Federal government and telecom entities have been subjected to a new wave of attacks by a China-joined threat actor tracked as Budworm employing an current malware toolset.
The intrusions, concentrating on a Center Eastern telecommunications group and an Asian govt, took spot in August 2023, with the adversary deploying an improved version of its SysUpdate toolkit, the Symantec Threat Hunter Staff, aspect of Broadcom, explained in a report shared with The Hacker News.
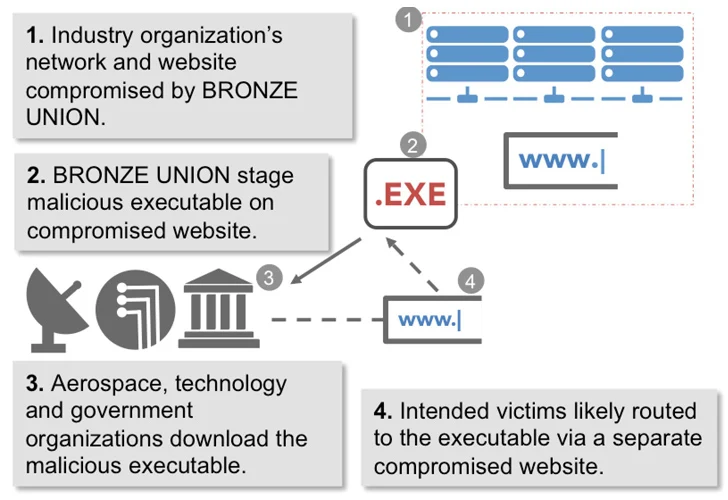
Budworm, also referred to by the names APT27, Bronze Union, Emissary Panda, Iron Tiger, Blessed Mouse, and Pink Phoenix, is identified to be active given that at minimum 2013, concentrating on a broad assortment of market verticals in pursuit of its intelligence gathering objectives.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The nation-point out team leverages many instruments this sort of as China Chopper web shell, Gh0st RAT, HyperBro, PlugX, SysUpdate, and ZXShell to exfiltrate significant-benefit information and facts and retain obtain to delicate devices around a prolonged time period of time.

A previous report from SecureWorks in 2017 exposed the attacker’s penchant for gathering defense, security, and political intelligence from organizations around the globe, characterizing it as a formidable threat.
It has also been noticed exploiting susceptible internet-going through products and services to attain entry to targeted networks. Earlier this March, Development Micro lose light-weight on the Linux variation of SysUpdate, which packs in capabilities to circumvent security program and resist reverse engineering.
The backdoor is attribute-loaded, earning it feasible to seize screenshots, terminate arbitrary procedures, perform file operations, retrieve travel facts, and execute commands.
“As perfectly as its custom made malware, Budworm also employed a variety of residing-off-the-land and publicly offered resources in these attacks,” Symantec mentioned. “It appears the action by the team could have been stopped early in the attack chain as the only destructive activity seen on contaminated devices is credential harvesting.”
Forthcoming WEBINARFight AI with AI — Battling Cyber Threats with Future-Gen AI Equipment
Prepared to tackle new AI-pushed cybersecurity difficulties? Sign up for our insightful webinar with Zscaler to tackle the increasing menace of generative AI in cybersecurity.
Supercharge Your Capabilities
With the latest progress, Budworm is the new addition to a increasing list of risk actors that have trained their eyes on the telecom sector in the Center East, together with formerly undocumented clusters dubbed ShroudedSnooper and Sandman.
“SysUpdate has been in use by Budworm considering that at minimum 2020, and the attackers surface to frequently produce the resource to improve its capabilities and stay away from detection.”
“That Budworm continues to use a recognised malware (SysUpdate), along with approaches it is regarded to favor, these as DLL aspect-loading utilizing an software it has utilized for this goal before, show that the group is just not much too anxious about acquiring this activity related with it if it is uncovered.”
Observed this write-up attention-grabbing? Follow us on Twitter and LinkedIn to go through much more exclusive written content we write-up.
Some areas of this write-up are sourced from:
thehackernews.com


 Update Chrome Now: Google Releases Patch for Actively Exploited Zero-Day Vulnerability
Update Chrome Now: Google Releases Patch for Actively Exploited Zero-Day Vulnerability