A number of danger actors have capitalized on the leak of Babuk (aka Babak or Babyk) ransomware code in September 2021 to build as many as nine distinctive ransomware households able of targeting VMware ESXi devices.
“These variants emerged by means of H2 2022 and H1 2023, which shows an growing craze of Babuk source code adoption,” SentinelOne security researcher Alex Delamotte explained in a report shared with The Hacker News.
“Leaked resource code permits actors to focus on Linux devices when they could if not deficiency know-how to establish a operating plan.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A range of cybercrime teams, the two big and little, have set their sights on ESXi hypervisors. What’s much more, at least a few different ransomware strains – Cylance, Rorschach (aka BabLock), RTM Locker – that have emerged considering that the begin of the year are dependent on the leaked Babuk supply code.

SentinelOne’s latest evaluation demonstrates that this phenomenon is additional typical, with the cybersecurity organization pinpointing source code overlaps among Babuk and ESXi lockers attributed to Conti and REvil (aka REvix).
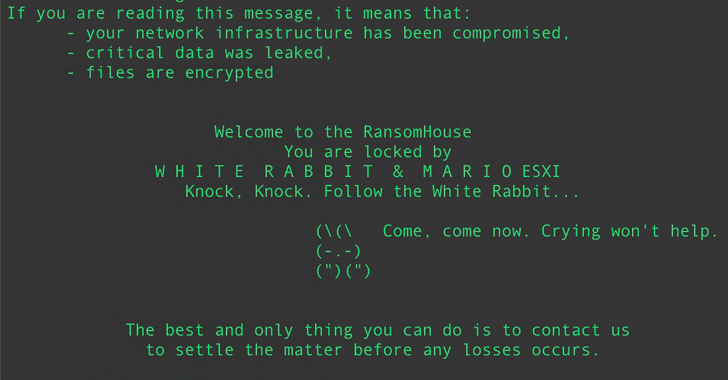
Other ransomware family members that have ported many attributes from Babuk into their respective code incorporate LOCK4, DATAF, Mario, Participate in, and Babuk 2023 (aka XVGV) ransomware.
Even with this visible development, SentinelOne claimed it noticed no parallels in between Babuk and ALPHV, Black Basta, Hive, and LockBit’s ESXi lockers, including it discovered “tiny similarity” in between ESXiArgs and Babuk, indicating an faulty attribution.
“Based on the popularity of Babuk’s ESXi locker code, actors could also change to the group’ Go-primarily based NAS locker,” Delamotte claimed. “Golang stays a market option for lots of
actors, but it carries on to increase in reputation.”
Approaching WEBINARLearn to Cease Ransomware with Authentic-Time Safety
Sign up for our webinar and master how to quit ransomware attacks in their tracks with true-time MFA and services account security.
Conserve My Seat!
The development comes as risk actors affiliated with Royal ransomware, who are suspected to be previous Conti members, have expanded their attack toolkit with an ELF variant which is capable of placing Linux and ESXi environments.
“The ELF variant is fairly identical to the Windows variant, and the sample does not incorporate any obfuscation,” Palo Alto Networks Device 42 stated in a produce-up published this 7 days. “All strings, together with the RSA public crucial and ransom note, are stored as plaintext.”
Royal ransomware attacks are facilitated by implies of several first entry vectors these kinds of as callback phishing, BATLOADER bacterial infections, or compromised qualifications, which is then abused to fall a Cobalt Strike Beacon as a precursor to ransomware execution.
Because bursting on the scene in September 2022, Royal ransomware has claimed accountability for targeting 157 businesses on their leak internet site, with most of the attacks concentrating on manufacturing, retail, legal solutions, education and learning, building, and healthcare expert services in the U.S., Canada, and Germany.
Identified this short article appealing? Observe us on Twitter and LinkedIn to read through far more unique written content we put up.
Some elements of this write-up are sourced from:
thehackernews.com

 NCSC and ICO Dispel Incident Reporting Myths
NCSC and ICO Dispel Incident Reporting Myths