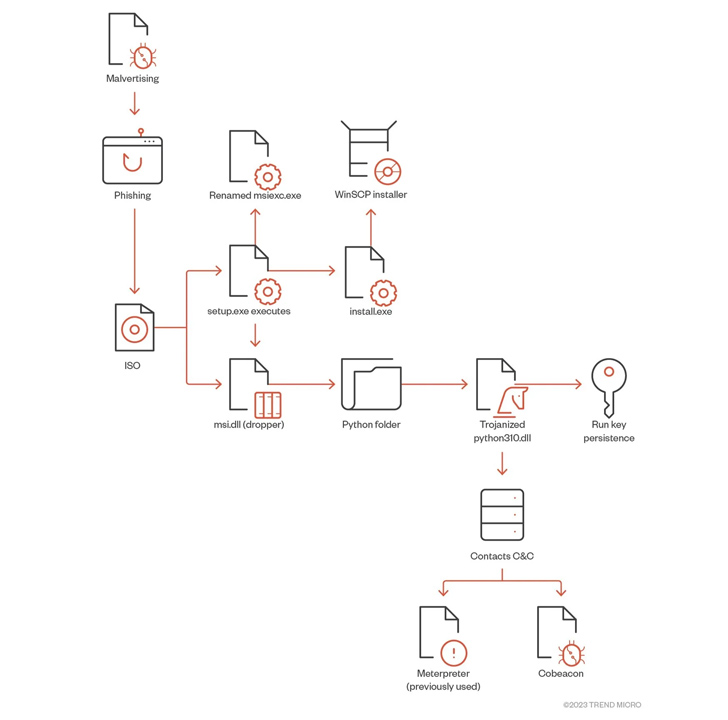
Risk actors involved with the BlackCat ransomware have been observed utilizing malvertising tips to distribute rogue installers of the WinSCP file transfer application.
“Malicious actors utilised malvertising to distribute a piece of malware by using cloned webpages of reputable organizations,” Development Micro researchers stated in an examination published last 7 days. “In this scenario, the distribution involved a webpage of the well-regarded software WinSCP, an open-source Windows software for file transfer.”
Malvertising refers to the use of Search engine optimisation poisoning approaches to distribute malware via on the net promoting. It usually consists of hijacking a chosen set of search phrases to display bogus adverts on Bing and Google lookup effects webpages with the objective of redirecting unsuspecting consumers to sketchy internet pages.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The concept is to trick people looking for applications like WinSCP into downloading malware, in this instance, a backdoor that includes a Cobalt Strike Beacon that connects to a remote server for follow-on operations, while also using reputable instruments like AdFind to facilitate network discovery.
The entry afforded by Cobalt Strike is further more abused to obtain a quantity of applications to perform reconnaissance, enumeration (PowerView), lateral motion (PsExec), bypass antivirus software package (KillAV BAT), and exfiltrate buyer knowledge (PuTTY Secure Copy customer). Also observed is the use of the Terminator protection evasion tool to tamper with security software program by suggests of a Carry Your Have Vulnerable Driver (BYOVD) attack.
In the attack chain in depth by the cybersecurity firm, the danger actors managed to steal top-degree administrator privileges to conduct publish-exploitation routines and attempted to established up persistence using remote checking and administration equipment like AnyDesk as well as entry backup servers.
“It is hugely probably that the enterprise would have been considerably affected by the attack if intervention experienced been sought afterwards, in particular due to the fact the risk actors experienced currently succeeded in gaining initial entry to area administrator privileges and started out setting up backdoors and persistence,” Trend Micro mentioned.
The enhancement is just the hottest illustration of threat actors leveraging the Google Ads platform to provide malware. In November 2022, Microsoft disclosed an attack marketing campaign that leverages the advertising assistance to deploy BATLOADER, which is then made use of to drop Royal ransomware.
It also arrives as Czech cybersecurity business Avast produced a free of charge decryptor for the fledgling Akira ransomware to assistance victims recuperate their info without obtaining to pay the operators. Akira, which 1st appeared in March 2023, has considering that expanded its concentrate on footprint to include Linux units.
“Akira has a number of similarities to the Conti v2 ransomware, which might show that the malware authors were at the very least impressed by the leaked Conti resources,” Avast scientists claimed. The corporation did not disclose how it cracked the ransomware’s encryption algorithm.
The Conti/TrickBot syndicate, aka Gold Ulrick or ITG23, shut down in May well 2022 after suffering a series of disruptive events induced by the onset of the Russian invasion of Ukraine. But the e-criminal offense group continues to exist to this day, albeit as more compact entities and employing shared crypters and infrastructure to distribute their warez.

IBM Security X-Pressure, in a the latest deep dive, claimed the gang’s crypters, which are apps built to encrypt and obfuscate malware to evade detection by antivirus scanners and hinder investigation, are getting employed to also disseminate new malware strains these as Aresloader, Canyon, CargoBay, DICELOADER, Lumma C2, Matanbuchus, Minodo (formerly Domino), Pikabot, SVCReady, Vidar.
“Earlier, the crypters have been utilized predominantly with the main malware households linked with ITG23 and their shut companions,” security researchers Charlotte Hammond and Ole Villadsen explained. “On the other hand, the fracturing of ITG23 and emergence of new factions, interactions, and solutions, have afflicted how the crypters are employed.”
Despite the dynamic character of the cybercrime ecosystem, as nefarious cyber actors come and go, and some operations associate jointly, shut down, or rebrand their economically enthusiastic schemes, ransomware continues to be a consistent threat.
This consists of the emergence of a new ransomware-as-a-assistance (RaaS) team identified as Rhysida, which has generally singled out education, govt, production, and technology sectors throughout Western Europe, North and South America, and Australia.
“Rhysida is a 64-bit Portable Executable (PE) Windows cryptographic ransomware software compiled utilizing MINGW/GCC,” SentinelOne said in a specialized publish-up. “In every sample analyzed, the application’s plan identify is set to Rhysida-.1, suggesting the resource is in early phases of progress.”
Located this write-up appealing? Follow us on Twitter and LinkedIn to study more special content material we put up.
Some sections of this posting are sourced from:
thehackernews.com

 Hackers Exploiting Unpatched WordPress Plugin Flaw to Create Secret Admin Accounts
Hackers Exploiting Unpatched WordPress Plugin Flaw to Create Secret Admin Accounts