New cybersecurity investigation has located that command-line interface (CLI) applications from Amazon Web Expert services (AWS) and Google Cloud can expose delicate qualifications in construct logs, posing sizeable dangers to businesses.
The vulnerability has been codenamed LeakyCLI by cloud security company Orca.
“Some commands on Azure CLI, AWS CLI, and Google Cloud CLI can expose sensitive details in the variety of natural environment variables, which can be gathered by adversaries when printed by resources these types of as GitHub Steps,” security researcher Roi Nisimi claimed in a report shared with The Hacker News.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Microsoft has due to the fact resolved the issue as portion of security updates introduced in November 2023, assigned it the CVE identifier CVE-2023-36052 (CVSS rating: 8.6).

The thought, in a nutshell, has to do with how the CLI commands these types of as could be utilized to demonstrate (pre-)outlined natural environment variables and output to Continuous Integration and Steady Deployment (CI/CD) logs. A list of this kind of instructions spanning AWS and Google Cloud is down below
- aws lambda get-perform-configuration
- aws lambda get-function
- aws lambda update-functionality-configuration
- aws lambda update-perform-code
- aws lambda publish-version
- gcloud functions deploy
–set-env-vars - gcloud features deploy
–update-env-vars - gcloud functions deploy
–clear away-env-vars
Orca reported it observed several initiatives on GitHub that inadvertently leaked entry tokens and other delicate facts via Github Steps, CircleCI, TravisCI, and Cloud Develop logs.

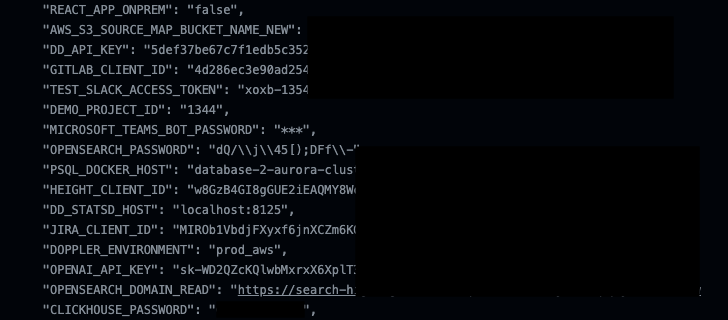
Unlike Microsoft, however, both Amazon and Google look at this to be predicted behavior, demanding that organizations consider methods to avoid storing secrets and techniques in environment variables and as an alternative use a dedicated secrets and techniques retail store company like AWS Techniques Supervisor or Google Cloud Top secret Manager.

Google also endorses the use of the “–no-consumer-output-enabled” choice to suppress the printing of command output to typical output and normal error in the terminal.
“If bad actors get their fingers on these ecosystem variables, this could possibly direct to check out delicate info together with credentials, these as passwords, person names, and keys, which could make it possible for them to entry any assets that the repository owners can,” Nisimi stated.
“CLI commands are by default assumed to be operating in a secure environment, but coupled with CI/CD pipelines, they might pose a security danger.”
Located this write-up exciting? Stick to us on Twitter and LinkedIn to read through far more special material we post.
Some areas of this post are sourced from:
thehackernews.com


 Widely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack
Widely-Used PuTTY SSH Client Found Vulnerable to Key Recovery Attack