Researchers from China’s Pangu Lab have disclosed specifics of a “major-tier” backdoor place to use by the Equation Team, an highly developed persistent threat (APT) with alleged ties to the cyber-warfare intelligence-accumulating device of the U.S. Nationwide Security Company (NSA).
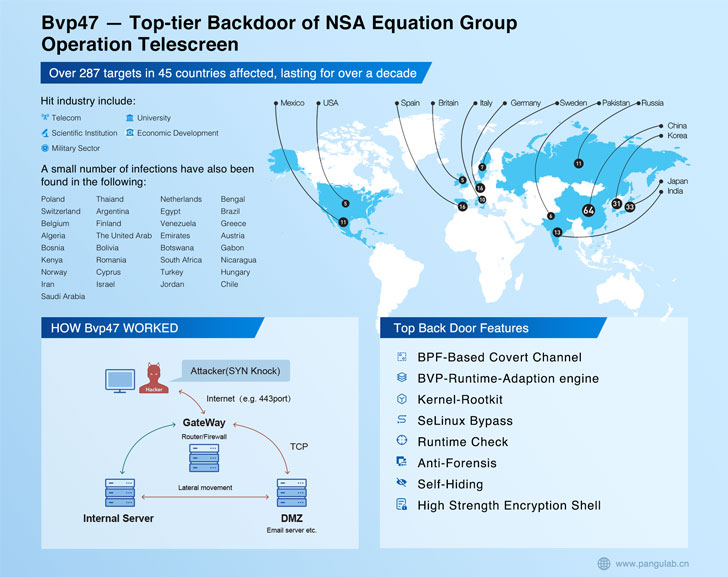
Dubbed “Bvp47” owing to several references to the string “Bvp” and the numerical value “0x47” utilized in the encryption algorithm, the backdoor was extracted from Linux techniques “in the course of an in-depth forensic investigation of a host in a important domestic office” in 2013.
Pangu Lab codenamed the attacks involving the deployment of Bvp47 “Procedure Telescreen,” with the implant showcasing an “state-of-the-art covert channel actions dependent on TCP SYN packets, code obfuscation, program hiding, and self-destruction design.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The Shadow Broker leaks
Equation Group, dubbed the “crown creator of cyber espionage” by Russian security agency Kaspersky, is the identify assigned to a sophisticated adversary that’s been energetic due to the fact at least 2001 applying formerly undisclosed zero-day exploits to “infect victims, retrieve data and conceal exercise in an outstandingly specialist way,” some of which ended up afterwards included into Stuxnet.

The attacks have specific a selection of sectors in no fewer than 42 nations around the world, including governments, telecom, aerospace, strength, nuclear investigation, oil and gasoline, armed forces, nanotechnology, Islamic activists and scholars, media, transportation, fiscal institutions, and firms acquiring encryption systems.
The group is considered to be linked to the NSA’s Personalized Obtain Functions (TAO) unit, though intrusion things to do pertaining to a second collective dubbed Longhorn (aka The Lamberts) have been attributed to the U.S. Central Intelligence Agency (CIA).
Equation Group’s malware toolset grew to become community expertise in 2016 when a group contacting by itself the Shadow Brokers leaked the total tranche of exploits used by the elite hacking workforce, with Kaspersky uncovering code-degree similarities in between the stolen data files and that of samples determined as employed by the risk actor.
Bvp47 as a covert backdoor
The incident analyzed by Pangu Lab comprises two internally compromised servers, an email and an business server named V1 and V2 respectively, and an external domain (dubbed A), sporting a novel two-way interaction mechanism to exfiltrate delicate data from the systems.
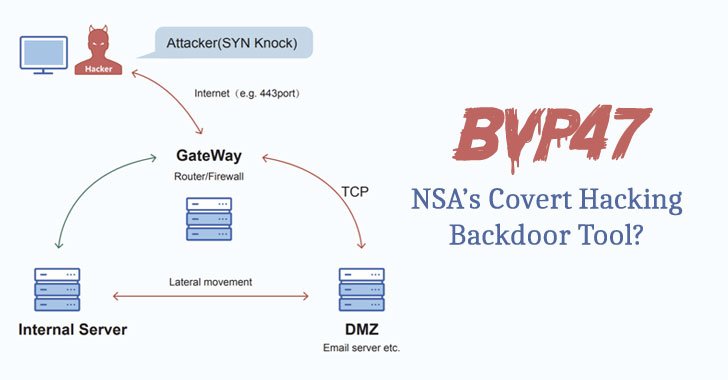
“There is abnormal interaction involving exterior host A and the V1 server,” the researchers claimed. “Specifically, A initial sends a SYN packet with a 264-byte payload to port 80 of the V1 server, and then the V1 server quickly initiates an external connection to the substantial-close port of the A machine and maintains a significant quantity of exchange details.”
Simultaneously, V1 connects to V2 by way of the SMB provider to complete a range of functions, which includes logging in to the latter with an administrator account, trying to open terminal solutions, enumerating directories, and executing PowerShell scripts as a result of scheduled jobs.
V2, for its part, also connects to V1 to retrieve a PowerShell script and an encrypted second-phase payload, the encrypted execution results of which are sent again to V1, which, in accordance to the scientists, “functions as a facts transfer between the A equipment and the V2 server.”
The Bvp47 backdoor installed on the servers is made up of two parts, a loader which is dependable for decoding and loading the real payload into memory. “Bvp47 frequently life in the Linux operating program in the demilitarized zone that communicates with the Internet,” the researchers said. “It mostly assumes the core regulate bridge communication position in the in general attack.”
Hyperlinks to the Equation Team
Pangu Lab’s attribution to Equation Group stems from overlaps with exploits contained in a GPG-encrypted archive file revealed by the Shadow Brokers – “eqgrp-auction-file.tar.xz.gpg” – as part of a failed auction of the cyber weapons in August 2016.
“In the process of analyzing the ‘eqgrp-auction-file.tar.xz.gpg’ file, it was found that Bvp47 and the attacking equipment in the compressed deal ended up technically deterministic, generally including ‘dewdrops,’ ‘suctionchar_brokers,’ ‘tipoffs,’ ‘StoicSurgeon,’ ‘incision’ and other directories,” the researchers defined.
“The ‘tipoffs’ directory includes the RSA uneven algorithm personal critical utilized in the Bvp47 covert channel [for] command execution and other functions. On this basis, it can be verified that Bvp47 is from [the] Equation team.”
The results mark the second time hitherto undocumented malware designed by the Equation Group has come to light-weight in as several months. In late December 2021, Examine Level Exploration disclosed facts of a diagnostic utility named “DoubleFeature” that is utilized in conjunction with the DanderSpritz malware framework.
“Judging from the attack applications associated to the corporation, which include Bvp47, Equation group is certainly a to start with-course hacking team,” the researchers concluded.
“The device is nicely-designed, effective, and greatly tailored. Its network attack ability outfitted by 0day vulnerabilities was unstoppable, and its information acquisition beneath covert control was with minimal exertion. The Equation Group is in a dominant posture in countrywide-stage cyberspace confrontation.”
Found this short article appealing? Stick to THN on Fb, Twitter and LinkedIn to browse a lot more exceptional articles we write-up.
Some components of this article are sourced from:
thehackernews.com



 9-Year-Old Unpatched Email Hacking Bug Uncovered in Horde Webmail Software
9-Year-Old Unpatched Email Hacking Bug Uncovered in Horde Webmail Software