Menace hunters have shed light on the methods, procedures, and processes embraced by an Indian-origin hacking group called Patchwork as aspect of a renewed campaign that commenced in late November 2021, concentrating on Pakistani govt entities and persons with a analysis concentrate on molecular drugs and organic science.
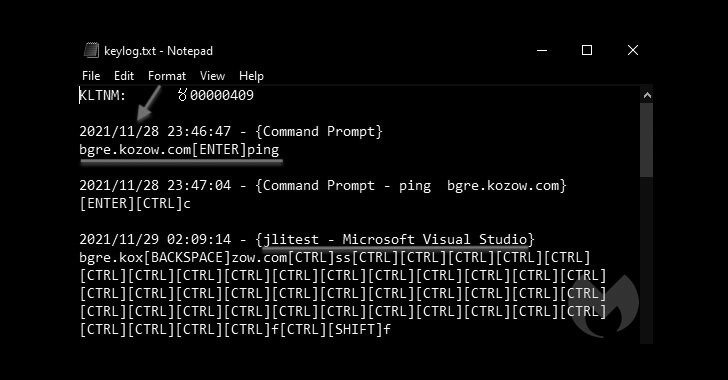
“Ironically, all the info we collected was possible many thanks to the risk actor infecting them selves with their have [remote access trojan], ensuing in captured keystrokes and screenshots of their own personal computer and virtual machines,” Malwarebytes Threat Intelligence Group claimed in a report printed on Friday.
Well known victims that ended up productively infiltrated consist of Pakistan’s Ministry of Protection, Nationwide Defence University of Islamabad, School of Bio-Sciences at UVAS Lahore, Intercontinental Center for Chemical and Biological Sciences (ICCBS), H.E.J. Investigation Institute of Chemistry, and the Salim Habib College (SBU).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

Believed to have been active considering that 2015, Patchwork APT is also tracked by the wider cybersecurity neighborhood under the monikers Dropping Elephant, Chinastrats (Kaspersky), Quilted Tiger (CrowdStrike), Monsoon (Forcepoint), Zinc Emerson, TG-4410 (SecureWorks), and APT-C-09 (Qihoo 360).
The espionage group, primarily identified for hanging diplomatic and authorities organizations in Pakistan, China, U.S. consider tanks, and other targets located in the Indian subcontinent through spear-phishing strategies, receives its identify from the actuality that most of the code applied for its malware tooling was copied and pasted from numerous resources publicly available on the web.
“The code utilized by this danger actor is copy-pasted from a variety of on line message boards, in a way that reminds us of a patchwork quilt,” researchers from the now-defunct Israeli cybersecurity startup Cymmetria mentioned in its findings revealed in July 2016.
Above the decades, successive covert functions staged by the actor have attempted to fall and execute QuasarRAT as properly as an implant named BADNEWS that functions as a backdoor for the attackers, providing them with whole control above the sufferer machine. In January 2021, the danger group was also observed exploiting a remote code execution vulnerability in Microsoft Workplace (CVE-2017-0261) to deliver payloads on sufferer equipment.
The newest campaign is no unique in that the adversary lures potential targets with RTF paperwork impersonating Pakistani authorities that ultimately act as a conduit for deploying a new variant of the BADNEWS trojan named Ragnatela — which means “spider web” in Italian — enabling the operators to execute arbitrary commands, capture keystrokes and screenshots, checklist and upload files, and down load added malware.
The new lures, which purport to be from the Pakistan Defence Officers Housing Authority (DHA) in Karachi, contains an exploit for Microsoft Equation Editor that’s induced to compromise the victim’s computer and execute the Ragnatela payload.
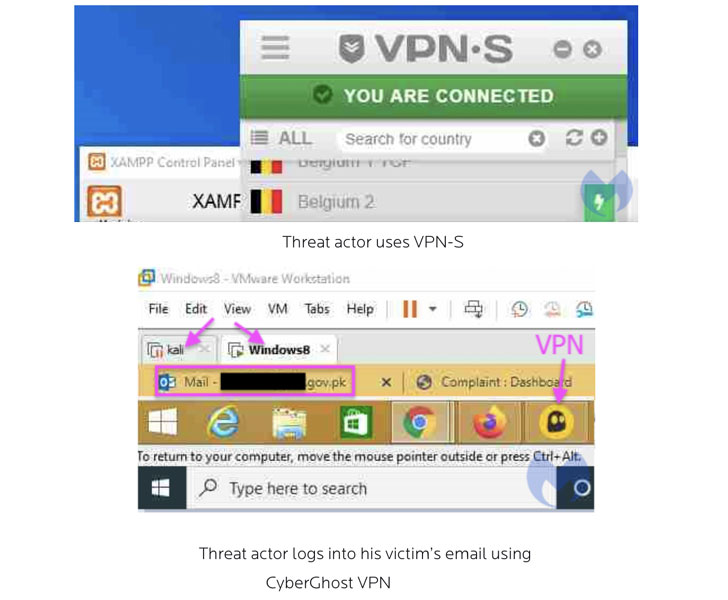
But in what’s a case of OpSec failure, the threat actor also ended up infecting their possess enhancement machine with the RAT, as Malwarebytes was ready to unmask a amount of its ways, which include the use of twin keyboard layouts (English and Indian) as nicely as the adoption of virtual equipment and VPNs these kinds of as VPN Secure and CyberGhost to conceal their IP handle.
“Even though they carry on to use the identical lures and RAT, the team has revealed desire in a new form of target,” the researchers concluded. “In fact, this is the very first time we have observed Patchwork targeting molecular medicine and organic science scientists.”
Observed this article intriguing? Stick to THN on Facebook, Twitter and LinkedIn to examine more exclusive articles we publish.
Some sections of this posting are sourced from:
thehackernews.com


 Facebook Launches ‘Privacy Center’ to Educate Users on Data Collection and Privacy Options
Facebook Launches ‘Privacy Center’ to Educate Users on Data Collection and Privacy Options