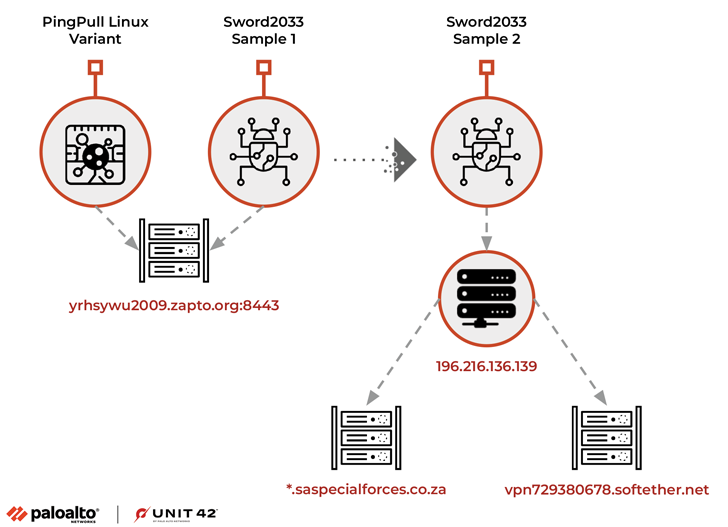
The Chinese country-state group dubbed Alloy Taurus is utilizing a Linux variant of a backdoor identified as PingPull as effectively as a new undocumented resource codenamed Sword2033.
That’s according to results from Palo Alto Networks Device 42, which found out the latest malicious cyber action carried out by the group focusing on South Africa and Nepal.
Alloy Taurus is the constellation-themed moniker assigned to a threat actor which is acknowledged for its attacks concentrating on telecom corporations since at the very least 2012. It’s also tracked by Microsoft as Granite Hurricane (beforehand Gallium).

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
Final thirty day period, the adversary was attributed to a marketing campaign known as Tainted Like targeting telecommunication providers in the Center East as section of a broader operation referred to as Comfortable Mobile.
Latest cyber espionage attacks mounted by Alloy Taurus have also broadened their victimology footprint to involve fiscal institutions and federal government entities.
PingPull, initial documented by Device 42 in June 2022, is a distant obtain trojan that employs the Internet Regulate Information Protocol (ICMP) for command-and-manage (C2) communications.
The Linux flavor of the malware features of related functionalities as its Windows counterpart, permitting it to have out file functions and run arbitrary commands by transmitting from the C2 server a single higher situation character in between A and K, and M.
“On execution, this sample is configured to communicate with the domain yrhsywu2009.zapto[.]org more than port 8443 for C2,” Unit 42 said. “It works by using a statically linked OpenSSL (OpenSSL .9.8e) library to interact with the domain about HTTPS.”
Apparently, PingPull’s parsing of the C2 instructions mirrors that of the China Chopper, a web shell broadly utilised by Chinese threat actors, suggesting that the danger actor is repurposing present resource code to devise customized resources.
A closer evaluation of the aforementioned area has also discovered the existence of another ELF artifact (i.e., Sword2033) that supports 3 essential capabilities, which include uploading and exfiltrating documents and executing commands.
Impending WEBINARZero Have confidence in + Deception: Find out How to Outsmart Attackers!
Learn how Deception can detect superior threats, prevent lateral movement, and enhance your Zero Rely on tactic. Be a part of our insightful webinar!
Help you save My Seat!
The malware’s inbound links to Alloy Taurus stems from the fact that the domain fixed to an IP deal with that was formerly discovered as an lively indicator of compromise (IoC) affiliated with a prior marketing campaign targeting corporations functioning in Southeast Asia, Europe, and Africa.
The focusing on of South Africa, for each the cybersecurity organization, comes towards the backdrop of the place keeping a joint 10-day naval drill with Russia and China earlier this calendar year.
“Alloy Taurus continues to be an energetic menace to telecommunications, finance and federal government businesses across Southeast Asia, Europe and Africa,” Unit 42 explained.
“The identification of a Linux variant of PingPull malware, as properly as new use of the Sword2033 backdoor, implies that the team proceeds to evolve their operations in assistance of their espionage routines.”
Discovered this article fascinating? Observe us on Twitter and LinkedIn to study extra unique content we post.
Some sections of this short article are sourced from:
thehackernews.com

 Charming Kitten’s New BellaCiao Malware Discovered in Multi-Country Attacks
Charming Kitten’s New BellaCiao Malware Discovered in Multi-Country Attacks