A suspected Chinese-nexus hacking team exploited a not long ago disclosed zero-day flaw in Barracuda Networks Email Security Gateway (ESG) appliances to breach govt, army, defense and aerospace, substantial-tech business, and telecom sectors as element of a global espionage campaign.
Mandiant, which is tracking the exercise under the title UNC4841, explained the menace actor as “extremely responsive to defensive endeavours” and able of actively tweaking their modus operandi to retain persistent entry to targets.
“UNC4841 deployed new and novel malware intended to manage existence at a compact subset of high precedence targets that it compromised possibly before the patch was released, or soon adhering to Barracuda’s remediation guidance,” the Google-owned risk intelligence agency said in a new technological report revealed now.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount
Pretty much a third of the determined influenced organizations are governing administration organizations. Apparently plenty of, some of the earliest compromises appear to have taken location on a compact amount of products geolocated to mainland China.
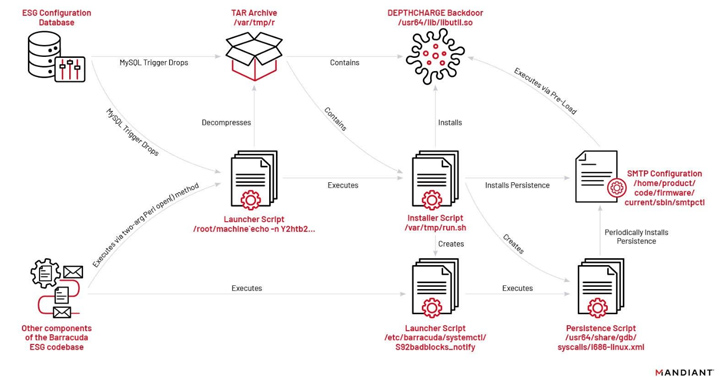
The attacks entail the exploitation of CVE-2023-2868 to deploy malware and perform publish-exploitation routines. In decide on circumstances, the intrusions have led to the deployment of supplemental malware, these kinds of as SUBMARINE (aka DEPTHCHARGE), to manage persistence in response to remediation endeavors.
Additional evaluation of the campaign has exposed a “distinct slide off in exercise from roughly January 20 to January 22, 2023,” coinciding with the beginning of the Chinese New Calendar year, adopted by two surges, a single following Barracuda’s public notification on May perhaps 23, 2023, and a next just one in early June 2023.

The latter is said to have concerned the attacker “attempting to retain accessibility to compromised environments via the deployment of the new malware people SKIPJACK, DEPTHCHARGE, and FOXTROT / FOXGLOVE.”
Although SKIPJACK is a passive implant that registers a listener for particular incoming email headers ahead of decoding and working their written content, DEPTHCHARGE is pre-loaded into the Barracuda SMTP (BSMTP) daemon applying the LD_PRELOAD natural environment variable, and retrieves encrypted instructions for execution.
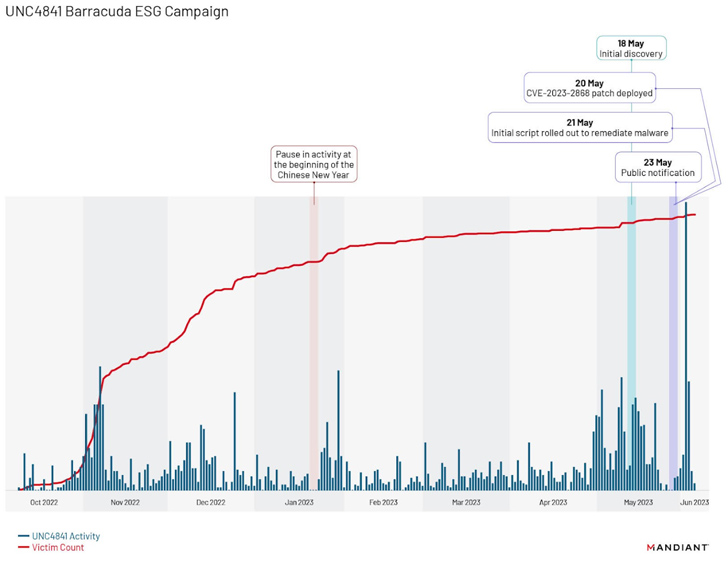
The earliest use of DEPTHCHARGE dates back again to May perhaps 30, 2023, basically times following Barracuda publicly disclosed the flaw. Mandiant mentioned it noticed the malware staying speedily deployed to a subset of targets, indicating a significant level of preparation and an try to persist in superior-price environments.
“It also suggests that regardless of this operation’s worldwide protection, it was not opportunistic, and that UNC4841 had suitable arranging and funding to foresee and put together for contingencies that could probably disrupt their access to target networks,” the company discussed.
About 2.64 percent of the complete compromised appliances are believed to have been contaminated with DEPTHCHARGE. This victimology spans U.S. and foreign government entities, as well as higher-tech and information and facts technology providers.
The 3rd malware pressure, also selectively shipped to targets, is FOXTROT, a C++ implant that is launched using a C-dependent program dubbed FOXGLOVE. Communicating through TCP, it arrives with options to seize keystrokes, run shell instructions, transfer data files, and set up a reverse shell.
What’s extra, FOXTROT shares overlaps with an open-supply rootkit known as Reptile, which has been thoroughly utilized by numerous Chinese hacking crews in modern months. This also includes UNC3886, a danger actor linked to the zero-working day exploitation of a now-patched medium-severity security flaw in the Fortinet FortiOS working program.

“FOXTROT and FOXGLOVE are also noteworthy in that they are the only malware family members observed becoming made use of by UNC4841 that ended up not specifically made for Barracuda ESGs,” Mandiant pointed out. “Dependent on performance, FOXTROT was very likely also meant to be deployed to other Linux-dependent devices inside a network to help lateral motion and credential theft.”
An additional element that can make FOXGLOVE and FOXTROT stand out is the point that they have been the most selectively deployed amongst all malware family members utilized by UNC4841, completely utilizing it to concentrate on govt or authorities-similar companies.
The adversarial collective has also been detected accomplishing internal reconnaissance and subsequent lateral movement steps within just a constrained quantity of victim environments. Much more than just one circumstance entailed using Microsoft Outlook Web Access (OWA) to try to log in to mailboxes for buyers in just the organizations.

As an alternative sort of distant access, the superior persistent menace (APT) actor produced accounts containing 4 randomly produced figures within the and so forth/passwd file on approximately five percent of the earlier impacted appliances.
UNC4841’s Chinese connections are even more bolstered by the infrastructure commonalities among the group and one more uncategorized cluster codenamed UNC2286, which, in convert, shares overlaps with other Chinese espionage strategies tracked as FamousSparrow and GhostEmperor.
The most up-to-date disclosure arrives versus the backdrop of the U.S. Federal Bureau of Investigation (FBI) urging impacted shoppers to switch their ESG appliances with immediate effect, citing ongoing risk.
“UNC4841 is a perfectly-resourced actor that has used a extensive array of malware and intent-developed tooling to empower their world wide espionage functions,” the company reported, calling out the danger actor’s ability to selectively deploy far more payloads to precise victim environments.
“Shared infrastructure and methods for anonymization are frequent amongst Chinese cyber espionage actors, as is shared tooling and probably malware improvement sources. It is probably that we will proceed to observe Chinese cyber espionage functions focusing on edge infrastructure with zero-working day vulnerabilities and the deployment of malware custom-made to specific equipment ecosystems.”
Uncovered this post fascinating? Stick to us on Twitter and LinkedIn to go through more exceptional information we write-up.
Some components of this post are sourced from:
thehackernews.com

 DarkGate Malware Activity Spikes as Developer Rents Out Malware to Affiliates
DarkGate Malware Activity Spikes as Developer Rents Out Malware to Affiliates