Risk actors have been observed serving malicious code by using Binance’s Smart Chain (BSC) contracts in what has been described as the “future stage of bulletproof hosting.”
The campaign, detected two months in the past, has been codenamed EtherHiding by Guardio Labs.
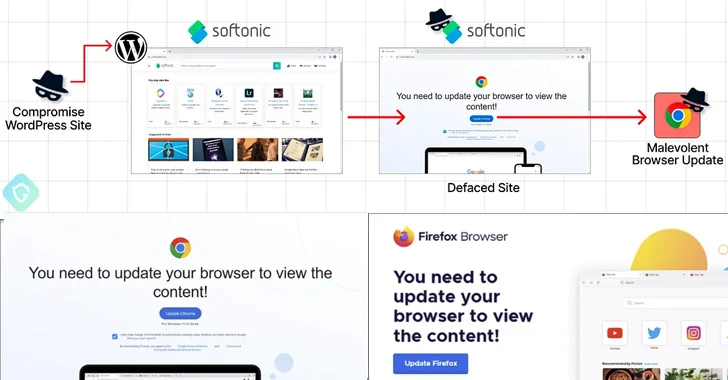
The novel twist marks the hottest iteration in an ongoing marketing campaign that leverages compromised WordPress web pages to provide unsuspecting site visitors a fake warning to update their browsers in advance of the internet sites can be accessed, finally main to the deployment of facts stealer malware such as Amadey, Lumma, or RedLine.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
“Even though their original system of hosting code on abused Cloudflare Employee hosts was taken down, they have immediately pivoted to acquire gain of the decentralized, anonymous, and community mother nature of blockchain,” security scientists Nati Tal and Oleg Zaytsev mentioned.

“This marketing campaign is up and more difficult than ever to detect and consider down.”
It’s no surprise that risk actors have specific WordPress web-sites by using both destructive plugins, as properly as take gain of publicly disclosed security flaws in well known plugins to breach web-sites. This offers the ability to entirely hijack infected web sites at will.
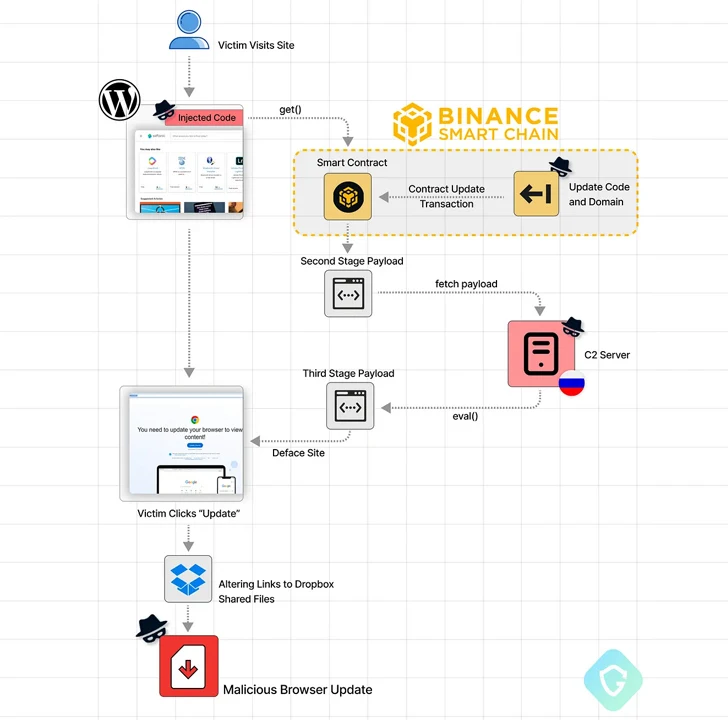
In the most current set of attacks, the contaminated internet sites are injected with obfuscated Javascript built to query the BNB Clever Chain by developing a good agreement with an attacker-managed blockchain address.
The purpose is to fetch a second-stage script that, in transform, retrieves a third-stage payload from a command-and-management (C2) server to provide the misleading browser update notices.
Should really a sufferer click on the update button on the bogus overlay, they are redirected to download a malicious executable from Dropbox or other legit file hosting products and services.

While the address and the related agreement have been tagged as used in a phishing plan, the consequence of hosting it on a decentralized services usually means that there is at present no way to intervene and disrupt the attack chain.
“As this is not an handle used in any financial or other action that victims can be lured to transfer cash or any other variety of Intellectual residence to — visitors of compromised WordPress web sites have no clue as to what is heading on underneath the hood,” the scientists stated.
“This deal, tagged as faux, malicious, or whatnot, is however on the web and delivers the malicious payload.”
With plugins becoming a sizable attack area for WordPress, it is suggested that people relying on the content administration procedure (CMS) adhere to security finest techniques and preserve their techniques up-to-day with the most current patches, take away undesirable admin consumers, and implement strong passwords.
Identified this article interesting? Adhere to us on Twitter and LinkedIn to read through extra distinctive written content we article.
Some sections of this article are sourced from:
thehackernews.com

 Microsoft to Phase Out NTLM in Favor of Kerberos for Stronger Authentication
Microsoft to Phase Out NTLM in Favor of Kerberos for Stronger Authentication