Microsoft is warning about the probable abuse of Azure Services Tags by destructive actors to forge requests from a trusted provider and get about firewall guidelines, thus allowing for them to get unauthorized entry to cloud means.
“This scenario does emphasize an inherent risk in making use of company tags as a single mechanism for vetting incoming network website traffic,” the Microsoft Security Response Centre (MSRC) said in a advice issued past 7 days.
“Service tags are not to be addressed as a security boundary and really should only be employed as a routing system in conjunction with validation controls. Assistance tags are not a complete way to secure site visitors to a customer’s origin and do not replace enter validation to protect against vulnerabilities that could be related with web requests.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

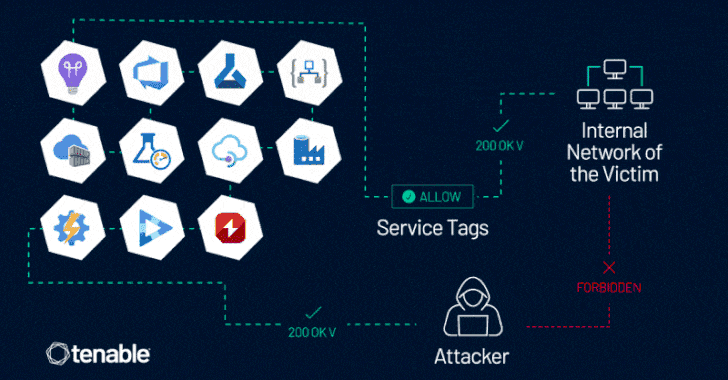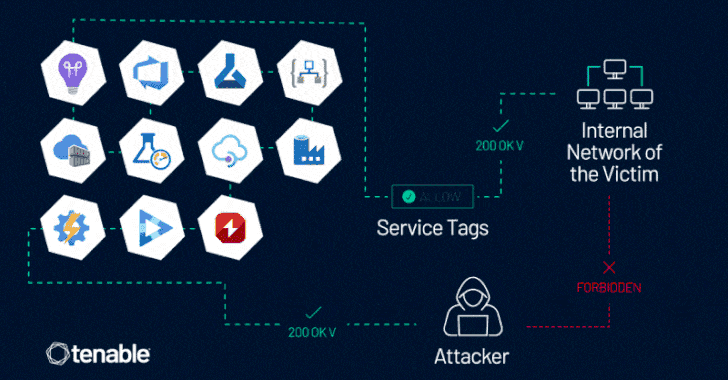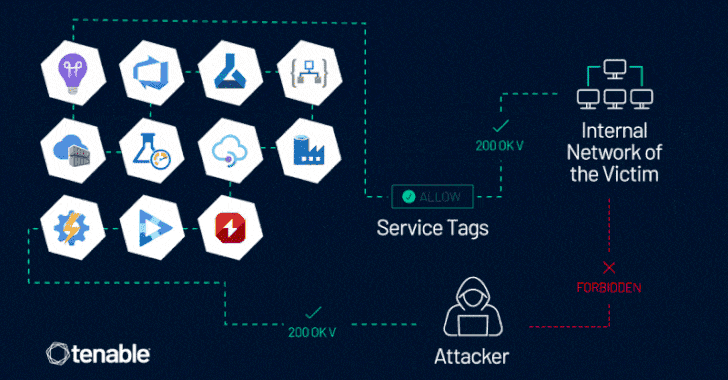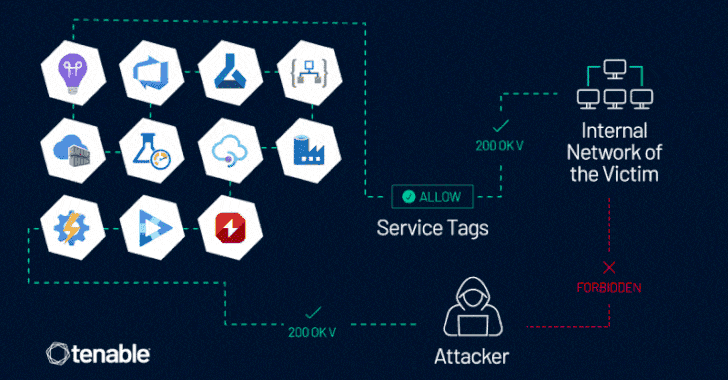
The assertion comes in response to findings from cybersecurity firm Tenable, which found that Azure clients whose firewall regulations count on Azure Service Tags could be bypassed. There is no proof that the attribute has been exploited in the wild.
The challenge, at its main, stems from the actuality that some of the Azure expert services enable inbound site visitors by using a provider tag, potentially letting an attacker in one tenant to send out specifically crafted web requests to access methods in another, assuming it has been configured to enable website traffic from the provider tag and does not perform any authentication of its have.
At 10 Azure solutions have been uncovered vulnerable: Azure Software Insights, Azure DevOps, Azure Machine Studying, Azure Logic Applications, Azure Container Registry, Azure Load Screening, Azure API Administration, Azure Knowledge Manufacturing unit, Azure Action Team, Azure AI Video clip Indexer, and Azure Chaos Studio.
“This vulnerability allows an attacker to management server-facet requests, as a result impersonating reliable Azure providers,” Tenable researcher Liv Matan mentioned. “This enables the attacker to bypass network controls based mostly on Company Tags, which are often made use of to prevent community entry to Azure customers’ inner belongings, data, and products and services.”
In reaction to the disclosure in late January 2024, Microsoft has up-to-date the documentation to explicitly note that “Service Tags alone aren’t sufficient to secure traffic devoid of looking at the nature of the provider and the traffic it sends.”
It really is also advised that consumers evaluate their use of services tags and guarantee they have adopted sufficient security guardrails to authenticate only dependable network targeted visitors for provider tags.
Located this report exciting? Adhere to us on Twitter and LinkedIn to go through a lot more special articles we submit.
Some pieces of this report are sourced from:
thehackernews.com

 Google Takes Down Influence Campaigns Tied to China, Indonesia, and Russia
Google Takes Down Influence Campaigns Tied to China, Indonesia, and Russia