A Chinese state-sponsored menace activity team tracked as RedGolf has been attributed to the use of a custom made Windows and Linux backdoor identified as KEYPLUG.
“RedGolf is a notably prolific Chinese state-sponsored risk actor group that has probable been active for numerous years from a huge vary of industries globally,” Recorded Long term informed The Hacker Information.
“The group has shown the ability to rapidly weaponize recently reported vulnerabilities (e.g. Log4Shell and ProxyLogon) and has a history of building and applying a big assortment of custom made malware families.”

Protect and backup your data using AOMEI Backupper. AOMEI Backupper takes secure and encrypted backups from your Windows, hard drives or partitions. With AOMEI Backupper you will never be worried about loosing your data anymore.
Get AOMEI Backupper with 72% discount from an authorized distrinutor of AOMEI: SerialCart® (Limited Offer).
➤ Activate Your Coupon Code
The use of KEYPLUG by Chinese danger actors was 1st disclosed by Google-owned Manidant in March 2022 in attacks focusing on a number of U.S. point out federal government networks in between May possibly 2021 and February 2022.
Then in Oct 2022, Malwarebytes specific a independent set of attacks targeting govt entities in Sri Lanka in early August that leveraged a novel implant dubbed DBoxAgent to deploy KEYPLUG.
Equally these strategies had been attributed to Winnti (aka APT41, Barium, Bronze Atlas, or Wicked Panda), which Recorded Foreseeable future explained “intently overlaps” with RedGolf.
“We have not noticed unique victimology as section of the most up-to-date highlighted RedGolf activity,” Recorded Long term mentioned. “However, we imagine this activity is likely being executed for intelligence uses fairly than monetary obtain due to the overlaps with beforehand documented cyberespionage campaigns.”
The cybersecurity firm, in addition to detecting a cluster of KEYPLUG samples and operational infrastructure (codenamed GhostWolf) employed by the hacking team from at the very least 2021 to 2023, pointed out its use of other instruments like Cobalt Strike and PlugX.
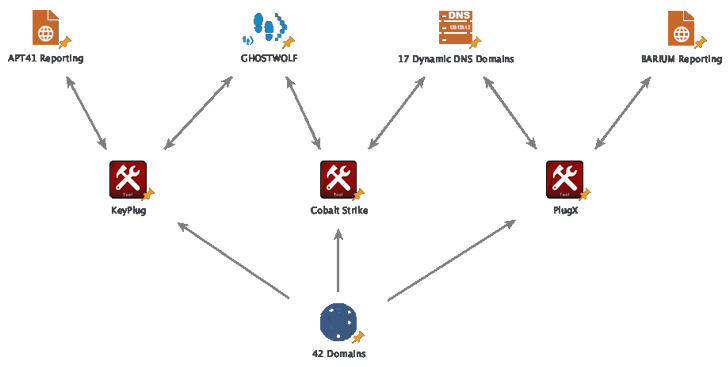
The GhostWolf infrastructure, for its element, is composed of 42 IP addresses that perform as KEYPLUG command-and-manage. The adversarial collective has also been noticed making use of a combination of both of those customarily registered domains and Dynamic DNS domains, usually showcasing a technology concept, to act as interaction factors for Cobalt Strike and PlugX.
“RedGolf will continue to exhibit a large operational tempo and speedily weaponize vulnerabilities in external-experiencing corporate appliances (VPNs, firewalls, mail servers, and many others.) to get initial obtain to target networks,” the corporation mentioned.
THN WEBINARBecome an Incident Response Pro!
Unlock the tricks to bulletproof incident reaction – Learn the 6-Section course of action with Asaf Perlman, Cynet’s IR Leader!
Will not Miss out on Out – Help you save Your Seat!
“On top of that, the team will possible keep on to adopt new tailor made malware people to incorporate to existing tooling this sort of as KEYPLUG.”
To protect towards RedGolf attacks, corporations are recommended to use patches regularly, watch entry to exterior experiencing network products, keep track of and block recognized command-and-manage infrastructure, and configure intrusion detection or avoidance programs to check for malware detections.
The conclusions come as Trend Micro disclosed that it discovered a lot more than 200 victims of Mustang Panda (aka Earth Preta) attacks as portion of a considerably-achieving cyber espionage effort and hard work orchestrated by different sub-teams since 2022.
A vast majority of the cyber strikes have been detected in Asia, followed by Africa, Europe, the Center East, Oceania, North The us, and South America.
“There are potent indications of intertwined conventional intelligence tradecraft and cyber assortment attempts, indicative of a hugely coordinated and sophisticated cyber espionage procedure,” Trend Micro claimed.
Found this write-up fascinating? Adhere to us on Twitter and LinkedIn to browse additional unique content material we put up.
Some pieces of this short article are sourced from:
thehackernews.com


 FDA Protects Medical Devices Against Cyber-Threats With New Measures
FDA Protects Medical Devices Against Cyber-Threats With New Measures