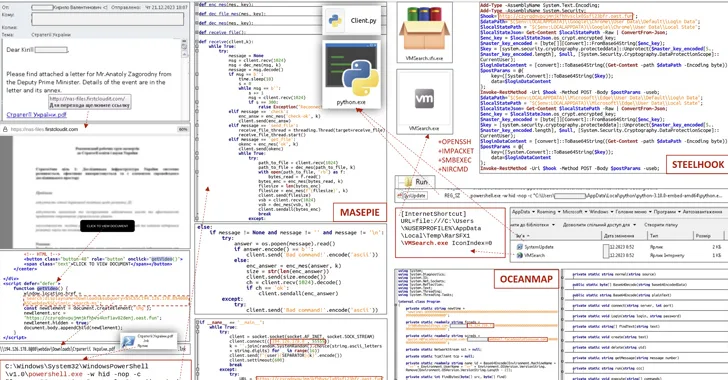
The Laptop or computer Emergency Reaction Crew of Ukraine (CERT-UA) has warned of a new phishing marketing campaign orchestrated by the Russia-joined APT28 group to deploy beforehand undocumented malware these types of as OCEANMAP, MASEPIE, and STEELHOOK to harvest delicate information.
The activity, which was detected by the agency involving December 15 and 25, 2023, targets authorities entities with email messages urging recipients to click on on a backlink to perspective a doc.
Future WEBINAR From Person to ADMIN: Master How Hackers Acquire Full Control

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Explore the top secret tactics hackers use to develop into admins, how to detect and block it ahead of it truly is too late. Sign up for our webinar right now.
Be part of Now
Even so, to the opposite, the links redirect to malicious web assets that abuse JavaScript and the “search-ms:” URI protocol handler to drop a Windows shortcut file (LNK) that launches PowerShell instructions to activate an an infection chain for a new malware regarded as MASEPIE.
MASEPIE is a Python-dependent instrument to down load/add documents and execute commands, with communications with the command-and-command (C2) server having place over an encrypted channel making use of the TCP protocol.
The attacks more pave the way for the deployment of further malware, including a PowerShell script referred to as STEELHOOK that’s able of harvesting web browser information and exporting it to an actor-managed server in Foundation64-encoded format.
Also shipped is a C#-centered backdoor dubbed OCEANMAP that is intended to execute instructions making use of cmd.exe.
“The IMAP protocol is made use of as a regulate channel,” CERT-UA explained, adding persistence is reached by generating a URL file named “VMSearch.url” in the Windows Startup folder.
“Instructions, in Foundation64-encoded kind, are contained in the ‘Drafts’ of the corresponding email directories each and every of the drafts includes the name of the laptop, the name of the user and the model of the OS. The benefits of the commands are saved in the inbox listing.”

The agency even further pointed out that reconnaissance and lateral movement routines are carried out inside of an hour of the original compromise by taking advantage of instruments like Impacket and SMBExec.
The disclosure comes months after IBM X-Drive disclosed APT28’s use of lures relevant to the ongoing Israel-Hamas war to facilitate the supply of a custom backdoor referred to as HeadLace.
In new weeks, the prolific Kremlin-backed hacking team has also been attributed to the exploitation of a now-patched critical security flaw in its Outlook email provider (CVE-2023-23397, CVSS score: 9.8) to achieve unauthorized access to victims’ accounts inside of Trade servers.
Uncovered this posting intriguing? Abide by us on Twitter and LinkedIn to browse far more exclusive material we write-up.
Some pieces of this posting are sourced from:
thehackernews.com

 Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks
Kimsuky Hackers Deploying AppleSeed, Meterpreter, and TinyNuke in Latest Attacks