Organizations in East Asia are becoming targeted by a most likely Chinese-speaking actor dubbed DragonSpark though utilizing uncommon ways to go earlier security layers.
“The attacks are characterized by the use of the little acknowledged open resource SparkRAT and malware that tries to evade detection by way of Golang source code interpretation,” SentinelOne reported in an evaluation released right now.
A hanging aspect of the intrusions is the reliable use of SparkRAT to conduct a wide range of pursuits, together with thieving information, acquiring manage of an contaminated host, or jogging extra PowerShell guidelines.

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The threat actor’s finish plans continue being unknown as however, despite the fact that espionage or cybercrime is possible to be the motive. DragonSpark’s ties to China stem from the use of the China Chopper web shell to deploy malware – a commonly utilised attack pathway amongst Chinese risk actors.
Furthermore, not only do the open up supply resources applied in the cyber assaults originate from builders or providers with hyperlinks to China, the instructure for staging the payloads are found in Taiwan, Hong Kong, China, and Singapore, some of which belong to respectable organizations.
The command-and-command (C2) servers, on the other hand, are situated in Hong Kong and the U.S., the cybersecurity organization reported.
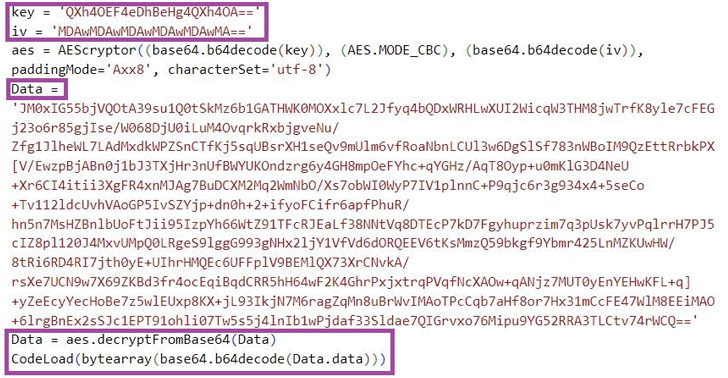
Original accessibility avenues entail compromising internet-uncovered web servers and MySQL database servers to fall the China Chopper web shell. The foothold is then leveraged to carry out lateral motion, privilege escalation, and malware deployment using open source equipment like SharpToken, BadPotato, and GotoHTTP.
Also sent to the hosts are personalized malware capable of executing arbitrary code and SparkRAT, a cross-platform remote access trojan that can operate program commands, manipulate documents and processes, and siphon information and facts of curiosity.
Yet another malware of be aware is the Golang-primarily based m6699.exe, which interprets at runtime the source code contained within it so as to fly under the radar and launch a shellcode loader that’s engineered to contact the C2 server for fetching and executing the up coming-phase shellcode.
“Chinese-speaking menace actors are recognized to often use open up source software in malicious strategies,” the scientists concluded.
“Because SparkRAT is a multi-system and feature-wealthy tool, and is consistently current with new features, we estimate that the RAT will continue being interesting to cybercriminals and other threat actors in the future.”
Discovered this post intriguing? Abide by us on Twitter and LinkedIn to examine far more unique content material we publish.
Some components of this short article are sourced from:
thehackernews.com


 FBI Says North Korean Hackers Behind $100 Million Horizon Bridge Crypto Theft
FBI Says North Korean Hackers Behind $100 Million Horizon Bridge Crypto Theft