An emerging menace actor out of China has been traced to a new hacking marketing campaign aimed at government businesses in India and citizens of Hong Kong intending to steal delicate data, cybersecurity business Malwarebytes uncovered in the most recent report shared with The Hacker Information.
The attacks have been noticed through the initially week of July, coinciding the passage of controversial security law in Hong Kong and India’s ban of 59 China-produced apps about privateness concerns, weeks right after a violent skirmish along the Indo-China border.
Attributing the attack with “average self confidence” to a new Chinese APT group, Malwarebytes said they were in a position to track their actions primarily based on the “exceptional phishing makes an attempt” created to compromise targets in India and Hong Kong.
The operators of the APT group have leveraged at the very least 3 unique Ways, Approaches, and Methods (TTPs), applying spear-phishing e-mail to fall variants of Cobalt Strike and MgBot malware, and bogus Android applications to collect contact data, contacts, and SMS messages.
“The lures made use of in this campaign show that the threat actor may perhaps be focusing on the Indian governing administration and people in Hong Kong, or at minimum those people who are from the new security law issued by China,” the agency claimed.
Employing Spear-Phishing to Put in MgBot Malware
The initially variant, observed on July 2, alerted recipients with the “gov.in” domain stating some of their email addresses experienced been leaked and that they are to finish a security test right before July 5.
The emails arrive connected with a “Mail security test.docx” purportedly from the Indian Federal government Information Security Middle. On opening, it employs template injection to down load a distant template and execute a closely obfuscated variant of Cobalt Strike.
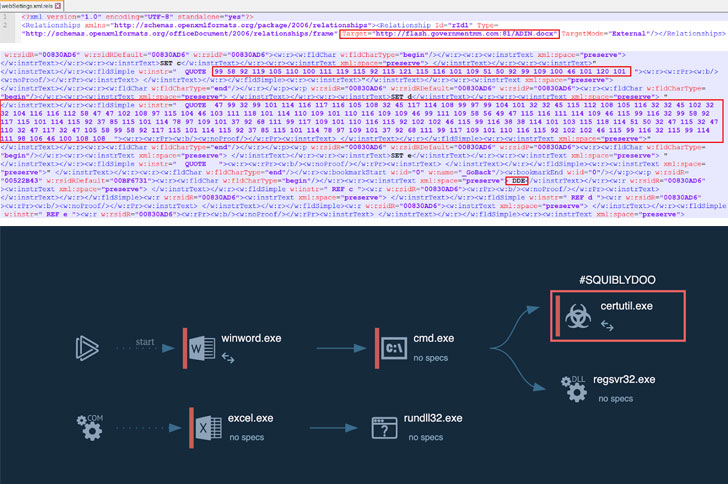
But a working day right after the aforementioned attack, the operators swapped out the malicious Cobalt Strike payload for an up-to-date variation of MgBot malware.
And in the 3rd model seen in the wild on July 5, the researchers noticed the APT applying an entirely distinctive embedded document with a assertion about Hong Kong from the Uk Primary Minister Boris Johnson allegedly promising to acknowledge three million Hong Kongers to the nation.
The malicious commands to down load and fall the loader — which are encoded within the documents — are executed employing the dynamic info exchange (DDE) protocol, an interprocess interaction method that allows information to be communicated or shared in between Windows purposes.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
A RAT With Quite a few Capabilities
The dropped loader (“ff.exe”) masquerades as a Realtek Audio Supervisor device and is made up of four embedded assets, two of which are written in Simplified Chinese.
This, along with the use of DDE and template injection, suggests the marketing campaign could be the handiwork of a China-dependent threat actor, given the prior background of assaults that took gain of the exact same TTPs.
Subsequently, the loader escalates its privileges as a result of a CMSTP bypass ahead of putting in the ultimate payload, even though also taking techniques to steer clear of detection by debuggers and security software package.
To thwart static assessment, “the code is self modifying which means it alters its code sections during runtime,” the scientists stated.
“It employs ‘GetTickCount’ and ‘QueryPerformanceCounter’ API phone calls to detect the debugger natural environment. To detect if it is jogging in a virtual environment, it utilizes anti-vm detection instructions this kind of as ‘sldt’ and ‘cpid’ that can present facts about the processor and also checks Vmware IO ports (VMXH).”
Finally, it can be this final malware executable (“pMsrvd.dll”) that is used to carry out the malicious routines, which it does by posing as a “Video clip Crew Desktop Application.”
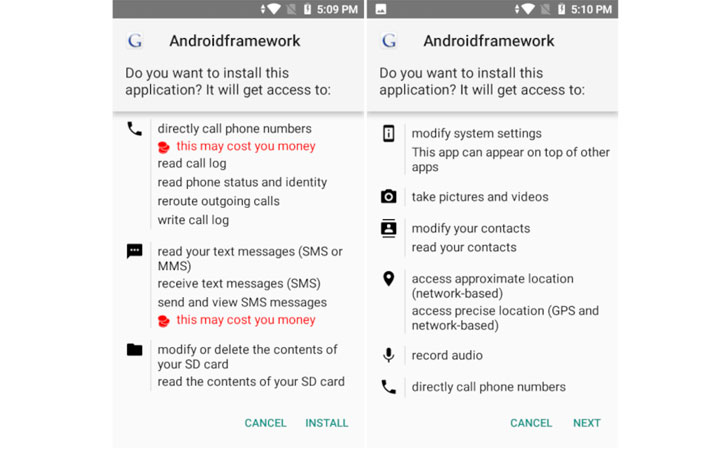
Not only is the bundled distant administration Trojan (RAT) able of developing a link to a remote command-and-manage (C2) server found in Hong Kong, it has the skill to seize keystrokes, screenshots, and control files and procedures.
What is extra, the scientists also observed quite a few destructive Android purposes as component of the group’s toolset that arrives outfitted with RAT attributes, these kinds of as audio and display recording and features to triangulate a phone’s site and exfiltrate contacts, get in touch with logs, SMS, and web record.
Curiously, it seems this new China APT team has been active at minimum since 2014, with its TTPs joined to at minimum three unique assaults in 2014, 2018, and March 2020. In all their campaigns, the actor utilised a variant of MgBot to satisfy its aims.
Discovered this posting appealing? Adhere to THN on Facebook, Twitter and LinkedIn to read through extra special articles we publish.


 Dependable Connectivity Alliance Announces New Chair and Expanded Board
Dependable Connectivity Alliance Announces New Chair and Expanded Board