The Chinese cyber espionage actor identified as Camaro Dragon has been noticed leveraging a new strain of self-propagating malware that spreads through compromised USB drives.
“Though their principal target has ordinarily been Southeast Asian nations, this hottest discovery reveals their world-wide reach and highlights the alarming function USB drives enjoy in spreading malware,” Test Stage reported in new analysis shared with The Hacker News.
The cybersecurity company, which observed proof of USB malware infections in Myanmar, South Korea, Terrific Britain, India, and Russia, claimed the results are the final result of a cyber incident that it investigated at an unnamed European clinic in early 2023.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
The probe located that the entity was not directly qualified by the adversary but instead suffered a breach by using an employee’s USB travel, which became contaminated when it was plugged into a colleague’s laptop at a conference in Asia.
“As a result, on returning to the healthcare institution in Europe, the staff inadvertently released the contaminated USB drive, which led to unfold of the infection to the hospital’s computer system units,” the organization said.

Camaro Dragon shares tactical similarities with that of exercise clusters tracked as Mustang Panda and LuminousMoth, with the adversarial crew just lately joined to a Go-dependent backdoor identified as TinyNote and a destructive router firmware implant named HorseShell.
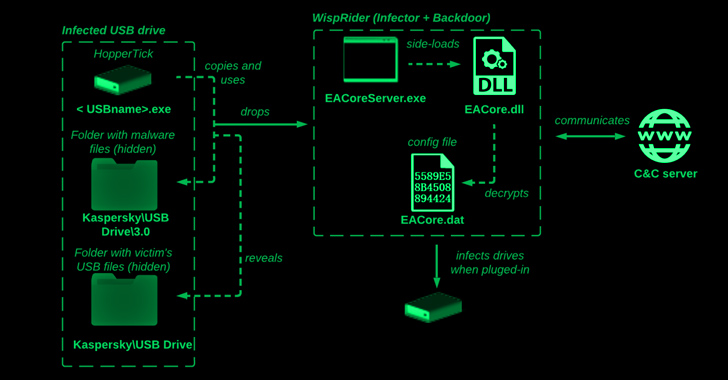
The hottest infection chain contains a Delphi launcher recognised as HopperTick which is propagated by way of USB drives and its major payload dubbed WispRider, which is dependable for infecting the devices when they are attached to a machine.
“When a benign USB thumb push is inserted into an contaminated laptop, the malware detects a new system inserted into the Pc and manipulates its information, generating various concealed folders at the root of the thumb generate,” Test Place scientists said.
WispRider, moreover infecting the current host if not currently, is tasked with communicating with a remote server, compromising any freshly connected USB gadgets, executing arbitrary instructions, and doing file operations.
Pick out variants of WispRider also functionality as a backdoor with capabilities to bypass an Indonesian antivirus alternative termed Smadav as properly as vacation resort to DLL side-loading by working with factors from security software package like G-Knowledge Full Security.
Another submit-exploitation payload delivered alongside WispRider is a stealer module referred to as disk monitor (HPCustPartUI.dll) that phases files with predefined extensions (i.e., docx, mp3, wav, m4a, wma, aac, cda, and mid) for exfiltration.
Upcoming WEBINAR🔐 Mastering API Security: Knowledge Your Genuine Attack Surface
Discover the untapped vulnerabilities in your API ecosystem and get proactive techniques toward ironclad security. Be a part of our insightful webinar!
Sign up for the Session.wn-button,.wn-label,.wn-label:soon afterexhibit:inline-block.examine_two_webinarmargin:20px 10px 30px 0background:#f9fbffcolor:#160755padding: 5%border:2px good #d9deffborder-radius:10pxtext-align:leftbox-shadow:10px 10px #e2ebff-webkit-border-major-left-radius:25px-moz-border-radius-topleft:25px-webkit-border-base-appropriate-radius:25px-moz-border-radius-bottomright:25px.wn-labelfont-sizing:13pxmargin:20px 0font-body weight:600letter-spacing:.6pxcolor:#596cec.wn-label:immediately afterwidth:50pxheight:6pxcontent:”border-major:2px reliable #d9deffmargin: 8px.wn-titlefont-sizing:21pxpadding:10px 0font-bodyweight:900text-align:leftline-peak:33px.wn-descriptiontext-align:leftfont-dimensions:15.6pxline-top:26pxmargin:5px !importantcolor:#4e6a8d.wn-buttonpadding:6px 12pxborder-radius:5pxbackground-colour:#4469f5font-measurement:15pxcolor:#fff!importantborder:0line-height:inherittext-decoration:none!importantcursor:pointermargin:15px 20pxfloat:leftfont-excess weight:500letter-spacing:.2px
This is not the initially time Chinese threat actors have been observed using edge of USB units as an infection vector to get to environments considerably outside of the scope of the threat actor’s principal interests.
In November 2022, Google-owned Mandiant attributed UNC4191, a menace actor with a suspected China nexus, to a set of espionage attacks in the Philippines that lead to the distribution of malware these kinds of as MISTCLOAK, DARKDEW, and BLUEHAZE.
A subsequent report from Trend Micro in March 2023 discovered overlaps between UNC4191 and Mustang Panda, connecting the latter to the use of MISTCLOAK and BLUEHAZE in spear-phishing campaigns focusing on nations in Southeast Asia.
The growth is a signal that the risk actors are actively transforming their resources, practices, and methods (TTPs) to bypass security alternatives, when concurrently relying on a wide collection of custom instruments to exfiltrate delicate details from target networks.
“The Camaro Dragon APT team carries on to employ USB gadgets as a system for infecting targeted programs, proficiently combining this system with other founded techniques,” the scientists said.
Identified this report interesting? Follow us on Twitter and LinkedIn to read more unique articles we write-up.
Some elements of this post are sourced from:
thehackernews.com

 Unveiling the Unseen: Identifying Data Exfiltration with Machine Learning
Unveiling the Unseen: Identifying Data Exfiltration with Machine Learning