Cybersecurity scientists have uncovered an updated model of malware referred to as ValleyRAT that’s getting distributed as portion of a new marketing campaign.
“In the hottest edition, ValleyRAT released new instructions, this sort of as capturing screenshots, approach filtering, pressured shutdown, and clearing Windows occasion logs,” Zscaler ThreatLabz scientists Muhammed Irfan V A and Manisha Ramcharan Prajapati reported.
ValleyRAT was previously documented by QiAnXin and Proofpoint in 2023 in relationship with a phishing campaign targeting Chinese-talking users and Japanese companies that dispersed different malware households these as Purple Fox and a variant of the Gh0st RAT trojan identified as Sainbox RAT (aka FatalRAT).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

The malware has been assessed to be the get the job done of a China-centered danger actor, boasting of abilities to harvest delicate details and drop more payloads on to compromised hosts.
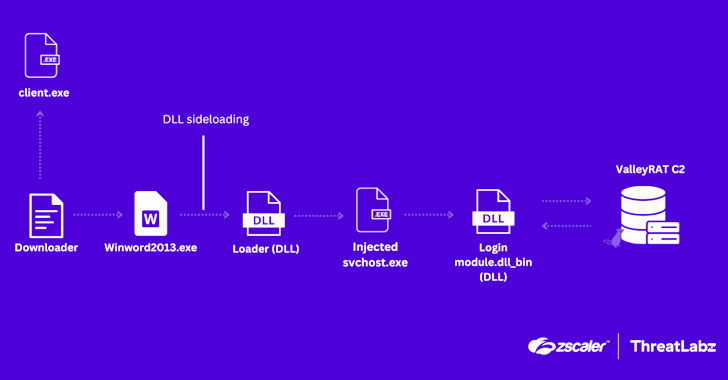
The starting off stage is a downloader that utilizes an HTTP File Server (HFS) to fetch a file named “NTUSER.DXM” which is decoded to extract a DLL file responsible for downloading “shopper.exe” from the same server.
The decrypted DLL is also created to detect and terminate anti-malware options from Qihoo 360 and WinRAR in an work to evade evaluation, right after which the downloader proceeds to retrieve three a lot more files – “WINWORD2013.EXE,” “wwlib.dll,” and “xig.ppt” – from the HFS server.
Future, the malware launches “WINWORD2013.EXE,” a legit executable involved with Microsoft Word, making use of it to sideload “wwlib.dll” that, in switch, establishes persistence on the process and loads “xig.ppt” into memory.
“From below, the decrypted ‘xig.ppt’ continues the execution approach as a system to decrypt and inject shellcode into svchost.exe,” the scientists claimed. “The malware creates svchost.exe as a suspended course of action, allocates memory within the system, and writes shellcode there.”
The shellcode, for its section, contains required configuration to get hold of a command-and-regulate (C2) server and obtain the ValleyRAT payload in the variety of a DLL file.
“ValleyRAT utilizes a convoluted multi-stage system to infect a procedure with the closing payload that performs the the greater part of the malicious functions,” the scientists reported. “This staged approach blended with DLL facet-loading are probable built to much better evade host-centered security options these as EDRs and anti-virus purposes.”

The enhancement will come as the Fortinet FortiGuard Labs uncovered a phishing campaign that targets Spanish-speaking folks with an current variation of a keylogger and data stealer named Agent Tesla.
The attack chain usually takes advantage of Microsoft Excel Add-Ins (XLA) file attachments that exploit acknowledged security flaws (CVE-2017-0199 and CVE-2017-11882) to result in the execution of JavaScript code that hundreds a PowerShell script, which is engineered to launch a loader in order to retrieve Agent Tesla from a distant server.
“This variant collects credentials and email contacts from the victim’s unit, the software from which it collects the info, and the standard information and facts of the victim’s system,” security researcher Xiaopeng Zhang stated. “Agent Tesla can also obtain the victim’s email contacts if they use Thunderbird as their email client.”
Found this posting fascinating? Follow us on Twitter and LinkedIn to go through a lot more distinctive articles we put up.
Some parts of this short article are sourced from:
thehackernews.com

 Snowflake Breach Exposes 165 Customers’ Data in Ongoing Extortion Campaign
Snowflake Breach Exposes 165 Customers’ Data in Ongoing Extortion Campaign