Risk actors are resorting to YouTube films that includes written content related to cracked software program in order to entice users into downloading an information stealer malware identified as Lumma.
“These YouTube video clips normally feature material similar to cracked applications, presenting consumers with related set up guides and incorporating malicious URLs frequently shortened making use of services like TinyURL and Cuttly,” Fortinet FortiGuard Labs researcher Cara Lin stated in a Monday investigation.
This is not the first time pirated software program movies on YouTube have emerged as an helpful bait for stealer malware. Formerly comparable attack chains were noticed delivering stealers, clippers, and crypto miner malware.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

In accomplishing so, menace actors can leverage the compromised devices for not only data and cryptocurrency theft, but also abuse the resources for illicit mining.
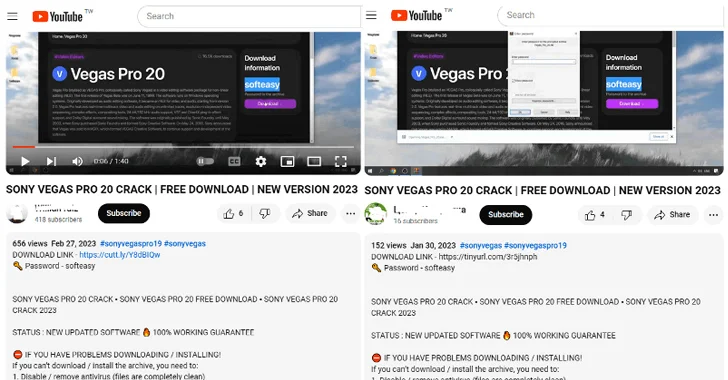
In the most current attack sequence documented by Fortinet, users browsing for cracked variations of respectable online video editing equipment like Vegas Pro on YouTube are prompted to click on a url located in the video’s description, major to the obtain of a bogus installer hosted on MediaFire.

The ZIP installer, the moment unpacked, options a Windows shortcut (LNK) masquerading as a set up file that downloads a .NET loader from a GitHub repository, which, in transform, loads the stealer payload, but not in advance of performing a sequence of anti-digital equipment and anti-debugging checks.
Lumma Stealer, penned in C and provided for sale on underground forums since late 2022, is able of harvesting and exfiltrating sensitive info to an actor-managed server.
The advancement arrives as Bitdefender warned of stream-jacking attacks on YouTube in which cybercriminals consider about high-profile accounts via phishing attacks that deploy the RedLine Stealer malware to siphon their credentials and session cookies, and ultimately endorse a variety of crypto frauds.

It also follows the discovery of an 11-month-outdated AsyncRAT marketing campaign that employs phishing lures to download an obfuscated JavaScript file which is then utilized to fall the remote accessibility trojan.
“The victims and their firms are meticulously chosen to broaden the impact of the marketing campaign,” AT&T Alien Labs researcher Fernando Martinez stated. “Some of the identified targets manage crucial infrastructure in the U.S.”
Identified this article fascinating? Stick to us on Twitter and LinkedIn to read through more exceptional written content we publish.
Some sections of this write-up are sourced from:
thehackernews.com

 Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals
Syrian Hackers Distributing Stealthy C#-Based Silver RAT to Cybercriminals