In what is actually a continuing assault on the open up resource ecosystem, more than 15,000 spam packages have flooded the npm repository in an attempt to distribute phishing back links.
“The offers have been developed making use of automatic processes, with undertaking descriptions and auto-created names that intently resembled one particular another,” Checkmarx researcher Yehuda Gelb claimed in a Tuesday report.
“The attackers referred to retail web-sites employing referral IDs, consequently profiting from the referral rewards they acquired.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The modus operandi entails poisoning the registry with rogue offers that incorporate one-way links to phishing campaigns in their README.md data files, evocative of a very similar marketing campaign the software package provide chain security firm uncovered in December 2022.
The pretend modules masqueraded as cheats and free of charge means, with some deals named as “absolutely free-tiktok-followers,” “cost-free-xbox-codes,” and “instagram-followers-cost-free.”
The top target of the procedure is to entice users into downloading the packages and clicking on the one-way links to the phishing sites with bogus promises of greater followers on social media platforms.
“The deceptive web web pages are very well-designed and, in some conditions, even consist of pretend interactive chats that show up to display customers acquiring the activity cheats or followers they ended up promised,” Gelb discussed.
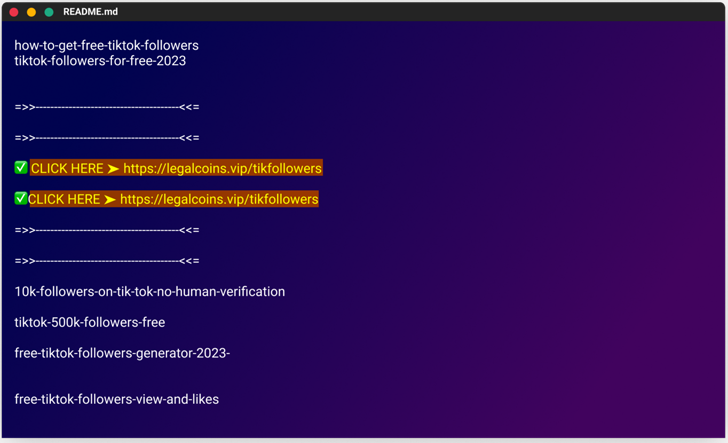
The web sites urge victims to fill out surveys, which then pave the way for additional surveys or, alternatively, redirect them to reputable e-commerce portals like AliExpress.
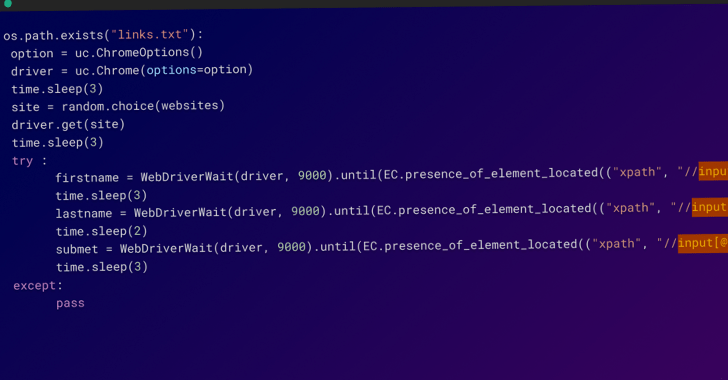
The offers are explained to have been uploaded to npm from several user accounts within just hours involving February 20 and 21, 2023, employing a Python script that automates the whole process.
What is much more, the Python script is also engineered to append inbound links to the published npm offers on WordPress web-sites operated by the risk actor that claim to offer Family members Island cheats.
This is achieved by making use of the selenium Python package deal to interact with the internet websites and make the required modifications.
In all, the use of automation permitted the adversary to publish a big amount of deals in a brief span of time, not to mention generate quite a few consumer accounts to conceal the scale of the attack.
“This demonstrates the sophistication and perseverance of these attackers, who ended up eager to spend considerable resources in buy to carry out this campaign,” Gelb stated.
The results as soon as yet again reveal the troubles in securing the computer software source chain, as risk actors continue to adapt with “new and unpredicted strategies.”
Discovered this post attention-grabbing? Stick to us on Twitter and LinkedIn to study additional exclusive content material we article.
Some elements of this short article are sourced from:
thehackernews.com

 3 Steps to Automate Your Third-Party Risk Management Program
3 Steps to Automate Your Third-Party Risk Management Program