New findings about a hacker team joined to cyber attacks concentrating on companies in the Russo-Ukrainian conflict space reveal that it may well have been all around for significantly more time than earlier imagined.
The danger actor, tracked as Lousy Magic (aka Red Stinger), has not only been linked to a fresh subtle marketing campaign, but also to an action cluster that initial arrived to gentle in May possibly 2016.
“Though the past targets had been largely situated in the Donetsk, Luhansk, and Crimea locations, the scope has now widened to include folks, diplomatic entities, and exploration companies in Western and Central Ukraine,” Russian cybersecurity agency Kaspersky claimed in a technological report published past week.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The campaign is characterised by the use of a novel modular framework codenamed CloudWizard, which functions capabilities to get screenshots, history microphone, log keystrokes, get passwords, and harvest Gmail inboxes.
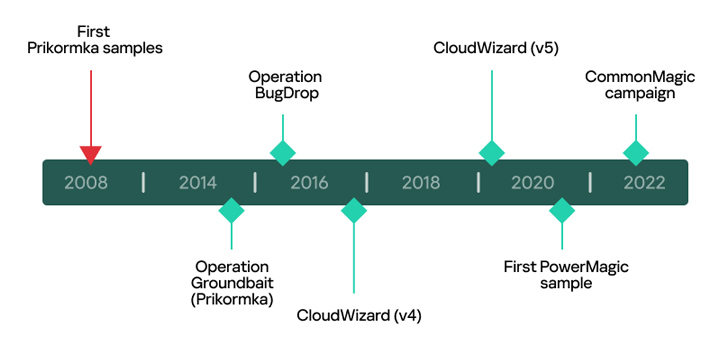
Terrible Magic was initially documented by the enterprise in March 2023, detailing the group’s use of a backdoor called PowerMagic (aka DBoxShell or GraphShell) and a modular framework dubbed CommonMagic in attacks focusing on Russian-occupied territories of Ukraine.
Then earlier this month, Malwarebytes exposed at minimum 5 waves of espionage attacks mounted by the group dating back again to December 2020.
The deeper insight shared by Kaspersky connects Lousy Magic to prior exercise primarily based on combing by historic telemetry facts, allowing the corporation to recognize numerous artifacts connected with the CloudWizard framework.
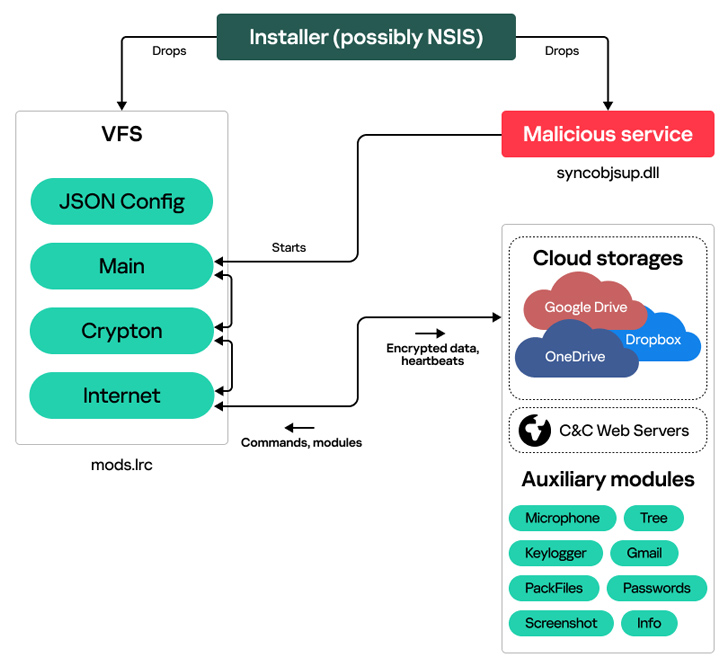
The original access vector utilized to fall the first-stage installer is at present unknown. That explained, the malware is configured to drop a Windows company (“syncobjsup.dll”) and a next file (“mods.lrc”), which, in switch, contains 3 various modules to harvest and exfiltrate sensitive facts.
The details is transmitted in encrypted kind to an actor-managed cloud storage endpoint (OneDrive, Dropbox, or Google Travel). A web server is applied as a fallback mechanism in the function none of the expert services are obtainable.
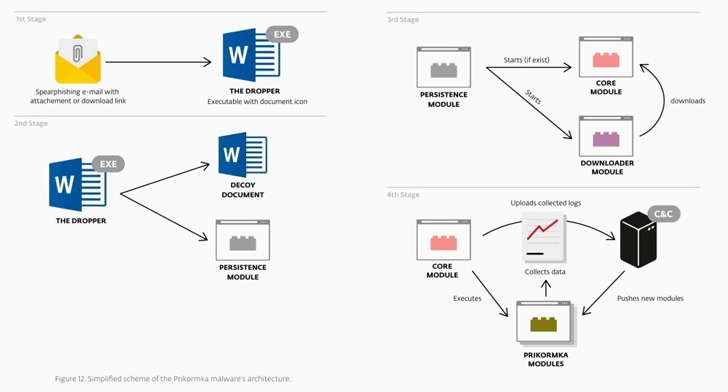
Kaspersky reported it determined resource code overlaps concerning an more mature model of CloudWizard and an additional malware known as Prikormka, which was uncovered by Slovak cybersecurity business ESET in 2016.
 Impression Supply: ESET
Impression Supply: ESET
The espionage marketing campaign, monitored by ESET beneath the moniker Procedure Groundbait, primarily singled out anti-governing administration separatists in Donetsk and Luhansk and Ukrainian authorities officers, politicians, and journalists.
Prikormka is deployed by means of a dropper contained in malicious email attachments and characteristics 13 various parts to harvest numerous kinds of knowledge from compromised equipment. Proof collected by ESET shows that the malware has been selectively utilised since at least 2008.
Future WEBINARZero Belief + Deception: Discover How to Outsmart Attackers!
Find out how Deception can detect innovative threats, halt lateral motion, and enrich your Zero Have faith in technique. Sign up for our insightful webinar!
Conserve My Seat!
CloudWizard also exhibits resemblances with a connected intrusion set referred to as BugDrop that was disclosed by CyberX (which has since been acquired by Microsoft) in 2017, with the industrial cybersecurity corporation describing it as extra advanced than Groundbait.
Commonalities have also been unearthed in between CloudWizard and CommonMagic, including victimology and supply code overlaps, indicating that the threat actor has been frequently tweaking its malware arsenal and infecting targets for about 15 a long time.
The newest advancement, in attributing the CloudWizard framework to the actor powering Operation Groundbait and Operation BugDrop, provides still yet another piece to the puzzle that hopes to eventually reveal the even bigger photograph of the mysterious group’s origins.
“The danger actor accountable for these operations has demonstrated a persistent and ongoing motivation to cyberespionage, repeatedly enhancing their toolset and targeting companies of fascination for above 15 decades,” Kaspersky researcher Georgy Kucherin claimed.
“Geopolitical things proceed to be a substantial motivator for APT attacks and, supplied the prevailing pressure in the Russo-Ukrainian conflict place, we anticipate that this actor will persist with its operations for the foreseeable long term.”
Identified this post attention-grabbing? Observe us on Twitter and LinkedIn to browse much more exceptional content material we article.
Some pieces of this short article are sourced from:
thehackernews.com

 Meta Fined €1.2bn for Violating GDPR
Meta Fined €1.2bn for Violating GDPR