A wave of Gootkit malware loader attacks has focused the Australian health care sector by leveraging reputable equipment like VLC Media Player.
Gootkit, also named Gootloader, is recognised to make use of research engine optimization (Seo) poisoning tactics (aka spamdexing) for initial entry. It typically performs by compromising and abusing reputable infrastructure and seeding these web pages with prevalent keyword phrases.
Like other malware of its type, Gootkit is capable of stealing info from the browser, executing adversary-in-the-browser (AitB) attacks, keylogging, getting screenshots, and other destructive actions.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Trend Micro’s new results reveal that the key phrases “hospital,” “wellbeing,” “medical,” and “business agreement” have been paired with several city names in Australia, marking an malware’s expansion outside of accounting and law firms.
The starting position of the cyber assault is to immediate consumers hunting for the same keywords and phrases to an contaminated WordPress web site that tips them into downloading malware-laced ZIP information.
“Upon accessing the site, the consumer is introduced with a display screen that has been produced to appear like a legitimate discussion board,” Craze Micro researchers stated. “Users are led to accessibility the backlink so that the malicious ZIP file can be downloaded.”
What’s extra, the JavaScript code that is applied to pull off this trickery is injected into a legitimate JavaScript file at random sections on the breached internet site.
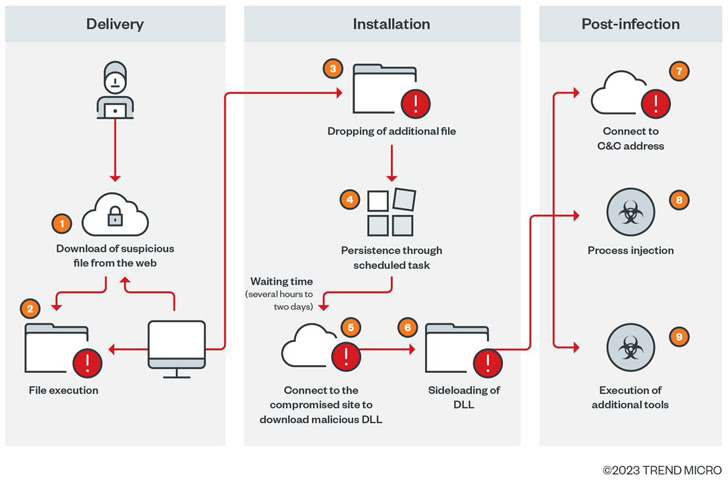
The downloaded ZIP archive, for its element, also incorporates a JavaScript file that, on execution, not only employs obfuscation to evade assessment, but is even more made use of to establish persistence on the device by implies of a scheduled job.
The execution chain subsequently sales opportunities to a PowerShell script which is designed to retrieve data files from a distant server for write-up-exploitation activity, which commences only immediately after a ready time period that ranges from a couple of hours to as extensive as two times.
“This latency, which obviously separates the initial an infection phase from the next stage, is a distinct function of Gootkit loader’s operation,” the scientists mentioned.
The moment the wait time elapses, two supplemental payloads are dropped – msdtc.exe and libvlc.dll – the previous of which is a genuine VLC Media Player binary which is employed to load the Cobalt Strike DLL part, followed by downloading far more applications to aid discovery.
“The malicious actors driving [Gootkit] are actively employing their marketing campaign,” the researchers reported. “The threats targeting precise task sectors, industries, and geographic spots are becoming far more aggressive.”
Identified this post intriguing? Adhere to us on Twitter and LinkedIn to go through more exclusive content material we put up.
Some sections of this post are sourced from:
thehackernews.com


 Customer and Employee Data the Top Prize for Hackers – Imperva
Customer and Employee Data the Top Prize for Hackers – Imperva