Microsoft on Monday attributed a China-based mostly cyber espionage actor to a established of attacks focusing on diplomatic entities in South The usa.
The tech giant’s Security Intelligence crew is monitoring the cluster under the emerging moniker DEV-0147, describing the exercise as an “expansion of the group’s info exfiltration functions that ordinarily focused federal government companies and believe tanks in Asia and Europe.”
The menace actor is mentioned to use established hacking resources these types of as ShadowPad to infiltrate targets and retain persistent accessibility.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
ShadowPad, also identified as PoisonPlug, is a successor to the PlugX distant access trojan and has been extensively set to use by Chinese adversarial collectives with one-way links to the Ministry of Condition Security (MSS) and People’s Liberation Military (PLA), for every Secureworks.
A person of the other malicious payloads place to use by DEV-0147 is a webpack loader called QuasarLoader, which enables for deploying added payloads onto the compromised hosts.
Redmond did not disclose the method DEV-0147 may be applying to attain first entry to a goal surroundings. That reported, phishing and opportunistic focusing on of unpatched purposes are possible vectors.
“DEV-0147’s attacks in South The usa integrated put up-exploitation exercise involving the abuse of on-premises id infrastructure for recon and lateral motion, and the use of Cobalt Strike for command-and-handle and data exfiltration,” Microsoft claimed.
DEV-0147 is considerably from the only China-based innovative persistent danger (APT) to leverage ShadowPad in new months.
In September 2022, NCC Group unearthed details of an attack aimed at an unnamed group that leveraged a critical flaw in WSO2 (CVE-2022-29464, CVSS rating: 9.8) to drop web shells and activate an infection chain that led to the shipping and delivery of ShadowPad for intelligence gathering.
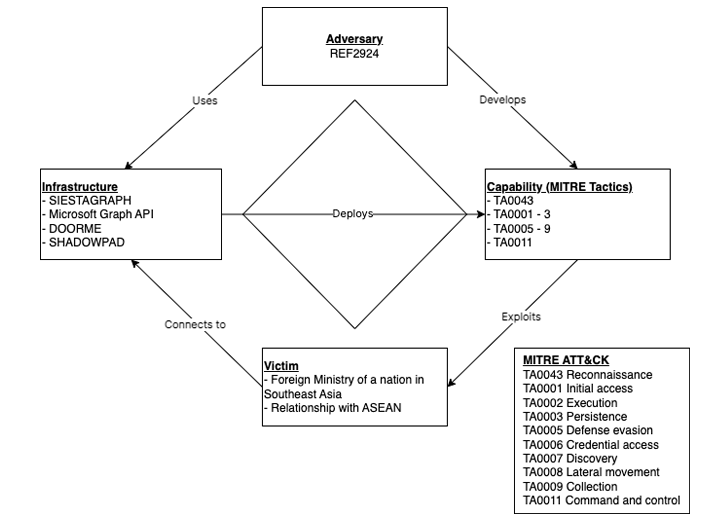
ShadowPad has also been employed by unidentified menace actors in an attack concentrating on an ASEAN member international ministry by the effective exploitation of a susceptible, and Internet-related, Microsoft Trade Server.
The action, dubbed REF2924 by Elastic Security Labs, has been noticed to share tactical associations with all those adopted by other country-state groups these kinds of as Winnti (aka APT41) and ChamelGang.
“The REF2924 intrusion set […] signifies an attack team that seems concentrated on priorities that, when observed across campaigns, align with a sponsored national strategic curiosity,” the corporation noted.
The simple fact that Chinese hacking teams continue on to use ShadowPad regardless of it being very well-documented above the several years implies the strategy is yielding some accomplishment.
Identified this write-up interesting? Adhere to us on Twitter and LinkedIn to go through much more distinctive material we submit.
Some parts of this article are sourced from:
thehackernews.com


 What is attack surface management?
What is attack surface management?