A “multi-12 months” Chinese point out-sponsored cyber espionage campaign has been noticed targeting South Korean academic, political, and government businesses.
Recorded Future’s Insikt Team, which is monitoring the exercise beneath the moniker TAG-74, claimed the adversary has been linked to “Chinese navy intelligence and poses a sizeable risk to educational, aerospace and protection, govt, military, and political entities in South Korea, Japan, and Russia.”
The cybersecurity firm characterized the focusing on of South Korean tutorial institutions as in alignment with China’s broader endeavours to perform mental property theft and extend its impact, not to point out enthusiastic by the country’s strategic relations with the U.S.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code

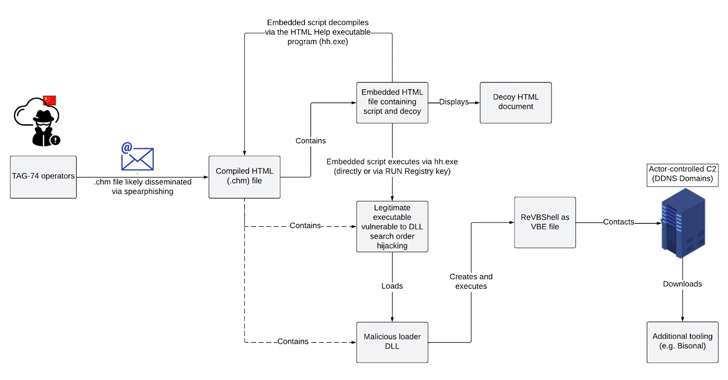
Social engineering attacks mounted by the adversary make use of Microsoft Compiled HTML Support (CHM) file lures to fall a customized variant of an open up-resource Visual Simple Script backdoor named ReVBShell, which subsequently serves to deploy the Bisonal distant accessibility trojan.
ReVBShell is configured to sleep for a specified interval through a command issued from a remote server that can edit the time period. It also takes advantage of Base64 encoding to mask the command-and-management (C2) website traffic.
The use of ReVBShell has been tied to two other China-nexus clusters recognized as Tick and Tonto Team, with the latter attributed to an identical an infection sequence by the AhnLab Security Unexpected emergency Reaction Middle (ASEC) in April 2023.
Bisonal is a multi-practical trojan that can harvest system and file information, execute instructions and information, terminate procedures, down load and upload information, and delete arbitrary files on disk.
Upcoming WEBINARFight AI with AI — Battling Cyber Threats with Up coming-Gen AI Resources
Prepared to deal with new AI-driven cybersecurity worries? Sign up for our insightful webinar with Zscaler to handle the growing danger of generative AI in cybersecurity.
Supercharge Your Abilities
TAG-74 is reported to be closely associated to Tick, once all over again highlighting the widespread device sharing amongst Chinese risk groups.
“The noticed TAG-74 campaign is indicative of the group’s prolonged-phrase intelligence collection aims against South Korean targets,” Recorded Upcoming said.
“Supplied the group’s persistent emphasis on South Korean organizations over lots of yrs and the likely operational purview of the Northern Theater Command, the group is most likely to carry on to be remarkably energetic in conducting extensive-phrase intelligence-gathering on strategic targets within just South Korea as well as in Japan and Russia.”
Observed this report intriguing? Follow us on Twitter and LinkedIn to examine more distinctive information we article.
Some elements of this posting are sourced from:
thehackernews.com

 Critical JetBrains TeamCity Flaw Could Expose Source Code and Build Pipelines to Attackers
Critical JetBrains TeamCity Flaw Could Expose Source Code and Build Pipelines to Attackers