The China-linked country-condition hacking group referred to as Mustang Panda is making use of lures relevant to the ongoing Russo-Ukrainian War to attack entities in Europe and the Asia Pacific.
That is according to the BlackBerry Investigate and Intelligence Group, which analyzed a RAR archive file titled “Political Direction for the new EU solution to Russia.rar.” Some of the qualified countries contain Vietnam, India, Pakistan, Kenya, Turkey, Italy, and Brazil.
Mustang Panda is a prolific cyber-espionage team from China that’s also tracked under the names Bronze President, Earth Preta, HoneyMyte, RedDelta, and Red Lich.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

It really is believed to be active considering the fact that at minimum July 2018, for every Secureworks’ threat profile, even though indications are that the risk actor has been targeting entities all over the world as early as 2012.
Mustang Panda is acknowledged to seriously depend on sending weaponized attachments by using phishing emails to obtain original infection, with the intrusions finally primary to the deployment of the PlugX distant accessibility trojan.
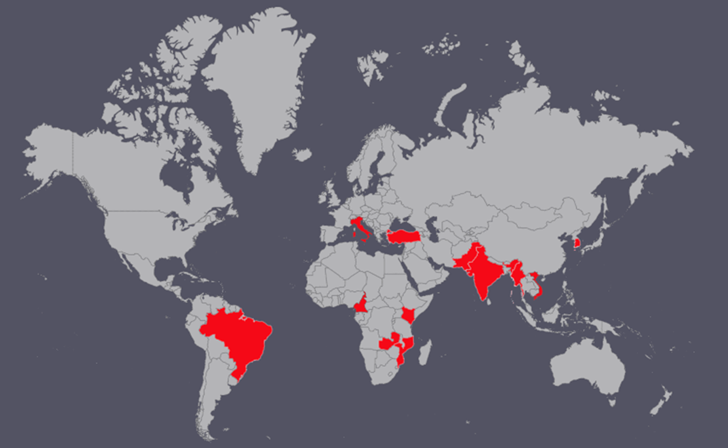
Nevertheless, latest spear-phishing attacks undertaken by the team focusing on governing administration, education and learning, and investigate sectors in the Asia Pacific location have included custom made malware like PUBLOAD, TONEINS, and TONESHELL, suggesting an expansion to its malware arsenal.
The latest findings from BlackBerry present that the core an infection system has remained more or less the exact same, even as Mustang Panda proceeds to make use of geopolitical gatherings to their benefit, echoing prior studies from Google and Proofpoint.
Contained inside the decoy archive is a shortcut to a Microsoft Phrase file, which leverages DLL side-loading – a system that was also utilized in attacks aimed at Myanmar earlier this calendar year – to kick off the execution of PlugX in memory, before exhibiting the document’s contents.
“Their attack chain stays reliable with the continued use of archive files, shortcut documents, destructive loaders, and the use of the PlugX malware, while their supply setup is typically custom-made per location/region to entice victims into executing their payloads in the hope of establishing persistence with the intent of espionage,” BlackBerry’s Dmitry Bestuzhev explained to The Hacker Information.
Found this posting appealing? Abide by us on Twitter and LinkedIn to go through far more exceptional information we article.
Some areas of this article are sourced from:
thehackernews.com


 UK Government Department Using Unsupported Applications, Reveals Watchdog
UK Government Department Using Unsupported Applications, Reveals Watchdog