Container technology has attained traction among the enterprises owing to the improved efficiency it offers. In this regard, organizations extensively use Kubernetes for deploying, scaling, and running containerized apps. Companies really should audit Kubernetes to guarantee compliance with regulations, discover anomalies, and discover security threats. The Wazuh open up source system performs a critical position in checking Kubernetes and other parts of an organization’s infrastructure.
What is Kubernetes?
Kubernetes is an open source container management solution that automates the deployment and scaling of containers and also manages the lifetime cycle of containers. It organizes containers into logical models for very simple management and discovery. Kubernetes extends how we scale containerized applications so that we might use a genuinely persistent infrastructure.
You can make cloud-indigenous apps based on microservices with Kubernetes. Lovers look at Kubernetes as the cornerstone of software modernization. It allows the containerization of present-day applications, permitting developers to create applications immediately.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The complexity of working systems grows when they distribute throughout quite a few servers and containers. To handle this complexity, Kubernetes delivers an open up supply API that manages where by and how people containers will execute. Kubernetes incorporates load balancing, controls provider discovery, keeps observe of source allocation, and scales based on compute use. Also, it assesses the situation of every resource and provides systems the potential to self-fix by replicating containers or restarting them quickly.
Auditing Kubernetes
There are several policies that organizations need to comply with, dependent on the jurisdiction and sector in which they run. Some of these policies enhance the cyber resilience of the IT infrastructure, for illustration, PCI DSS and GDPR. The Kubernetes cluster is portion of the IT infrastructure, and businesses should really guarantee they comply with guidelines and security very best tactics where applicable.
Just one of the prerequisites that look in most IT plan paperwork is the log retention plan. Log retention procedures dictate how extensive you should really shop logs. You can use these logs to establish threats in the course of energetic checking and incident investigation.
Directors interact with the Kubernetes cluster through the Kubernetes API, and the cluster can log all API requests and responses. You can detect unconventional or unwelcome API phone calls from the Kubernetes audit logs. In a lot more detail, you can get alerts for functions such as authentication failure, container generation, modification, and deletion. The Kubernetes audit logging feature is disabled by default. For that reason, you require to get some required techniques to convert it on.
Making use of Wazuh to monitor and archive Kubernetes audit logs
You require to monitor the audit logs to detect security threats and anomalies. Also, you have to have to index the logs to look for for suitable information during an incident investigation. Wazuh displays, suppliers, and indexes the Kubernetes audit logs. Wazuh is an open resource unified XDR and SIEM system. It is commercially free and has above 10 million yearly downloads.
The Wazuh improvement team has a thorough manual on auditing Kubernetes with Wazuh. The information particulars measures on how to do the following:
- Configure the Wazuh server to get and process the Kubernetes audit logs.
- Enable audit logs on the Kubernetes cluster and forward them to the Wazuh server.
You can generate custom made principles to cause alerts when Wazuh detects precise situations in the Kubernetes audit log. For case in point, you can create regulations to set off alerts when resources are created or deleted on the Kubernetes cluster.
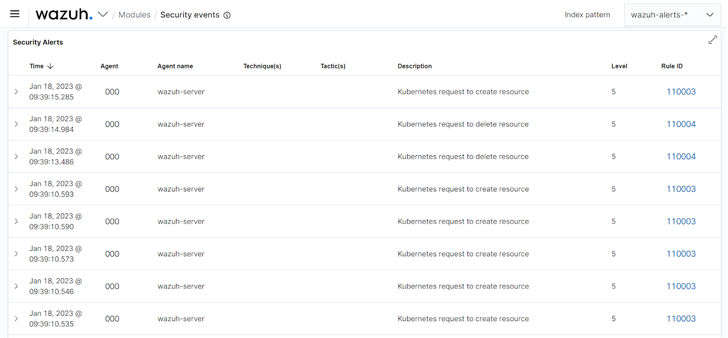 Determine 1: Alerts induced from Kubernetes audit logs on the Wazuh dashboard
Determine 1: Alerts induced from Kubernetes audit logs on the Wazuh dashboard
You can configure Wazuh to display screen all archived logs on the dashboard. These are logs of Kubernetes activities that did not cause an inform.
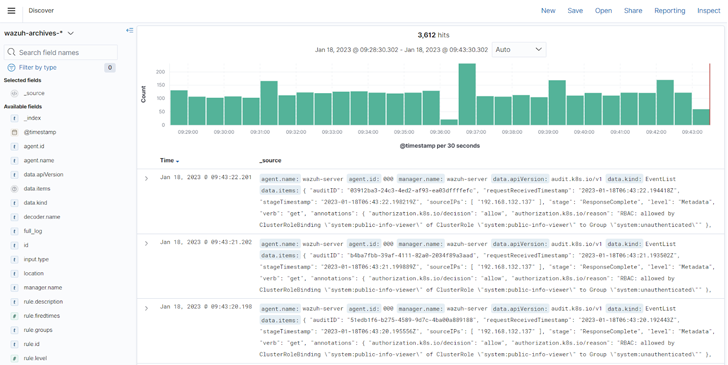 Determine 2: Kubernetes audit log archive on the Wazuh dashboard
Determine 2: Kubernetes audit log archive on the Wazuh dashboard
The Wazuh indexer is a remarkably scalable entire-textual content look for and analytics engine. The indexer indexes and stores the Kubernetes audit logs to provide you with genuine-time info research and analytics capabilities. The Wazuh indexer boosts performance during an incident investigation when you want to retrieve appropriate details from the audit logs.
Summary
Kubernetes is greatly used to deploy, scale, and regulate applications. You should keep Kubernetes audit logs for security and compliance reasons. The audit logs include information that can show uncommon or unwelcome activities. Wazuh is an open resource XDR and SIEM alternative that monitors, archives, and queries Kubernetes audit logs to recognize security threats and other anomalies. Wazuh also safeguards other factors of an IT infrastructure, which include endpoints and cloud workloads.
Wazuh has a large neighborhood of customers who support each individual other and enable to boost the solution. You can sign up for the Wazuh group to add to the item and ask for assist for any issues you could have.
Found this post fascinating? Observe us on Twitter and LinkedIn to examine more exclusive content we put up.
Some elements of this posting are sourced from:
thehackernews.com


 What is Apple’s T2 security chip?
What is Apple’s T2 security chip?