A stealthy Unified Extensible Firmware Interface (UEFI) bootkit called BlackLotus has turn out to be the to start with publicly recognised malware capable of bypassing Secure Boot defenses, earning it a strong risk in the cyber landscape.
“This bootkit can run even on completely up-to-date Windows 11 units with UEFI Safe Boot enabled,” Slovak cybersecurity organization ESET claimed in a report shared with The Hacker News.
UEFI bootkits are deployed in the technique firmware and make it possible for comprehensive control about the functioning procedure (OS) boot system, therefore producing it possible to disable OS-degree security mechanisms and deploy arbitrary payloads in the course of startup with higher privileges.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Made available for sale at $5,000 (and $200 for each new subsequent variation), the effective and persistent toolkit is programmed in Assembly and C and is 80 kilobytes in sizing. It also capabilities geofencing capabilities to steer clear of infecting personal computers in Armenia, Belarus, Kazakhstan, Moldova, Romania, Russia, and Ukraine.
Specifics about BlackLotus to start with emerged in October 2022, with Kaspersky security researcher Sergey Lozhkin describing it as a complex crimeware resolution.
“This represents a bit of a ‘leap’ ahead, in conditions of simplicity of use, scalability, accessibility, and most importantly, the potential for much far more effects in the sorts of persistence, evasion, and/or destruction,” Eclypsium’s Scott Scheferman mentioned.
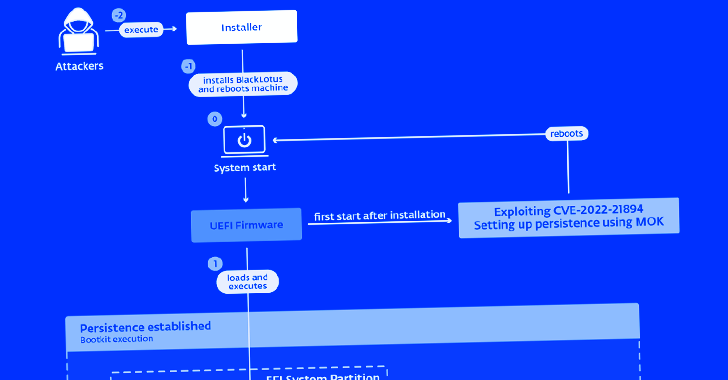
BlackLotus, in a nutshell, exploits a security flaw tracked as CVE-2022-21894 (aka Baton Drop) to get around UEFI Secure Boot protections and established up persistence. The vulnerability was tackled by Microsoft as aspect of its January 2022 Patch Tuesday update.
A profitable exploitation of the flaw lets arbitrary code execution during early boot phases, allowing a danger actor to have out destructive actions on a technique with UEFI Safe Boot enabled devoid of possessing bodily obtain to it, ESET reported.
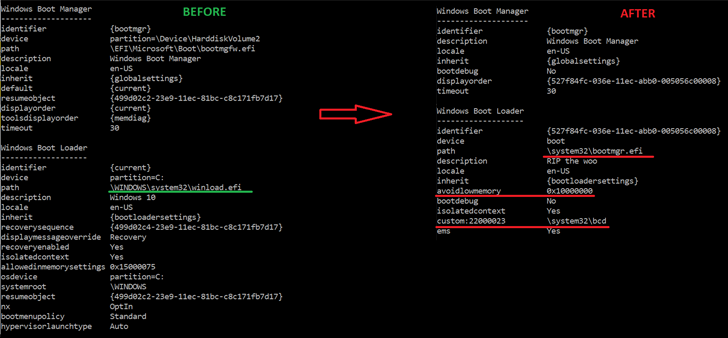
“This is the very first publicly identified, in-the-wild abuse of this vulnerability,” ESET researcher Martin Smolár mentioned. “Its exploitation is however probable as the affected, validly signed binaries have even now not been additional to the UEFI revocation list.”
“BlackLotus normally takes gain of this, bringing its personal copies of legitimate – but vulnerable – binaries to the system in buy to exploit the vulnerability,” properly paving the way for Convey Your Very own Susceptible Driver (BYOVD) attacks.
Moreover currently being outfitted to change off security mechanisms like BitLocker, Hypervisor-protected Code Integrity (HVCI), and Windows Defender, it really is also engineered to fall a kernel driver and an HTTP downloader that communicates with a command-and-regulate (C2) server to retrieve more user-method or kernel-method malware.
The correct modus operandi used to deploy the bootkit is unfamiliar as still, but it begins with an installer part that’s responsible for composing the data files to the EFI system partition, disabling HVCI and BitLocker, and then rebooting the host.
The restart is adopted by the weaponization of CVE-2022-21894 to achieve persistence and put in the bootkit, just after which it is immediately executed on every program begin to deploy the kernel driver.
Even though the driver is tasked with launching the person-method HTTP downloader and operating future-phase kernel-manner payloads, the latter is able of executing commands acquired from the C2 server around HTTPS.
This includes downloading and executing a kernel driver, DLL, or a standard executable fetching bootkit updates, and even uninstalling the bootkit from the infected technique.
“A lot of critical vulnerabilities affecting security of UEFI units have been learned in the final handful of yrs,” Smolár claimed. “Regrettably, thanks the complexity of the entire UEFI ecosystem and linked supply-chain troubles, quite a few of these vulnerabilities have still left several units vulnerable even a extensive time soon after the vulnerabilities have been set – or at the very least soon after we have been advised they had been fastened.”
“It was just a subject of time right before somebody would choose edge of these failures and generate a UEFI bootkit able of operating on programs with UEFI Secure Boot enabled.”
Identified this write-up exciting? Comply with us on Twitter and LinkedIn to go through far more distinctive information we write-up.
Some sections of this post are sourced from:
thehackernews.com

 CISOs Are Stressed Out and It’s Putting Companies at Risk
CISOs Are Stressed Out and It’s Putting Companies at Risk