipment to Armenian IP addresses.
Also of take note is the capacity of OxtaRAT to run instructions for port scanning and to exam the speed of an internet relationship, that latter of which is likely employed as a way to conceal the “considerable” facts exfiltration.
“OxtaRAT, which beforehand experienced typically area recon and surveillance abilities, can now be applied as a pivot for energetic reconnaissance of other gadgets,” Check Point explained.
“This may point out that the danger actors are making ready to extend their principal attack vector, which is at this time social engineering, to infrastructure-based mostly attacks. It also might be a indication that the actors are shifting from focusing on persons to targeting additional elaborate or company environments.”
“The fundamental risk actors have been retaining the progress of Vehicle-IT based malware for the final 7 decades, and are working with it in surveillance campaigns whose targets are steady with Azerbaijani passions.”
Observed this report attention-grabbing? Observe us on Twitter and LinkedIn to go through much more distinctive content material we submit.
Some sections of this short article are sourced from:
thehackernews.com

 Cisco issues patch for critical vulnerability in open source ClamAV antivirus
Cisco issues patch for critical vulnerability in open source ClamAV antivirus