The recent attack towards Microsoft’s email infrastructure by a Chinese country-condition actor referred to as Storm-0558 is claimed to have a broader scope than earlier imagined.
According to cloud security firm Wiz, the inactive Microsoft account (MSA) purchaser signing critical used to forge Azure Energetic Directory (Azure Advert or AAD) tokens to obtain illicit obtain to Outlook Web Accessibility (OWA) and Outlook.com could also have permitted the adversary to forge accessibility tokens for many forms of Azure Ad programs.
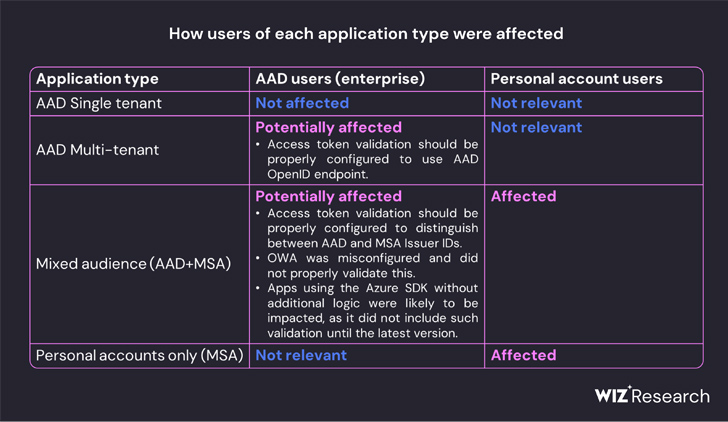
This incorporates every single software that supports private account authentication, these kinds of as OneDrive, SharePoint, and Groups consumers purposes that assistance the “Login with Microsoft performance,” and multi-tenant purposes in specified problems.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
“Every thing in the world of Microsoft leverages Azure Active Directory auth tokens for access,” Ami Luttwak, chief technology officer and co-founder of Wiz, stated in a assertion. “An attacker with an AAD signing key is the most strong attacker you can picture, mainly because they can access nearly any application – as any person. This is a ‘shape shifter’ superpower.”
Microsoft, last 7 days, disclosed the token forging method was exploited by Storm-0558 to extract unclassified information from victim mailboxes, but the specific contours of the cyber espionage marketing campaign continues to be unfamiliar.
The Windows maker mentioned it is nevertheless investigating as to how the adversary managed to receive the MSA purchaser signing crucial. But it truly is unclear if the critical functioned as a learn important of types to unlock entry to data belonging to almost two dozen corporations.
Wiz’s investigation fills in some of the blanks, with the organization finding that “all Azure particular account v2. apps depend on a record of 8 public keys, and all Azure multi-tenant v2. applications with Microsoft account enabled rely on a record of 7 general public keys.”
It even further observed that Microsoft changed one particular of the the shown community keys (thumbprint: “d4b4cccda9228624656bff33d8110955779632aa”) that experienced been current since at the very least 2016 someday between June 27, 2023, and July 5, 2023, close to the identical period of time the organization said it experienced revoked the MSA crucial.
“This led us to believe that whilst the compromised critical acquired by Storm-0558 was a personal important developed for Microsoft’s MSA tenant in Azure, it was also ready to signal OpenID v2. tokens for many varieties of Azure Energetic Listing programs,” Wiz said.
Impending WEBINARShield Towards Insider Threats: Master SaaS Security Posture Administration
Worried about insider threats? We’ve received you coated! Be part of this webinar to take a look at simple tactics and the secrets and techniques of proactive security with SaaS Security Posture Administration.
Sign up for Now
“Storm-0558 seemingly managed to attain accessibility to a single of numerous keys that ended up intended for signing and verifying AAD obtain tokens. The compromised vital was trusted to signal any OpenID v2. access token for particular accounts and blended-audience (multi-tenant or personal account) AAD applications.”
This successfully usually means that it could theoretically allow malicious actors to forge entry tokens for use by any software that depends on the Azure identity system.
Even even worse, the obtained private key could have been weaponized to forge tokens to authenticate as any consumer to an impacted application that trusts Microsoft OpenID v2. mixed audience and private-accounts certificates.
“Identity provider’s signing keys are probably the most effective secrets in the present day environment,” Wiz security researcher Shir Tamari said. “With identification service provider keys, one can acquire instant solitary hop obtain to anything, any email box, file provider, or cloud account.”
Observed this posting exciting? Comply with us on Twitter and LinkedIn to go through far more exclusive written content we post.
Some sections of this posting are sourced from:
thehackernews.com


 HotRat: New Variant of AsyncRAT Malware Spreading Through Pirated Software
HotRat: New Variant of AsyncRAT Malware Spreading Through Pirated Software