Cybersecurity scientists stated they have found out what they say is the to start with open-source software provide chain attacks precisely concentrating on the banking sector.
“These attacks showcased sophisticated strategies, together with focusing on specific components in web property of the sufferer bank by attaching malicious functionalities to it,” Checkmarx claimed in a report printed previous week.
“The attackers used deceptive techniques these kinds of as developing a phony LinkedIn profile to surface credible and custom made command-and-handle (C2) centers for every single concentrate on, exploiting genuine companies for illicit functions.”

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The npm deals have due to the fact been reported and taken down. The names of the deals were being not disclosed.
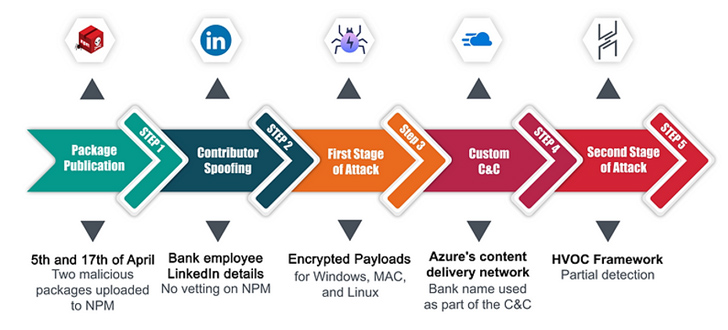
In the first attack, the malware creator is said to have uploaded a couple of offers to the npm registry in early April 2023 by posing as an personnel of the focus on bank. The modules arrived with a preinstall script to activate the an infection sequence. To entire the ruse, the danger actor guiding it made a faux LinkedIn site.
The moment introduced, the script identified the host functioning procedure to see if it was Windows, Linux, or macOS, and proceeded to obtain a 2nd-phase malware from a remote server by using a subdomain on Azure that integrated the name of the financial institution in question.
“The attacker cleverly used Azure’s CDN subdomains to proficiently provide the next-stage payload,” Checkmarx researchers mentioned. “This tactic is significantly clever since it bypasses classic deny list techniques, thanks to Azure’s standing as a reputable services.”
The next-stage payload made use of in the intrusion is Havoc, an open up-resource command-and-handle (C2) framework that has more and more arrive less than the radar of malicious actors wanting to sidestep detection stemming from the use of Cobalt Strike, Sliver, and Brute Ratel.
In an unrelated attack detected in February 2023 focusing on a diverse financial institution, the adversary uploaded to npm a package that was “meticulously intended to blend into the website of the sufferer financial institution and lay dormant until finally it was prompted to spring into action.”
Specially, it was engineered to covertly intercept login knowledge and exfiltrate the aspects to an actor-managed infrastructure.
“Offer chain security revolves around preserving the complete process of application development and distribution, from the beginning phases of enhancement to the shipping to the conclude user,” the firm claimed.
“The moment a destructive open-resource package deal enters the pipeline, it truly is in essence an instantaneous breach – rendering any subsequent countermeasures ineffective. In other words and phrases, the problems is carried out.”
The development will come as the Russian-speaking cybercrime team RedCurl breached an unnamed important Russian bank and an Australian organization in November 2022 and May 2023 to siphon company tricks and personnel information as part of a complex phishing campaign, Group-IB’s Russian arm, F.A.C.C.T., explained.
“Above the previous four and a fifty percent several years, the Russian-talking group Purple Curl […] has carried out at minimum 34 attacks on organizations from the UK, Germany, Canada, Norway, Ukraine, and Australia,” the organization explained.
Future WEBINARShield From Insider Threats: Master SaaS Security Posture Management
Anxious about insider threats? We’ve received you included! Be a part of this webinar to investigate simple tactics and the secrets and techniques of proactive security with SaaS Security Posture Management.
Be a part of These days
“Additional than fifty percent of the attacks – 20 – fell on Russia. Between the victims of cyber spies had been development, economic, consulting businesses, retailers, banking institutions, insurance plan, and legal organizations.”
Financial establishments have also been at the receiving conclusion of attacks leveraging a web-inject toolkit identified as drIBAN to execute unauthorized transactions from a victim’s pc in a fashion that circumvents identity verification and anti-fraud mechanisms adopted by banking institutions.
“The main operation of drIBAN is the ATS engine (Automated Transfer Method),” Cleafy researchers Federico Valentini and Alessandro Strino pointed out in an analysis unveiled on July 18, 2023.
“ATS is a course of web injects that alters on-the-fly legitimate banking transfers carried out by the user, shifting the beneficiary and transferring cash to an illegitimate financial institution account managed by TA or affiliate marketers, which are then liable for dealing with and laundering the stolen cash.”
Located this write-up intriguing? Stick to us on Twitter and LinkedIn to read more distinctive written content we publish.
Some parts of this article are sourced from:
thehackernews.com


 Apple Threatens to Pull iMessage and FaceTime from U.K. Amid Surveillance Demands
Apple Threatens to Pull iMessage and FaceTime from U.K. Amid Surveillance Demands