An “really subtle” Chinese-speaking highly developed persistent danger (APT) actor dubbed LuoYu has been observed working with a destructive Windows device termed WinDealer which is sent by usually means of person-on-the-facet attacks.
“This groundbreaking progress makes it possible for the actor to modify network targeted visitors in-transit to insert malicious payloads,” Russian cybersecurity business Kaspersky reported in a new report. “This sort of attacks are primarily unsafe and devastating mainly because they do not involve any conversation with the concentrate on to direct to a effective an infection.”
Regarded to be energetic considering that 2008, companies specific by LuoYu are predominantly foreign diplomatic corporations founded in China and members of the tutorial neighborhood as well as money, defense, logistics, and telecommunications corporations.

Protect your privacy by Mullvad VPN. Mullvad VPN is one of the famous brands in the security and privacy world. With Mullvad VPN you will not even be asked for your email address. No log policy, no data from you will be saved. Get your license key now from the official distributor of Mullvad with discount: SerialCart® (Limited Offer).
➤ Get Mullvad VPN with 12% Discount

LuoYu’s use of WinDealer was initial documented by Taiwanese cybersecurity company TeamT5 at the Japan Security Analyst Convention (JSAC) in January 2021. Subsequent attack campaigns have made use of the malware to target Japanese entities, with isolated bacterial infections reported in Austria, Germany, India, Russia, and the U.S.
Other applications that are component of the adversary’s malware arsenal incorporate PlugX and its successor ShadowPad, both of which have been utilized by a range of Chinese threat actors to empower their strategic objectives. On top of that, the actor is recognised to goal Linux, macOS, and Android products.
WinDealer, for its portion, has been delivered in the earlier by means of internet sites that act as watering holes and in the sort of trojanized applications masquerading as fast messaging and movie hosting companies like Tencent QQ and Youku.
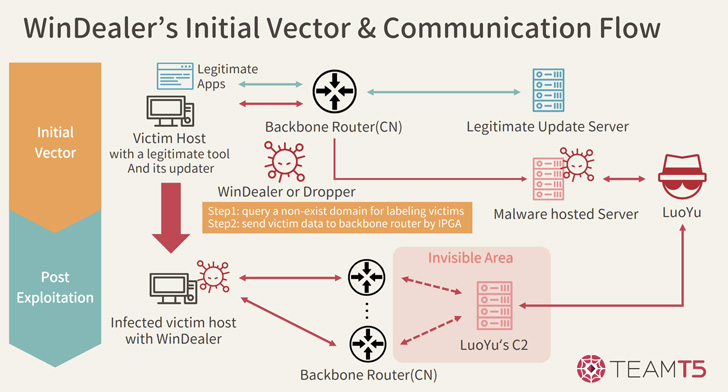
But the infection vector has since been traded for an additional distribution strategy that can make use of the automatic update mechanism of decide on authentic purposes to serve a compromised edition of the executable on “rare instances.”
WinDealer, a modular malware platform at its main, arrives with all the standard bells and whistles related with a backdoor, allowing for it to hoover sensitive facts, capture screenshots, and execute arbitrary commands.
But where by it also stands aside is its use of an IP-technology algorithm to choose a command-and-manage (C2) server to connect to at random from a pool of 48,000 IP addresses.
“The only way to explain these seemingly extremely hard network behaviors is by assuming the existence of a man-on-the-aspect attacker who is able to intercept all network visitors and even modify it if required,” the firm claimed.

A man-on-the-facet attack, similar to a male-in-the-middle attack, enables a rogue interloper to read through and inject arbitrary messages into a communications channel, but not modify or delete messages sent by other functions.
Such intrusions normally lender on strategically timing their messages these kinds of that the malicious reply that contains the attacker-provided knowledge is sent in reaction to a victim’s ask for for a web useful resource ahead of the real reaction from the server.
The point that the menace actor is equipped to command these kinds of a enormous selection of IP addresses could also reveal the hijacking of the update system linked with real apps to supply the WinDealer payload, Kaspersky pointed out.
“Guy-on-the-facet-attacks are particularly harmful as the only situation required to attack a machine is for it to be connected to the internet,” security researcher Suguru Ishimaru stated.
“No make any difference how the attack has been carried out, the only way for prospective victims to protect them selves is to continue being very vigilant and have strong security techniques, these kinds of as common antivirus scans, investigation of outbound network targeted visitors, and in depth logging to detect anomalies.”
Observed this post attention-grabbing? Follow THN on Facebook, Twitter and LinkedIn to read through additional unique content material we publish.
Some elements of this short article are sourced from:
thehackernews.com

 Old Hacks Die Hard: Ransomware, Social Engineering Top Verizon DBIR Threats – Again
Old Hacks Die Hard: Ransomware, Social Engineering Top Verizon DBIR Threats – Again