The cyber espionage actor tracked as Blind Eagle has been connected to a new multi-phase attack chain that qualified prospects to the deployment of the NjRAT distant access trojan on compromised devices.
“The group is recognized for utilizing a range of complex attack strategies, including tailor made malware, social engineering tactics, and spear-phishing attacks,” ThreatMon said in a Tuesday report.
Blind Eagle, also referred to as APT-C-36, is a suspected Spanish-talking group that chiefly strikes personal and general public sector entities in Colombian. Attacks orchestrated by the group have also focused Ecuador, Chile, and Spain.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
An infection chains documented by Check Issue and BlackBerry this 12 months have discovered the use of spear-phishing lures to deliver commodity malware family members like BitRAT, AsyncRAT, and in-memory Python loaders able of launching a Meterpreter payload.
The hottest discovery from ThreatMon entails the use of a JavaScript downloader to execute a PowerShell script hosted in Discord CDN. The script, in switch, drops another PowerShell script and a Windows batch file, and will save a VBScript file in the Windows startup folder to achieve persistence.
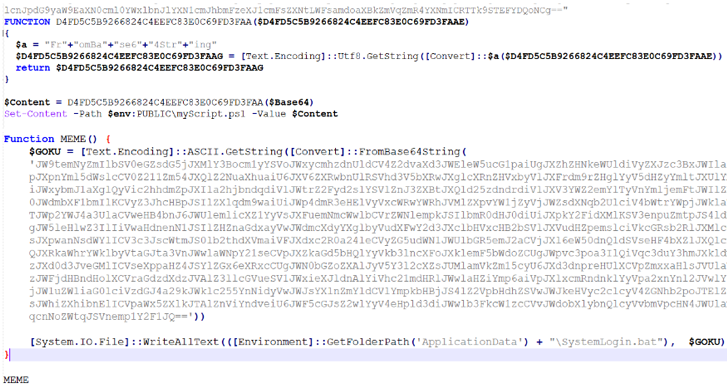
The VBScript code is then run to launch the batch file, which is subsequently deobfuscated to run the PowerShell script that was formerly sent alongside with it. In the closing phase, the PowerShell script is used to execute njRAT.
“njRAT, also recognized as Bladabindi is a distant obtain resource (RAT) with person interface or trojan which allows the holder of the software to management the end-user’s personal computer,” the cybersecurity company explained.
Observed this article exciting? Adhere to us on Twitter and LinkedIn to study more unique information we publish.
Some pieces of this article are sourced from:
thehackernews.com


 Google Chrome Hit by Second Zero-Day Attack – Urgent Patch Update Released
Google Chrome Hit by Second Zero-Day Attack – Urgent Patch Update Released