Web Application Security is composed of a myriad of security controls that make sure that a web application:
Web Applications have grow to be ubiquitous just after the growth of Web 2., which Social Media Platforms, E-Commerce web sites, and email purchasers saturating the internet areas in new several years.
As the applications take in and retailer even much more delicate and comprehensive data, they grow to be an at any time more interesting focus on for attackers.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Typical Attack Techniques
The three most frequent vulnerabilities that exist in this house are Injections (SQL, Remote Code), Cryptographic Failures (previously delicate data exposure), and Broken Entry Command (BAC). Today, we will aim on Injections and Broken Obtain Control.
Injections
SQL is the most widespread Database software that is employed, and hosts a plethora of payment knowledge, PII information, and interior organization information.
A SQL Injection is an attack that utilizes destructive SQL code for backend database manipulation to accessibility information and facts that was not intended to be shown.
The starting off issue for this, is a command this sort of as the a person below:

This will return ALL rows from the “Users” table, due to the fact OR 1=1 is usually Correct. Going further with this, this process will also return passwords if there are any.
Photograph an attack like this getting executed from a huge social media corporation, or a significant e-commerce organization, and one can begin to see how a great deal delicate information can be retrieved with just one particular command.
Damaged Obtain Manage
Damaged Accessibility Management (BAC) has risen the ranks on the OWASP best 10 from fifth to the most common Web Application Security Hazards. The 34 Typical Weak spot Enumerations (CWEs) mapped to Broken Obtain Handle had extra occurrences in purposes than any other class in the course of OWASP’s new testing.
The most widespread types of BAC, is Vertical and Horizontal privilege escalation. Vertical privilege escalation occurs when a person can elevate their privileges and conduct steps, they ought to not have accessibility to do.
The CVE-2019-0211, which was an Apache Nearby Privilege Escalation. This critical vulnerability, from 2019, affected Apache HTTP servers managing on Unix devices, specifically these employing the mod_prefork, mod_employee, and mod_occasion libraries.
This granted attackers the capacity to execute unprivileged scripts, possibly main to root accessibility and compromising shared hosting providers. Exploiting this flaw involves the manipulation of shared-memory regions within just Apache’s employee procedures, which will have to be performed ahead of initiating an Apache sleek restart.
The underneath is a screenshot of the POC code. As a person can see, a selected stage of complex skill is essential in this respect, nonetheless, vertical privilege escalation can just as simply come about when a user’s permissions are extremely permissive, or not revoked when they depart a enterprise.
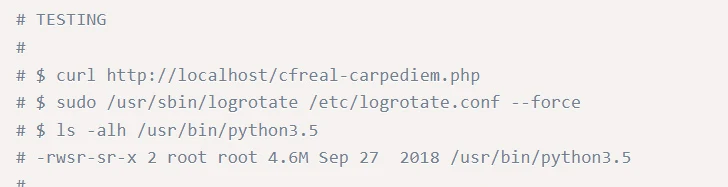
This normally takes us back to the principle of minimum privilege, a ubiquitous expression located all over the IT earth, that is now turning out to be much more commonplace as we realise how important web purposes have turn out to be.
Horizontal Privilege Escalation is when a user gains access to data they are not intended to have access to, but that info is held at the exact same level as their personal permissions. This can be witnessed with a single normal person accessing the info of yet another normal person. While this really should not be authorized, the privileges are not climbing vertical, but spreading horizontally. This is at times observed as extra dangerous, as it can happen without the need of elevating any alerts on security units.
With BAC getting to be ever a lot more present in the past few of decades, it is crucial to remember:
- Only depending on obfuscation is not a sufficient system for accessibility management.
- If a source is not meant to be accessible to the community, it ought to be denied accessibility by default.
- Builders need to explicitly specify allowed access for each and every useful resource at the code stage, with entry denial as the default location.
Best Procedures – Go through amongst the Traces (of code!)
To sustain security, developers want to verify incoming info, carry out parameterized queries when interacting with databases, and apply helpful session administration solutions to guard sensitive information. Significantly of this relies on both of those the security of web browsers, but also of the back-finish security of the web servers offering web content material, primary to a segregation of obligations in web security.
The most important difficulty that occurs right here, is that although Web Software Firewalls (WAFs), can mitigate these dangers, considerably of the duty for secure implementation of web content lands at the feet of the builders who set these web-sites collectively. Cybersecurity can generally develop into an afterthought, with performance being favored.
Simple Instance – Input Validation
Enter Validation is the simplest and most powerful approaches to put into action safe coding, in this instance to stop SQL injections.


In this code, the (user_enter,) is a tuple made up of the user’s enter. The databases driver requires care of escaping and thoroughly handling this enter. It makes sure that the input is dealt with as a knowledge worth, not executable SQL code.
If the user input incorporates destructive code, this sort of as “105 or 1=1,” it is not executed as SQL. Instead, it is treated as a worth to be in contrast to the UserId in the databases.
The databases driver automatically handles the escaping of the input, stopping it from affecting the framework of the SQL query or introducing security vulnerabilities.
Web Application Firewalls (WAFs)
A WAF operates at layer 7 of the OSI model, and functions as a reverse proxy, making certain customer traffic passes through the WAF prior to entering the backend server. The regulations or policies on the WAF secure in opposition to the documented vulnerabilities that are present in these backend servers and filter out destructive site visitors.
There are a plethora of WAFs on the market, and these can all offer a potent defence versus the a lot more novel attacks, and contribute very well to a defence in depth solution, the follow of secure coding is a thing that make sure the foundations of the web software is secure and will not slide victim to additional advanced or novel attacks in the upcoming.
WAFs are at present moving towards a combination of security product that use behavioural-examination systems to detect destructive threats, and more mitigate in opposition to the threats of far more advanced ‘bots’ which have been leveraged for reduced-energy attacks on internet sites.
The main disadvantage of working with a WAF, aside from the included latency and HTTP overhead, is the reality that a WAF can be bypassed by utilizing a -working day exploit from a web software, which safe coding and right sanitisation can mitigate towards far more effectively that offsetting all Web software security to a WAF. It is vital to keep in mind a WAF is just a layer of security, and not the whole answer.
Incident Response and Recovery
SecurityHQ’s suggestions to mitigate versus attacks:
- This really should be coupled with ensuring the basic principle of least privilege.
For additional details on these threats, speak to an skilled in this article. Or if you suspect a security incident, you can report an incident below.
Notice: This short article was expertly written by Tim Chambers, Senior Cyber Security Manager at SecurityHQ
Discovered this post interesting? Stick to us on Twitter and LinkedIn to browse more unique content we publish.
Some sections of this short article are sourced from:
thehackernews.com


 New Security Vulnerabilities Uncovered in pfSense Firewall Software – Patch Now
New Security Vulnerabilities Uncovered in pfSense Firewall Software – Patch Now