Currently, we can’t help noticing an unlimited cycle in which the additional enterprises invest in risk avoidance the additional hackers adapt and go on to penetrate enterprises.
To make issues worse, detecting these penetrations nevertheless will take way too extensive with an ordinary dwell time that exceeds 100 (!) times.
To continue to keep the enterprise shielded, IT needs to determine out a way to crack this infinite cycle with out purchasing advanced security and facts analysis equipment and employing the ideal (proficient and high priced) safety professionals to operate them.
Enter MDR
An sophisticated protection support, Managed Detection and Response (MDR), gives ongoing risk detection and response, leveraging AI and device discovering to examine, notify, and consist of threats.
MDR is getting to be preferred and attaining traction. In actuality, Gartner forecasts that by 2024, 25% of companies will be applying MDR providers, up from much less than 5% currently. And by 2024, 40% of midsize enterprises will use MDR as their only managed protection company (source: Gartner’s Industry Tutorial for Managed Detection and Response Services Printed 15 July 2019 – ID G00367208).
MDR is the industry’s hope to crack the cycle of adding additional and a lot more danger prevention equipment, as hackers continuously raise their assault capabilities. Nonetheless, to get visibility into all community site visitors – vital for powerful detection and reaction – common MDR products and services demand installing committed software package and hardware across an enterprise’s network.
This deployment design is pricey and complicated, causing quite a few corporations to set off implementing MDR expert services though leaving their community at chance.
Houston, we have a triple problem
1 — Every enterprise is a concentrate on for hackers, no matter of its measurement or variety of business. In accordance to Verizon’s 2019 Data Breach Investigations Report (DBIR), 43% of breaches included modest company victims 10% have been breaches of the Monetary Industry, and 15% ended up breaches involving Health care organizations. 2 — On prime of that, enterprises will need generally to presume the worst, as Gartner states obviously, “The assumption must be that the business will be compromised, that the hacker’s skill to penetrate devices is never totally countered. Ongoing checking of programs and actions is the only way to reliably detect threats right before it is much too late.”3 — As a final result, enterprises must constantly stand guard, presenting a enormous obstacle for IT in terms of assets and in-dwelling expertise. Also, in accordance to the DBIR, “56% of breaches took months or for a longer time to find,” which all through this very long dwell time the malware distributes alone, spreads in the course of the organization, and when activated, the destruction brought on is multiplied.
In small, if all enterprises are targets, and must always assume they are less than attack, then IT needs to be observing 24/7. Hmmm, does this sound impractical to anybody else?

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Alright, we’ve experienced a trouble – fulfill Cato MDR
Cato MDR is integrated into Cato’s SASE system, beating the complications of common MDR. Cato aims to split the limitless cycle of escalating threats and lurking hackers. How? By enabling buyers that use Cato Cloud, to offload the source-intensive and ability-dependent system of detecting compromised endpoints, to its SOC team. The crew has prompt, crystal clear visibility to all website traffic, and you can find no will need for customers to deploy any extra network probes or software agents.
Cato mechanically collects, indexes, and shops the metadata of just about every WAN and World wide web targeted visitors flow traversing the Cato Cloud. Information aggregation and device understanding algorithms mine the whole network context of Cato’s huge info warehouse, detecting any malware indicators across buyer networks. Cato’s SOC crew assesses the site visitors flaws and alerts clients on any lively threats.
A sneak peek behind the scenes
Cato statements that its MDR company stands guard for shoppers, and dwell time is lowered from months to just 1-2 days. We had to get a nearer appear to have an understanding of, if and how this is feasible. Here is what we discovered.
Cato’s MDR services provides these vital abilities:
- Zero-footprint facts selection: Cato can access all suitable information and facts for menace investigation since it currently serves as the customer’s community system (remember, Cato MDR is built-in into Cato’s SASE platform). This eradicates the need to have for any additional installations, and all that’s still left for prospects is to subscribe to the provider.
- Automatic menace hunting: Cato utilizes large info and machine mastering algorithms to mine the community for suspicious flows, which are based mostly on the quite a few circulation characteristics obtainable to Cato. These include precise consumer software identification, geolocation, risk assessment of the location based on IP, URL class, URL title structure, frequency of entry, and a lot more.
- Human verification: Cato’s SOC group inspects suspicious flows on a every day foundation, closing the investigation for benign site visitors.
- Network-stage danger containment: Cato alerts shoppers in case of a verified threat, and dependent on a predefined plan, will implement community-amount threat containment by blocking the network targeted visitors.
- Guided remediation: Cato gives the context of threats for It’s even further reference and suggests the steps to be taken for remediation.
Additional awesome abilities
Multi-dimensional technique:
Cato has entire visibility into all network traffic. From every single community move that passes by its MDR service, Cato extracts and collects metadata on the pursuing:
- Supply – Cato distinguishes among human and non-human site visitors, shopper sort, OS details,
- and extra.
- Destination – Cato sees the recognition, class, and name.
- Behavior – Cato understands the website traffic designs, these kinds of as frequency and quantity of knowledge.
Cato then suppliers all this metadata in its huge information repository. 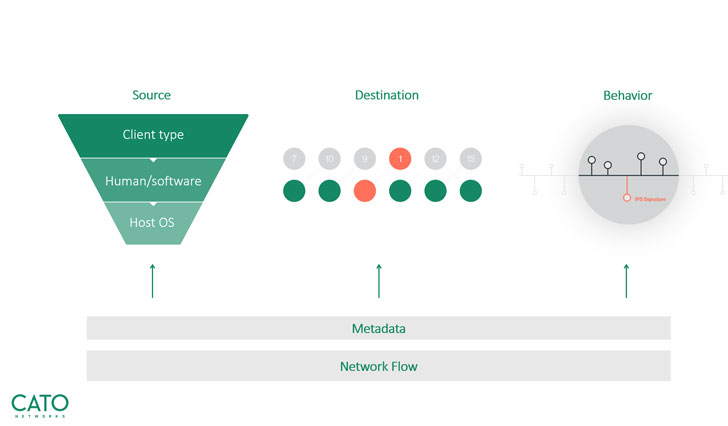 Cato’s exclusive multi-dimensional strategy
Cato’s exclusive multi-dimensional strategy
Risk looking:
We zoomed into Cato’s threat hunting technological innovation and learned that Cato lowers a each day amount of hundreds of thousands of flows down to only 10-20 flows, which will need really to be investigated by its SOC workforce. The group then assessments the list and helps make certain clients are only notified of confirmed threats that have to have focus. This removes what we all dread – wrong positives. 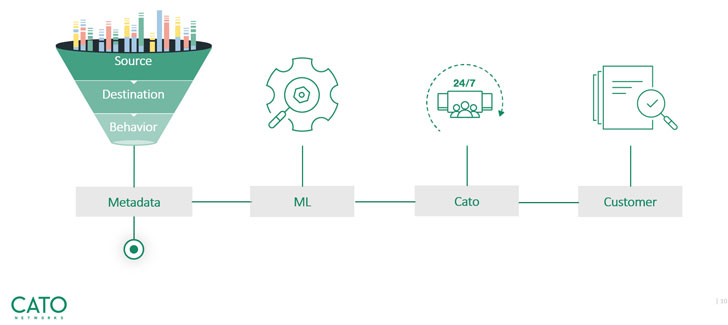 Threat searching – from thousands and thousands of activities to a significant, actionable item
Threat searching – from thousands and thousands of activities to a significant, actionable item
Company walkthrough
The Cato MDR portal is the place buyers take care of all requests and actions. The portal features an on the web ticketing program, via which all threats are reported, and their remediation position is tracked. We found the portal to be intuitive and self-explanatory we’re delighted to consider you via a rapid walkthrough:
The moment you log into the portal, you can expect to be in a position to see your company’s activities’ thorough status. 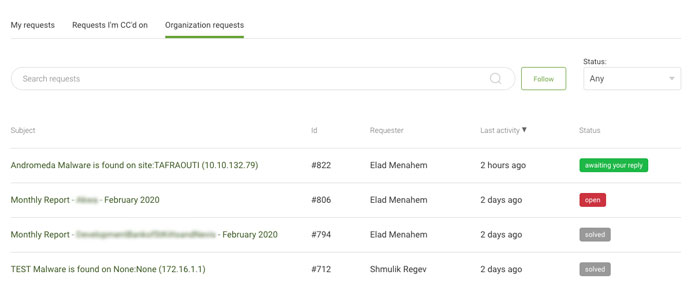 View all firm functions and requests
View all firm functions and requests
For just about every ask for group, you can see a summary of all lively tickets that consist of: the ID range of a unique request, the name of the requestor, the time of the last exercise done on the request, and the position of the ticket.
Clicking on any of the requests enabled us to drill down into its specifics. Each threat incident includes the pursuing detailed details:
- Name and IP of the web-site on which a menace was uncovered.
- Sort and identify of danger.
- Possibility degree of a certain danger variety.
- Inside/exterior IP handle that is the focus on of an attack.
- Domain identify that refers to a server’s IP deal with.
- Place port number of a conversation channel.
- Reference and hyperlink to Cato’s occasion discovery (Instantaneous Perception).
- Action taken by Cato’s SOC workforce.
- Further more reference to a unique menace or assault.
- Encouraged motion for prospects to consider for getting rid of a menace.
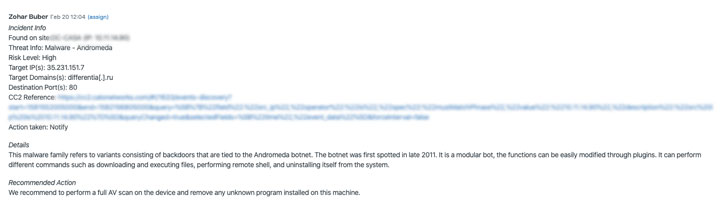 Drill down into any ask for
Drill down into any ask for
Cato MDR generates every month studies that listing all preceding and ongoing investigations and consist of an executive summary part, which we found specifically effective for quickly sharing with applicable friends and supervisors.
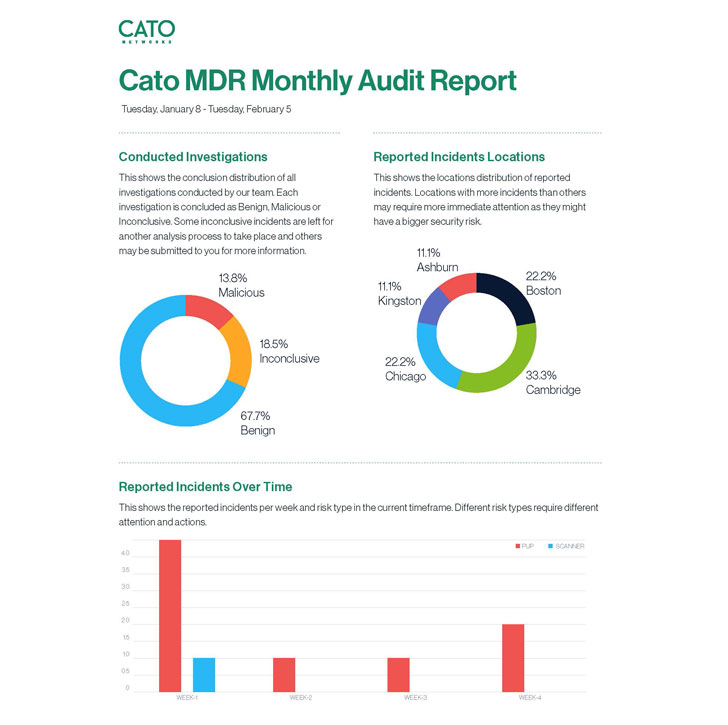
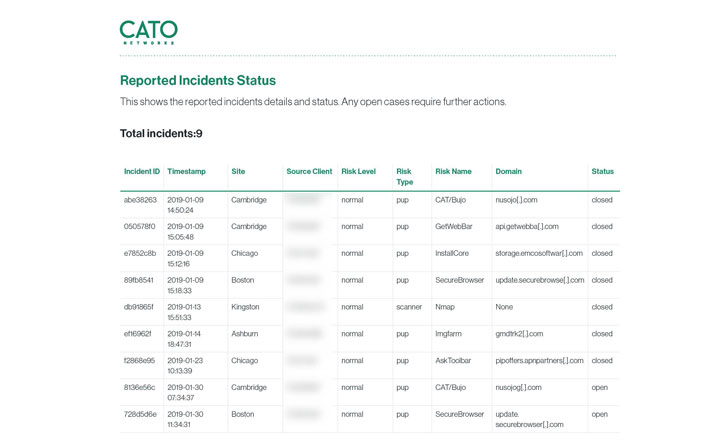
Regular monthly audit reports of all functions
Wrap-up
Cato MDR gained us (and Cato shoppers) more than with its subtle capabilities on the 1 hand, and effortless-to-use portal on the other. But typically we ended up amazed by the peace and tranquil it presents enterprises and their IT teams. Cato supports Gartner’s 4 levels of an adaptive security architecture.
Cato’s built-in safety stack addresses the Prediction and Prevention stages, and Cato MDR concludes with the remaining stages of Detection and Response.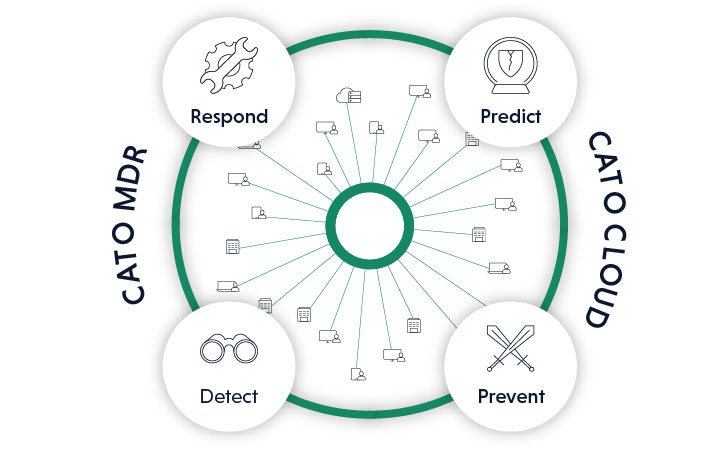 Cato MDR provides Detection and Response to Prediction and Prevention now sent by Cato Cloud
Cato MDR provides Detection and Response to Prediction and Prevention now sent by Cato Cloud
Significant LIKE Cato Networks!
Identified this report intriguing? Adhere to THN on Facebook, Twitter and LinkedIn to examine additional unique information we publish.

 Critical RCE Flaw (CVSS 10) Influences F5 Massive-IP Application Security Servers
Critical RCE Flaw (CVSS 10) Influences F5 Massive-IP Application Security Servers