A fiscally motivated danger actor tracked as Blind Eagle has resurfaced with a refined toolset and an elaborate an infection chain as section of its attacks targeting corporations in Colombia and Ecuador.
Test Point’s most up-to-date investigation presents new insights into the Spanish-speaking group’s ways and techniques, which includes the use of innovative applications and federal government-themed lures to activate the killchain.
Also tracked under the title APT-C-36, Blind Eagle is notable for its slender geographical target and launching indiscriminate attacks against South American nations because at the very least 2018.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Blind Eagle’s operations have been documented by Craze Micro in September 2021, uncovering a spear-phishing marketing campaign largely aimed at Colombian entities intended to produce a commodity malware recognized as BitRAT, with a lesser emphasis to targets in Ecuador, Spain, and Panama.
Attacks chains start with phishing e-mail containing a booby-trapped url that, when clicked, potential customers to the deployment of an open resource trojan named Quasar RAT with the top target of gaining access to the victim’s bank accounts.
Some of targeted banking institutions consists of Banco AV Villas, Banco Caja Social, Banco de Bogotá, Banco Well-liked, Bancoomeva, BBVA, Colpatria, Davivienda, and TransUnion.
Need to the email receiver be located outdoors of Colombia, the attack sequence is aborted and the victim is redirected to the official website of the Colombian border regulate company, Migración Colombia.
A related campaign singling out both equally Colombia and Ecuador masquerades as the latter’s Inner Revenue Company (SRI) and makes use of a related geo-blocking technology to filter out requests originating from other nations around the world.
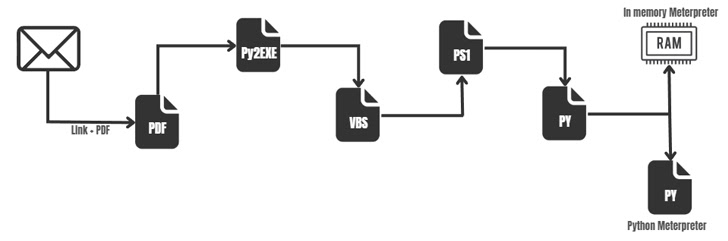
This attack, somewhat than dropping a RAT malware, employs a extra complicated multi-phase method that abuses the legitimate mshta.exe binary to execute VBScript embedded inside an HTML file to finally obtain two Python scripts.
The first of the two, ByAV2.py, is an in-memory loader engineered to run a Meterpreter payload in DLL format. mp.py is also a Meterpreter artifact, only it can be programmed in Python, indicating that the risk actor could be applying one particular of them as a redundant strategy to keep backdoor access to the host.
“Blind Eagle is a strange hen among APT groups,” the scientists concluded. “Judging by its toolset and typical functions, it is clearly additional interested in cybercrime and monetary get than in espionage.”
The advancement arrives times following Qualys disclosed that an unfamiliar adversary is leveraging particular info stolen from a Colombian cooperative lender to craft phishing e-mail that end result in the deployment of BitRAT.
Identified this short article exciting? Follow us on Twitter and LinkedIn to browse far more distinctive information we post.
Some areas of this posting are sourced from:
thehackernews.com


 Rapid7 hires whistleblower Peiter “Mudge” Zatko a year after Twitter sacking
Rapid7 hires whistleblower Peiter “Mudge” Zatko a year after Twitter sacking